
Table of
Contents
 Table of Contents |
The collection management process is cyclic in
nature. As you use the process to satisfy some intelligence requirements,
you simultaneously use it to generate new requirements or reprioritize
existing ones.
How To Do It:
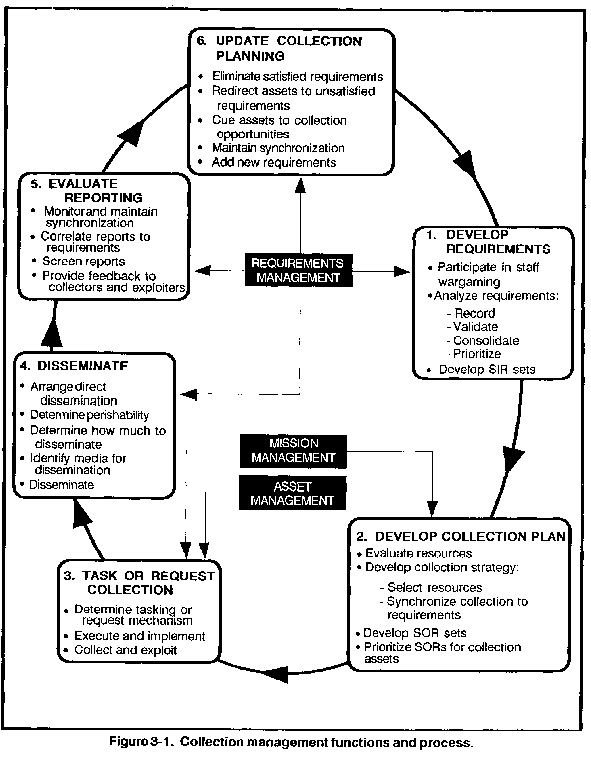
As shown in Figure 3-1,
each step of the collection management process consists of a series
of judgment decisions. Taken together, they form the "how
to" of collection management.
A Doctrinal Procedure:
Use the same procedural thought process shown
in Figure 3-1 regardless of echelon,
type operation, or time available. However, circumstances will
dictate the nature and amount of detail you will be able to develop
in the resulting products. For example:
Remember to always conduct every step. The time
required to execute these steps depends upon the tools you choose
to use and develop. If you are familiar with the capabilities
of your assets, for example, you may speed up the process by not
actually constructing asset evaluation worksheets. You will, however,
consider the capabilities of your assets against the collection
target before selecting them as part of your collection strategy.
What Is It?
Definition:
The identification, prioritization, and refinement
of uncertainties concerning the threat and the battlefield environment
that a command must resolve to accomplish its mission.
For Example:
After receiving taskings from division, participating
in staff wargaming, and coordinating with the commander, a brigade
S2 publishes the following list:
Desired End Effect:
A prioritized list of exactly WHAT needs to be
collected, precisely WHERE it needs to be collected, and WHEN
it needs to be collected and reported in order for a unit to conduct
operations as planned.
So What?
Success Results In:
Intelligence requirements that are synchronized
with the command's COA.
As collectors report, analysts receive the information
they need to develop intelligence that drives the commander's
decisions.
Consequences of Failure:
Analysts receive information that--
Participate In Staff Wargaming:
Wargaming:
Units generate intelligence requirements through
staff wargaming. Intelligence officers role play the enemy commander
using enemy COAs developed during the IPB process.
As the remainder of the staff "fights"
opposing COAs, the commander or his designated representative
identifies decisions to be made during the actual execution of
the mission. For each of these decisions, the staff identifies
the precise intelligence criteria required to trigger the decision.
For example: During a corps wargaming session
the G2, who is role-playing the enemy Army commander, commits
a forward detachment of regimental size to seize a bridgehead
over a major river at either bridge site #1 or #2.
The G3 responds by declaring: "Darn you,
if that happens we'll have to hit them with two attack helicopter
companies. We will also have to blow the bridge they're going
for; but we can leave the other intact."
After further discussion the G2 writes the following
notes, which the G3 and commander verify later:
The collection manager notes the requirement
for collection on the AAs to the bridges, as well as the bridges
themselves. He outlines a collection strategy that will ensure
early warning of a move toward the bridges and support employment
of the attack helicopters in the related engagement areas.
Collection Management Participation:
A collection management representative (normally
the requirements manager) should participate in the wargaming
session.
The CM representative determines whether the
normally available collection assets can acquire the appropriate
intelligence in a timely manner. If not, wargamers must plan contingencies
around the predicted lack of intelligence.
The CM representative ensures that each proposed
NAI can be covered by some sensor. If the command must rely on
non-organic sensors to cover the NAI, he ensures that the remainder
of the staff is aware of any risks and delays involved.
The commander will often designate certain decisions
as more critical than others. This will enable the collection
manager to appropriately prioritize requirements later in the
CM process.
If wargamers identify more decisions than available
collectors can support, the CM representative can prompt the commander
to prioritize the decisions.
Wargamers often discuss the specific intelligence
that will and will not support each decision. The details of this
discussion may not appear in the intelligence requirements and
SIRs sent to the CM section.
By sitting in on this discussion the collection
manager will be better able to evaluate the relevance of incoming
reports later in the CM process. The collection manager will also
be able to develop collection strategies with higher reliability.
By sitting in on the wargaming session the collection
manager will better understand the commander's intent and concept
of operation. This enables the collection manager to respond faster
to changes in operational priorities during battle.
Participating in staff wargaming allows the collection
manager to fully integrate the CM process into the decision making
process. As a result, he is better able to synchronize the command's
collection operations with the remainder of its operations.
For more information on intelligence support
to wargaming, see FM 34-130,
Appendix A. For a discussion on how to determine the precise intelligence
required for decisions, see Appendix D
of this manual.
Analyze Requirements:
To ensure the most effective use of collection
assets, first analyze each requirement to determine how best to
satisfy it. Sometimes this does not require collection activity.
Often, a newly received requirement can be satisfied by intelligence
in the data base or duplicates one that has already been processed.
Use the following steps to ensure that each requirement
is satisfied in the most efficient manner:
Record Requirements:
In addition to the set of intelligence requirements
produced during wargaming, you will receive intelligence requirements
from--
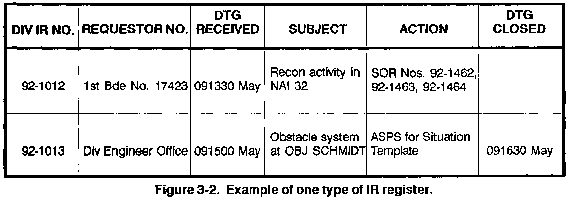
In order to track these requirements, along with
those of your own command, record each requirement as received.
Use this record to track each requirement from its receipt to
its eventual satisfaction. See Figure 3-2
for one example of a register used to record and track intelligence
requirements.
Validate Requirements:
After beginning an audit trail by recording each
requirement, validate requirements by considering--
Consolidate Requirements:
Since you receive requirements from several different
commands, you will often receive requirements which are similar
to those previously received. In particular, the specific request
for intelligence from subordinate units often duplicate the intelligence
requirements of their parent command.
Simplify the collection effort by merging similar
requirements. Normally, replace the more poorly written requirement
with the wording of the better justified or more specific requirement.
However, exercise caution to ensure that in merging requirements
you do not lose the intent of either of the original requirements.
Also ensure that when merging requirements, you
do not lose accountability of the replaced requirement. The audit
trail must allow you to match the satisfied requirement against
all requests for that intelligence; ensuring dissemination to
every requesting headquarters when the requirement is satisfied.
Prioritize Requirements:
After consolidation you will have a composite
list of intelligence requirements. Some of these requirements
are more important to mission success than others. Prioritize
the list. This enables you to focus assets on the most important
requirements, while economizing assets for less significant areas.
When prioritizing, do not automatically put specific
orders from senior headquarters on top of the list, your own command's
requirements in the middle, and specific requests for intelligence
from subordinates on the bottom. A subordinate command's specific
request may well be more important to the success of your command's
mission than all the other requirements. Likewise, a specific
order from a senior command may be ranked near the bottom of the
list.
Effective prioritization requires staying abreast
of the operation. When prioritizing consider--
Develop Specific Information
Requirement Sets:
What is it?
Identifying the sets of specific information
that will provide an answer to each intelligence requirement.
SIRs break requirements into smaller, more specific
questions which, when answered, can satisfy the larger intelligence
requirement. SIRs describe what information is required, where
on the battlefield it can be obtained, and when it is to be answered.
SIRs are as detailed as possible. To support mission management
and the development of SORs the requirements manager, normally
with the assistance of the ASPS, develops sets of SIRs for each
requirement.
For example: During wargaming a corps commander
tells the G2, "In order to commit our reserve I need to know
whether that tank division will turn east or west at Griffinheim."
The requirements manager refines this into the
intelligence requirement, "Will the 3d Tank Division enter
NAI 8 or NAI 9 on the evening of 5 March? (triggers corps reserve).
This intelligence requirement already contains
a reasonably detailed description of what the commander wants
to know, where to find the intelligence, and when the event is
expected to occur. However, the requirements manager needs to
supply the mission manager with more detail in order to support
his planning and the subsequent development of specific orders
and requests. Therefore, the requirements manager and the ASPS
develop the following set of SIRs, all designed to support the
same basic intelligence requirement:
How to do it:
Ideally, each intelligence requirement will contain
all the information the requirements manager and ASPS section
need to develop supporting SIRs. In such cases, the intelligence
requirement states the "where" and "when"
to collect; the requirements manager and ASPS need only refine
the "what to collect" into specific items of information.
If you receive requirements which do not contain
the information you need to establish the "where" and
"when to collect, coordinate with the originator to obtain
that information. The information you need should be contained
in the IPB products that helped generate the requirement.
The event template shows the location of' NAIs
on the battlefield and TPLs associated with each NAI. The event
matrix shows the threat activities, or indicators, to look
for in each NAI, and the timelines during which each NAI should
be active.
As the requirements manager develops SIR, he
should coordinate with the mission manager to get an understanding
of the types of SIRs and exact specificity required to support
his planning. A technique is to develop SIR sets while the mission
manager is developing the collection strategy for each requirement.
This process begins with identifying the activities
that will confirm the event specified in the intelligence requirement.
These activities, called indicators, are usually stated in general
terms such as "forward deployment of artillery."
The first step is to make each indicator more
specific by identifying the "where to collect, " tying
it to a specific point on the battlefield. For example, use a
specific NAI to replace the general idea of "forward"
in the indicator "forward deployment of artillery" and
rewrite it as "artillery deployed in NAI 12." If the
intelligence requirement is well written, it will contain the
NAI that allows you and the ASPS to do this.
Use a similar technique to specify the "when
to collect." If the intelligence requirement is well written,
it will contain the timelines needed to establish the "when
to collect. " If it does not, coordinate with the ASPS. Their
situation templates depicting the threat COA under consideration
and the graphics depicting the friendly scheme of maneuver should
provide the information needed to establish collection timelines
for the NAI in question.
Develop more detail in the "what to collect"
by identifying the specific information which supports the indicator.
For example, specific information which supports the indicator
"artillery deployed in NAI 12" might include--
Develop each indicator further by coordinating
with the ASPS to identify the specific types of equipment or other
"collectible" associated with each developing SIR.
For example, replace the generic "artillery
weapons" with specifics such as "M-109 or M-110 self-propelled
artillery systems" if that is what should be present within
the NAI. Similarly, replace "artillery associated communications"
with "the QUASIT data signal" if that is the type used
by the enemy unit in question. This helps asset managers to optimize
their collection capabilities against the target in question.
Establish the LTIOV by backwards planning the
timelines required to deliver the finished intelligence to the
requester. Ensure that the LTIOV will deliver the intelligence
at or before the DP it supports.
Because each intelligence requirement will generate
a number of indicators, which will in turn generate a number of
SIRs, finalize each SIR by labeling it with an identifier that
allows the requirements manager to trace it back to the original
intelligence requirement. A final SIR might be written as "SIR
2.12.7: Are there QUASIT data signals active in NAI 12 between
041200 and 060200 March? LTIOV: 060400 March."
Remember that indicators and SIRs are analytical
tools for the ASPS. Ensure that when the collector satisfies the
SIR, the analyst will have information that truly does indicate
enemy actions that will solve the original requirement.
Step 2. Develop Collection
Plan
What Is It?
Definition:
The integrated and synchronized plan that selects
the best collectors to cover each requirement. It is a graphic
representation of the collection strategy. This is the first step
in the CM process that involves mission management.
An example of one collection
planning problem:
The corps commander's first priority is detection
and tracking of the enemy's tank regiment, the principal counterattack
threat. The Corps is conducting the theater's main effort and
has radar service request priority during tonight's Joint STARS
mission. The mission manager decides to maximize Joint STARS wide
area surveillance capability to detect and track major armor movement.
He also plans to activate preplanned national system imagery problem
sets of key choke points (NAIs #6, #7, #8) along likely tank regiment
approaches. Additionally, he prioritizes collection requirements
for the corps MI brigade HUMINT company and the forward brigades
with responsibility for the same NAIs, with special emphasis on
enemy prisoners of war (EPWs) or refugees with knowledge of enemy
reconnaissance activity.
Desired End Effect:
A collection strategy and employment scheme that
will produce the intelligence required to effectively answer the
command's intelligence requirements.
So What?
Success Results in:
Synchronization of intelligence collection with
the command's COA through effective use of collection assets at
the right time and place on the battlefield.
Consequences of Failure:
The wrong collector wastes time trying to answer
a question beyond its capabilities.
A false picture of the target develops from use
of an inappropriate collector.
A true picture of the target arrives too late,
because you relied upon a collector with insufficient reporting
timeliness.
Collection is focused on an unimportant area
of the battlefield.
The commander is forced to assume unnecessary
risk.
How to do it:
Evaluate Resources:
Mission management takes prioritized requirements
and begins matching them with suitable collection and exploitation
assets using the following criteria:
Availability: Know the collectors and processors
available to you at your own echelon, and above and below. Know
their capabilities and how to access them. Aside from maintenance
and operator readiness issues, you have influence over the availability
of organic assets. For example, the corps collection manager will
alert the MI brigade to prepare for a surge in Guardrail Common
Sensor missions. In turn, the Brigade will regularly report aircraft
readiness, factoring in such variables as phase maintenance and
crew rest requirements.
Determine higher echelon and other service asset
availability by reviewing various scheduling mechanisms (for example,
the air tasking order or Peacetime Application of Reconnaissance
Programs (PARPRO) schedule). Airborne collectors often retain
a reserve capability to respond during crises. This quick reaction
capability provides an opportunity to request unscheduled collection
in support of a critical requirement.
HUMINT assets are not tied to traditional "schedules";
their availability is linked to geographic access, support relationships,
and workload.
Capability: This criteria is fairly straightforward
with electronic collection and exploitation systems. Capability
includes such things as--
Physical and threat environments impact greatly
upon collection system capability, both in terms of--
Determining HUMINT collector capability is often
a subjective process. Access to the target and reporting timeliness
may be key qualifiers.
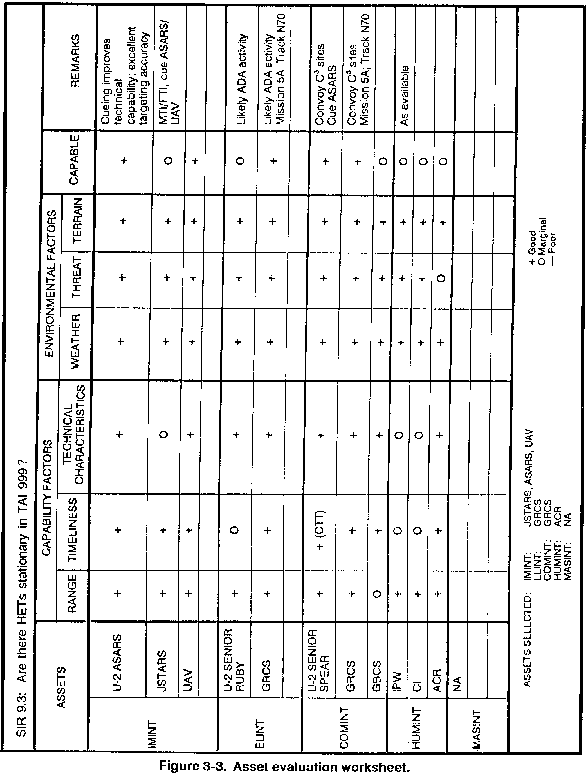
A tool that can help you work through the capability
evaluation is the asset evaluation worksheet (see Figure 3-3)
developed as part of the Joint-Service Tactical Exploitation of
National Systems (J-TENS) Manual. See Appendix C
for a capability quick reference guide.
Vulnerability: Evaluate the collector's vulnerability
to threat forces. Consider more than threat forces in the target
area. For example, the flight path of a QUICKFIX helicopter makes
its role as an intelligence collection system and high-value target
(HVT) obvious. Determine the threat's ability to locate, identify,
and destroy the collectors anywhere their collection mission might
take them.
Performance History: An experienced collection
manager knows the "work horses" upon which he relies
to meet the commander's intelligence requirements. Readiness rates,
responsiveness, and accuracy over time may raise one collector's
reliability y quotient. Certain sensors require confirmation,
especially if targeting is an issue.
For example, target selection standards may require
you to rely on systems capable of providing targeting accuracy,
such as Advanced Synthetic Aperture Radar System (ASARS), Joint
STARS, or UAV.
If experience shows that ASARS is often unavailable
because of local weather patterns, the experienced collection
manager considers this in evaluating the system's performance
history; perhaps leading to the selection of an alternate system.
Develop Collection Strategy:
After thorough study of availability, capability,
and performance history, the collection manager performs the following:
Select Resources: Plan to task organic
assets, request support from higher headquarters,
and recommend tasking to subordinate echelons. Organic
assets are usually more responsive and, as discussed above, you
may directly influence their availability. However, avoid relying
solely on your own resources if other systems are, based upon
your evaluation, more capable.
Each echelon has unique, organic intelligence
capabilities and the resultant hierarchy of task, request, or
recommend relates directly to the IS0S "push and pull"
concept of "seamlessness." EAC asset reporting "pushes"
intelligence down to corps. Corps collectors support the intelligence
requirements of division, brigade, and battalion. As we continue
to develop multiple subscriber processors that complement the
unique collectors, lower echelon units are increasingly capable
of "pulling" the information they need from higher headquarters.
Maximizing the "take" from those processors and the
collection systems that feed them results from effective exploitation
management.
Some processors that facilitate exploitation
include--
These systems receive, process, and exploit SIGINT
and imagery intelligence (IMINT) data from theater and national
level collectors. They also transmit processed data to the mobile
terminals using varied communications means. See Appendix C
for more information.
Some processors also allow the collection manager
direct access to collection systems for new taskings. For example,
given tasking authority during an ASARS or Joint STARS mission,
TRAC and the Joint STARS GSM terminal can communicate new requirements
to their respective collection platforms via their respective
interactive data links. See Step 3, Task or Request Collection,
for details on dynamic tasking.
In some cases, new collection tasking is not
the most efficient approach to intelligence requirement resolution.
Exploitation management allows you to "piggyback" on
existing collection by tasking your processors to "pull"
in the appropriate image or signals. For example:
A JTF requires multiple images of Shalimar Industrial
Complex to determine activity levels and defensive posture. The
supporting JIC knows that Shalimar is a daily Defense Intelligence
Agency (DIA) target of interest (TAI) and tasks the IMINT processor
to ensure priority receipt and exploitation of all frames covering
the complex.
The JIC does not generate a new collection requirement;
it uses the exploitation system to acquire intelligence already
available as a result of ongoing missions, saving considerable
time and energy. Simultaneously, the JIC submits a time-sensitive
collection requirement for screening and debriefing individuals
knowledgeable of the facility.
Similarly, a brigade S2 who knows that the division
is conducting UAV flights within his AI may tap into the downlink
on his own GSM at those times it operates over his NAIs.
Collection managers with access to these processors
and terminals must establish pertinence filters to ensure the
images or data received are of value to their commanders and analysts.
Indiscriminate "pulling" from these systems can overload
your analysts with too much irrelevant intelligence to process
effectively.
Key to collection strategy development are cueing,
redundancy, mix, and integration.
Cueing involves the use of one or more sensor
systems to provide data that directs collection by other systems.
For example, sweeping the battlefield electronically with wide-area
surveillance systems reveals activity that triggers direct collection
by a more accurate, pinpoint sensor system. Cueing maximizes the
efficient use of finite collection assets in support of multiple,
often competing, intelligence collection priorities.
Plan to create opportunities for cued collection
as part of your strategy. For example, you plan to use a low-level
HUMINT source 24 hours prior to UAV launch to confirm or deny
activity along a key corridor.
If the HUMINT source reports the absence of activity;
you may redirect the UAV to another mission or use it to confirm
the absence of activity, depending on the relative priority of
requirements.
If the HUMINT source reports significant activity
earlier than anticipated, you may accelerate the UAV launch sequence
to collect supporting detail or, instead, retask it to another
collection mission.
Cueing can also occur dynamically (outside the
collection strategy) as one system or echelon tips the other off
to an unexpected collection opportunity.
IEW collection systems also cue BOSs. For example:
These examples further illustrate the need for
synchronization among the BOS and for the collection manager's
active participation in the wargaming process. (See Step 1, Develop Requirements.)
Redundancy planning as part of collection strategy
development involves the use of several same-discipline assets
to cover the same target. Use redundant tasking against high priority
targets when the probability of success by any one system is low.
For example, if you focus several SIGINT collectors on a designated
emitter at different times, the probability of intercept improves,
even if the emitter operates intermittently. The chance of accurate
geolocation is also improved through the use of redundant collection
strategies.
Mix means planning for complementary coverage
by a combination of assets from multiple disciplines. Sensor mix
increases the probability of collection, reduces the risk of successful
enemy deception, can facilitate cueing, and provides more complete
reporting. For example, scouts report resupply activity within
a known assembly area; SIGINT intercept of the associated logistics
net provides unit identity, subordination, and indications of
future activity.
Integration is the resource management aspect
of collection strategy development. Barring a decision to use
redundant coverage for a critical target, attempt to integrate
new requirements into planned or ongoing missions. Integration
also helps avoid the common problem of under-tasking very capable
collectors. Examples of resource integration include--
After selecting the resources, execute the next
step in the strategy:
Synchronize Collection to Requirements: The RM
function develops SIR sets from the consolidated, validated, and
prioritized list of PIR and IR. The mission management function
uses SIRs to complete the collection strategy by associating each
requirement and its corresponding decision points and timelines.
Match each SIR against the intelligence requirement that it supports
to ensure that you fully understand the requirement. Starting
at the point in time that the commander requires intelligence
to effect a decision, backward plan to account for dissemination,
analysis, processing, collection, and tasking time.
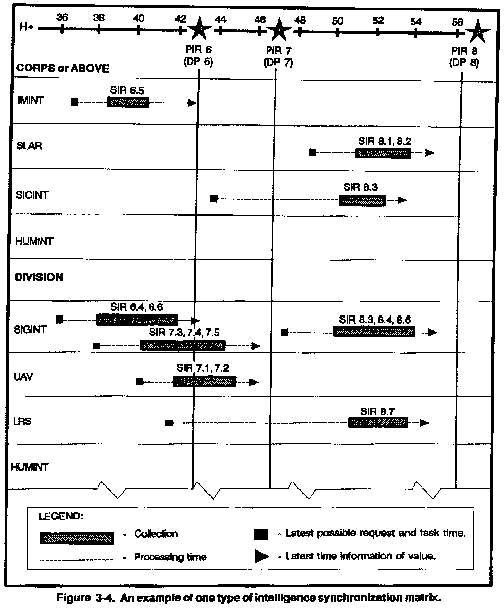
An effective tool used to link and synchronize
the collection strategy with the expected flow of the operation
it supports is the ISM (see Figure 3-4).
In addition to the LTIOV, determined by the prioritized requirements
and associated decision criteria, the matrix records NAIs from
the event template and reflects timelines of expected enemy activity
from the event template and the event matrix. The intelligence
synchronization matrix provides the basic structure for the more
detailed collection plan, which reflects the SOR assigned to selected
collectors for each intelligence requirement.
Develop SOR Sets:
The development of detailed SIR during the RM
function helps develop SOR sets during the MM function. You can
easily translate a well written SIR into an effective SOR by making
a directive vice inquisitive statement. Tailor the reporting criteria
to the collection capabilities of the asset tasked. For example:
Be specific; however, avoid overly restrictive
reporting guidelines. Allow your collectors the latitude to provide
information you and the analysts had not anticipated. Emphasis
or amplification tasking supplies the specifics required without
artificially restricting collector capability (see Figure 3-4).
Tailor the SOR to the selected collection system
or organization. For example, some imaging systems require a basic
encyclopedia (BE) number rather than a geographic or universal
transverse mercator (UTM) coordinate for target location. Most
Air Force airborne collection platforms recognize geographic coordinates
only. HUMINT collectors need to have specific timeliness, reporting,
and dissemination guidance. If your SOR are specific enough, they
can roll over into the actual tasking or request mechanism or
format.
Prioritize SORs for Collection
Assets:
Collection plans are complex, with multiple requirements
and collection assets. Each asset may have several SOR to which
it must respond.
For example, Corps requests TRACKWOLF support
to target high frequency (HF) communications associated with three
deployed Army headquarters. You require DF locational data for
each headquarters. You need to prioritize which headquarters is
most important (perhaps a center of gravity?) according to the
Corps operational concept.
Prioritization affects reporting as well as collection
procedures. To avoid the "first in, first out" approach
to reporting, especially if communications paths are limited,
specify which answers need to be transmitted first regardless
of when they were received.
Step 3. Task or Request
Collection
What is it?
Definition:
Implementation of the collection plan through
execution of system-specific tasking or request mechanisms.
An Example:
The collection manager uses the multiple assets
tasking message (MATM) format for IMINT taskings to pass immediate
tasking to the analysis and control element's (ACE's) remote Joint
STARS GSM.
Desired End Effect:
The collector receives properly formatted tasking
with all necessary data fields and executes the mission.
So What?
Success Results in:
Tasking that makes immediate sense to the collector.
Consequences of Failure:
Loss of synchronization due to unnecessary delay
in processing the task for collection. At worst, you miss the
tasking timeline for an EAC airborne sensor or your requirement
is rejected outright.
Collector focuses on the wrong priorities through
misunderstanding.
How to do it:
Determine Tasking or Request
Mechanism:
There are various tasking documents used to levy
intelligence requirements on collection agencies. Some tasking
mechanisms are theater or system unique. The J-TENS and various
Defense Intelligence Agency Manuals (DIAMs) specify procedures
and formats for requesting support from EAC and national systems
or agencies.
JCS Publication 6-04
establishes request and response formats, such as requests for
information (RI) and response to a request for information (RRI).
The IEW Character-Oriented Message Catalog (COMCAT) contains the
MATAM and Exploitation Requirement (ER) among other standard formats.
The intelligence annex to the operations order
(OPORD) is a standardized tasking vehicle at echelons corps and
below (ECB). Paragraph 3 of the intelligence annex, Intelligence
Acquisition Tasks, implements the collection plan. It contains
a complete list of current orders and RI. Use an appendix to the
annex to relay lengthy intelligence tasking orders and requests.
At brigade or battalion levels this appendix often takes the form
of R&S overlays and plans.
Another effective technique is to coordinate
with the G3 or S3 to list specific orders for the collection of
intelligence in paragraph 3, Execution, of the command's OPORD.
Supporting details are then included in the intelligence annex
and additional appendixes, as required.
The intelligence annex to joint operations plans
(OPLANs) contains paragraphs for collection tasks directed to
each intelligence discipline. These paragraphs also provide guidance
for reporting and dissemination of intelligence. Additionally,
there are separate appendixes for SIGINT, counterintelligence
(CI), and HUMINT operations.
Determination of the most efficient task or request
mechanism depends upon system or agency requirements (some collectors
will only recognize and react to one format) and the urgency of
the task. For example, you may issue immediate tasking in response
to a cue via voice. Quick reaction capability missions often launch
with only telephonic tasking from the collection manager; fragmentary
orders (FRAGOs) over the radio often redirect the scout platoon
to new or changed missions.
Execute and Implement:
The tasking process provides the selected unit
with a specific, prioritized requirement. Planning and conduct
of the collection operation fall within the AM functional area
of responsibility (AOR). Following the appropriate tasking chains
established by unit standing operating procedures (SOPs) or "how-to"
manuals (J-TENS) limits the confusion caused by duplicate or misrouted
tasking.
At the joint level, in addition to system or
agency specific tasking (an SOR developed for a specific collector),
the theater J2 issues a statement of intelligence interest
(SII) for all theater units. The SII provides the "collection
intent" for a specified period of time, ensuring collective
comprehension of collection priorities in support of theater operations.
SII update is the first function of joint-level collection RM.
In addition to SII, division and corps collection
managers use the collection emphasis message (see Figure 3-5).
It is the IEW synchronization matrix in narrative format. You
can broadcast your collection strategy to higher, lower, and adjacent
units; collectors; and exploiters in addition to providing SORs.
The primary benefit of communicating "collection
intent" is the "big picture" perspective it provides
organizations which may be otherwise isolated from your planning
process. An informed collector can often amplify reporting to
provide an answer that goes beyond the immediate question. While
the report stops short of analysis, it refines raw information
and may facilitate cueing.
Related to cueing is dynamic retasking.
The ISOS technological revolution continues to develop and field
collection systems that truly report in NRT. Joint STARS, UAV,
Guardrail Common Sensor (GRCS), and ASARS with their respective
terminals (GSM, intelligence. processing facility [IPF], TRAC)
bring the battle home fast enough to effect new collection operations
almost simultaneously.
Interactive data links make these systems and
their capabilities immediately available to the collection manager.
Dynamic retasking may include new flight orbits or tracks in addition
to new requirements and coverage areas; this requires coordination
with the airspace manager as well as the asset manager. The following
scenario illustrates dynamic retasking:
The PARPRO schedule calls for a Corps GRCS mission
and theater U2 flight. GRCS aircraft flying in a northern orbit
report intercept of regimental units preparing to conduct a river-crossing
in a major training area. River-crossing operations are a high
priority on the SII. The IPF notifies the corps collection manager.
The collection manager contacts TRAC to check
status of the U2 mission. It is currently flying the southern
loop of its track and reporting minimal activity. The collection
manager coordinates with the theater's collection manager to arrange
retasting of the U2. The theater collection manager directs TRAC
to implement an adjusted navigation plan to optimize both SIGINT
and ASARS coverage of the river-crossing site.

TRAC passes the new navigation plan and adjusted
ASARS target deck to the U2 via its datalink. Within minutes of
receipt, the aircraft is on the new, northern track collecting
against the target area. Increased SIGINT collection and ASARS
images of pontoon bridging operations combine to give the corps
(and other intelligence users in theater) exceptional coverage
of a priority collection requirement.
While modern technology offers greater opportunities
for dynamic retasking, it also offers problems in delineating
the exact limits of the CM functions. Using a Joint STARS GSM
example, the CM directly tasks through the GSM remote workstation
in the ACE. The GSM directly interfaces with the airborne platform
via the surveillance and control data link. His corps has Radar
Service Request priority, giving him the ability to direct the
radar coverage of the Joint STARS, blurring the distinction between
MM and AM. In most cases, however, you task or direct collection
requirements to an agency or military command with AM authority
rather than to a specific collector. Within the corps and division
ACE, the MI brigade or battalion retains AM authority.
Collect and Exploit:
This final sub-function of Step 3, Task or Request Collection,
belongs to the asset manager for planning purposes and to
the collection and exploitation systems themselves for execution.
The final result is the production of information and intelligence
that leads to the sat is faction of the initial intelligence requirements.
In addition to providing reports on the results
of their collection operations, asset managers report on the status
and availability of their collection systems. This ensures that
the collection manager is able to make efficient use of the command's
intelligence collection capabilities as he continually updates
and refines the collection plan.
The echelon manuals (FMs 34-10,
34-25, and 34-80)
address MI operations in detail. System handbooks and TTP manuals
cover the "how to" aspect of collection and exploitation.
What Is It?
Definition:
The delivery of intelligence information to users
who need it.
Two Examples:
While writing an SOR to support the division's
targeting plan, the mission manager specifies direct dissemination
of results to the FSE and targeting cell.
The collection manager receives two messages
from the division's MI battalion.
The first is an information copy of a direct
response to an SOR. The collection manager notes that the information
has already been sent directly to the original requestor. While
closing out the requirement in his journal, the collection manager
checks to determine if the report will satisfy any other open
requests. Discovering that the report will partially satisfy an
unrelated request by the 1st Brigade, the collection manager coordinates
a retransmission of the report to the 1st Brigade.
Although not in direct response to an SOR, the
second report satisfies a recently received request for intelligence
from the aviation battalion. Since the report's classification
level exceeds the classification level of the aviation battalion's
communication system, the collect ion manager sanitizes the report
and, after coordinating release with the special security officer
(SSO), arranges for its transmission to the aviation battalion.
Desired End Effect:
Intelligence flows directly from collectors and
processors to requesters.
All intelligence users receive, in a timely manner,
the same information they would "pull" if they had the
time and resources to inspect all incoming information.
So What?
Success Results in:
Any unit that might act or consider acting upon
a piece of information will have the opportunity to do so.
The collection manager is sure that all units
to whom the information was passed actually received it.
Consequences of Failure:
Information will "stovepipe" into individual
intelligence data bases. Units that would otherwise act upon the
information will not be aware of its existence.
Information not relevant to a command's intelligence
needs will slow the processing and dissemination of more critical
information.
How to Do it:
Arrange for Direct Dissemination:
Getting intelligence to the requester as soon
as possible is key to successful CM operations. Whenever possible,
write into the SOR the requirement for direct dissemination of
intelligence to the original requester. Include the required coordinating
information such as call signs, frequencies, and routing addresses.
Direct dissemination is especially important
for intelligence that supports targeting efforts. Whenever possible,
arrange for direct dissemination of targeting intelligence to
the FSE and targeting cells.
Even with direct dissemination, you must arrange
a system that allows you to track the status of each request.
Information copies of reports already provided directly to the
original requester is one technique.
Sometimes direct dissemination is impossible
due to communications system limitations or the classification
level of the intelligence. Using the steps which follow below,
arrange for dissemination that is as direct as possible. Since
information already disseminated directly to requestors can often
satisfy other requests, also apply the following procedures to
"information copies."
Determine Perishability:
Determining the time sensitivity of each report
allows you to make decisions about the best means of dissemination.
Evaluating perishability requires you to stay abreast of the current
and developing situation. Continuous coordination is essential
with the ASPS, the targeting cell, and the operations staff.
Identify Users:
Check the report against outstanding requirements
to determine who requested the information. Ideally, this information
is included in the report by way of a cross-reference to the SOR
that generated the collection.
Check to determine if the report satisfies, completely
or partially, the requirements of other users. Often a report
contains information that helps to satisfy other requests. Since
the collector is usually unaware of the needs of other users,
he is not likely to disseminate information to anyone not specified
in the original SOR. Establishing a cross-reference system for
each SOR early in the requirements development process helps identify
requirements that support each other in this manner.
Another technique is to conduct "hindsight
wargaming. " This technique is useful when determining the
recipients of "unanticipated" intelligence. In this
technique, the collection manager determines--
Ask yourself the following questions:
Determine How Much to Disseminate:
After determining WHO to send each report to,
determine HOW MUCH of the report each user requires.
First, make sure that compartmented information
is not disseminated to users who are only authorized collateral
information. Legal restrictions may also prohibit the dissemination
of information to allied or coalition forces. This is especially
true during operations other than war where political considerations
may dominate collection operations.
Today's automation and communications technology
will tempt you to try to send everything to everybody; resist
the temptation. Competition for a limited number of communications
trunks will force you to prioritize the dissemination schedule
anyway. Additionally, pertinence filters at other headquarters
will eliminate those elements of information that you should not
have sent in the first place.
To determine how much information to send to
each user, employ the same analytical techniques described above
in "Identify Users." Evaluate each element of reported
information against the decisions, requirements, and supporting
SIRs and SORs for the identified consumer. Disseminate each "block"
of intelligence accordingly.
Identify Media for Dissemination:
Voice, Graphics, and Text Dissemination: When
disseminating relatively small amounts of information, use a combination
of voice, graphics, and text deliveries. Each of these means has
advantages and disadvantages:
Voice is most useful in situations where speed
in the transmission of a small amount of information is critical.
It obtains instant feedback and acknowledgement, allowing for
resolution of misunderstandings or ambiguity. On the other hand,
when passing large amounts of information, voice systems are slow
and prone to error.
Graphics and Text dissemination is ideal for
lengthy messages, but can sometimes make information too subtle,
ambiguous, and confusing.
When there is an option, use the graphic solution
for information on disposition, composition, and strength; use
text for the other order of battle (OB) factors.
The optimal mix is to send the graphics or text
immediately with a notice that a follow-up voice conference will
follow. This allows for verification of receipt and gives an opportunity
for recipients to resolve any questions or ambiguities.
Data Base Handling:
Automated data bases are ideal for handling large
amounts of data. While the collection manager rarely manages the
data base, he will have complete access to it via a local area
network (LAN).
This enables you to transfer incoming digital
information straight into the data base, thus ensuring instant
dissemination within the command's intelligence section.
The LAN also enables you to immediately satisfy
some intelligence requests. Recall that during the Develop
Requirements step, the requirements manager checks immediately
available data bases before sending SIRs to the mission manager.
The LAN enables the requirements manager to conduct instant checks
of the local data base. For example:
Disseminate:
Techniques:
For voice communications, use a radio net call
or a conference call to transmit broadcast or limited broadcast
items. Point-to-point communication is best for single distribution
items.
Deal with graphics and text dissemination as
per voice communications. The distribution list determines whether
you use broadcast, limited broadcast, or point-to-point techniques.
First try to disseminate graphics and text using
file transfers between two automated systems using normal communications
trunks between moderns. Failing this, try a facsimile transmission.
In terms of time required, a messenger with hard
copy is least desirable. However, if the messenger is well briefed,
this technique can be effective in terms of user understanding.
Considerations:
Use the precedence coding system (for example,
FLASH, PRIORITY) but be careful not to deflate the value of the
highest precedence codes.
Ensure that the entire section is proficient
in terms of operating automated systems and familiarity with message
formats.
Answer questions about accuracy, source, and
completeness that arise during dissemination. However, defer requests
for the significance of intelligence to the ASPS.
When disseminating information, "push"
items of essential information to concerned users and make them
aware of what else is available. This enables users to "pull"
additional information from the CM system.
Develop Audit Trail:
You must know who has received what information.
This optimizes dissemination by ensuring that everyone who requires
information actually receives it. It is not uncommon for a concerned
user not to receive information, even though the requirements
manager arranged for direct dissemination and the collector has
sent the information. This problem arises due to reasons such
as missed broadcasts and incorrect call signs.
Audit trails further optimize dissemination by
ensuring that concerned users receive each report only once. It
is not uncommon for a user to receive the same report multiple
times. Often this leads to false "confirmation" of a
report which is only "confirming" itself.
A common technique is to provide spaces on the
collection plan for "messages received that satisfy this
SOR:" and "messages sent to:". This enables the
requirements manager to record directly onto the collection plan.
A disadvantage to this technique is that it is difficult to track
messages chronologically (for example, "give me all the messages
that came in yesterday morning").
Another technique is to develop a matrix separate
from the collection plan, with "time received" and "sent
to" on one axis, and "SORs" on the other axis.
Another technique is to annotate the dissemination list directly
into the Remarks section of each message.
A collection and dissemination journal is a simple
technique to track who has seen what messages. A disadvantage
of this technique is that, without automation, it is difficult
to efficiently link journal entries to the requirements numbering
system.
This is an area where automation is especially
useful. Relational data bases and automated journals allow complete
and thorough cross-indexing, solving many of the problems collection
managers usually experience in relating requirements to reports
and tracking dissemination.
What Is It?
Definition:
Determines how well the system is satisfying
the command's intelligence requirements.
An Example:
A requirements manager in a corps ACE receives
two reports from the Aerial Exploitation Battalion. He determines
that--
Desired End Effect:
All SORs are fully satisfied in a timely manner,
keeping the intelligence system fully synchronized.
The collection manager knows the status of each
requirement.
So What?
Success Results in:
Analysts receive enough information to solve
intelligence requirements in a timely manner. This enables them
to deliver intelligence that supports the commander's decisions
in time to keep the operation synchronized.
Consequences of Failure:
Asset managers will think they satisfied an SOR
when they have not.
Analysts will be waiting for information that
will not come, denying or delaying intelligence the commander
needs.
Analysts will have to support the commander's
decisions with their best guess rather than with confirmed intelligence.
How to Do it:
Monitor and Maintain Synchronization:
Track the flow of the operation against the intelligence
synchronization matrix. Prompt asset managers and collectors,
as necessary, to keep their reporting synchronized with the operation
and the commander's needs.
The operation will seldom progress on the timelines
assumed during planning and staff wargaming. Watch for changes
in tempo that require changes in reporting times (LTIOV). Coordinate
any changes with all parties concerned, especially the asset managers.
It is also very likely that the staff's assumptions
about threat COAs will not prove entirely correct. The usual result
is a change in intelligence requirements as well as adjustments
to the time lines. The staff usually initiates abbreviated versions
of the IPB and decision making processes to accommodate the changes
in their assumptions. Be prepared to update collection planning
as a result.
Not all intelligence will flow through you; many
collectors will report directly to users such as FSEs. Monitoring
synchronization and evaluating reporting require you to establish
some system to evaluate all reports, including those that go directly
from the collector to the user. Set up a system that allows you
to monitor synchronization and evaluate how well the intelligence
system is meeting requirements without unduly delaying intelligence
dissemination.
Correlate Reports to Requirements:
Identify the original SOR and requirement that
the reported information satisfies. This allows you to determine
which SORs have been satisfied and which require more collection.
This is difficult to perform since--
During the development of requirements, develop
a numbering system that enables you to conduct quick audit trails
linking requirements to SORs. For example, "SOR 8-h-2"
might be the second SOR developed for "SIR-h" of "IR-8."
Remember that all intelligence requirements should already be
linked one-for-one to operational decisions.
Insist that asset managers tag all of their reports
with the numbers of the SORs they satisfy.
If an asset establishes its own numbering system,
insist that reports provide a key that relates the reporting asset's
internal numbers to the SOR number.
Develop templates that will enable. you to quickly
match incoming reports to outstanding SOR. For example:
Screen Reports:
After reports have been correlated and tagged
to the appropriate SOR, determine whether the SOR has been satisfied.
Screen each report for--
If the report fully satisfies the SOR, make the
appropriate entry in the audit trail or register of intelligence
requirements and disseminate the final intelligence to the requestor.
Coordinate with the requestor to ensure that the requestor also
considers the requirement satisfied.
If the report only partially satisfies the SOR,
annotate in the audit trail or registers what has been accomplished
and what remains to be done.
If the report suggests an opportunity to cue
other assets, take immediate action to do so and record any new
requirements into the collection plan and audit trail.
Pay particular attention to reports that state
simply "nothing significant to report." Sometimes these
reports intend to report that collection occurred and that no
activity satisfying the SOR was observed. This may be a significant
indicator in itself. On the other hand, "nothing significant
to report" may indicate collection did not occur. This has
a different significance, particularly to the collection manager,
and is by no means a reliable indicator of the absence of activity.
Provide Feedback to Collectors
and Exploiters:
After determining how well the reported information
satisfies SORs, inform the asset managers of the concerned collectors
and exploiters.
Step 6. Update Collection
Planning
What Is It?
Definition:
The adjustment of the overall collection plan
to keep intelligence synchronized and optimize collection and
exploitation capability as the current situation changes.
An Example:
An analyst notifies the requirements manager
that the ASPS solved IR-12 through analysis of previously submitted
SORs.
When the requirements manager reviews the collection
plan, he sees that he already relieved collectors of three SORs
associated with IR-12. However, five SORs remain outstanding with
corps and the division's MI Battalion. The requirements manager
relieves the MI Battalion from their two SORs and withdraws the
other three SORs from the division's request list at corps.
While updating himself on the current situation,
the requirements manager notices that the operation appears to
be progressing more rapidly than anticipated. He confers with
the ASPS and G2/G3 Operations and determines that he will have
to update the LTIOV for several of his SORs in order to keep the
intelligence system synchronized with the operation. He coordinates
with the ASPS to make the needed changes to the event templates
and matrices and then uses them as a basis for changing outstanding
SORs.
Desired End Effect:
SORs are updated to keep intelligence synchronized
with the operation. Collectors and exploiters work only on SORs
for unsatisfied requirements.
So What?
Success Results In:
Consequences of Failure:
Asset managers waste resources collecting information
that will not influence the course of the battle.
How to Do it:
Eliminate Satisfied Requirements:
During the "Evaluate Reporting" step
of the CM process you eliminate SORs that have been satisfied.
In this step, eliminate SORs that are overtaken by events, even
if unsatisfied. This requires continuous coordination with the
agency that generated the original requirement. For example, a
division requirements manager would coordinate with--
When the originating agency declares an SOR satisfied,
eliminate the requirement from the collection plan and update
any other logs and records.
Redirect Assets to Unsatisfied
Requirements:
Requirements can be satisfied by the collector
to which they were tasked or as a result of collection success
elsewhere on the battlefield. Hence, for limited times, an asset
manager may have collection capability in excess of his taskings.
The purpose of this step is to make best use of this "excess"
capability.
After eliminating satisfied requirements from
the collection plan, reevaluate each collection asset for excess
capability. Focus the excess collection capability on the most
important of the remaining unsatisfied requirements. This enables
you to compensate for--
When redirecting assets, consider--
In general, minimize excess capability and maximize
support to the most important requirements--new or old.
Cue Assets to Collection
Opportunities:
Recall that in previous steps the requirements
manager looked to create and exploit cueing opportunities. This
is where the requirements manager and mission manager redirected
an asset not because of excess capability, but as the result of
cross-cueing or because of the opportunity that an intelligence
report might generate.
The requirements manager and mission manager
execute the same procedure at this stage in the process. The primary
difference is that they are now responding to results of analysis,
rather than combat information.
When the requirements manager receives the results
of analysis, he consults the mission manager. The mission manager
reevaluates his original collection strategy based upon the new
intelligence. In particular, he looks for opportunities to improve
collection strategies, Once identified, the mission manager retasks
collection assets appropriately. For example:
A division ASPS informs the collection management
and dissemination (CM&D) section that they have unexpectedly
deduced the location of a second echelon regiment's CP (to within
1,000 meters) through analysis of Joint STARS moving target indicators
and synthetic aperture radar imagery.
The mission manager's original strategy for locating
this headquarters was to use Guardrail Common Sensor.
Since this CP is a critical HPT, the mission
manager focuses on refining the locational accuracy to meet target
selection standards. He evaluates the likelihood of the Guardrail
Common Sensor providing more accurate locational data against
the capabilities of other systems.
He decides to divert an ongoing UAV mission from
a lower priority requirement to conduct reconnaissance on the
1,000 meter circle that the ASPS identified. He issues the necessary
orders to the asset manager and then helps coordinate the changed
flight track with the division's airspace manager.
After the UAV identifies the precise location
of the CP, the mission manager withdraws the corresponding SOR
from the corps requirements manager. The corps mission manager
then relieves the MI Brigade (as the asset manager) of the SOR,
making them available for additional taskings.
Cueing opportunities, whether prompted through
combat information or analysis, allow you to satisfy requirements
more efficiently than previously planned through collection strategies.
Maintain Synchronization:
The timelines associated with each decision point,
which are used as the basis for establishing the LTIOV, are only
estimates. As planning or execution of the command's COA progress,
these estimated timelines are refined. You must stay alert to
the need for changes in the collection plan that result from these
refinements. These are usually changes to the LTIOV but sometimes
also involve other changes.
As the need for changes becomes apparent, coordinate
with the ASPS and G2 sections to update the IPB products needed
to refine the collection plan. Depending on the situation, this
may be as simple as updating the timelines on the situation templates,
event templates, and event mat rices. It may also require that
these products be completely redone.
Add New Requirements:
As planning or execution of a COA evolves and
as the threat situation develops, commanders will generate new
intelligence requirements. This prompts the re-initiation of the
CM process.
Prioritize the new requirements against the old
rather than simply adding them to the existing list. Do not simply
discount previous requirements; some may still be valid.
Reinitiate the CM process, consolidating new requirements with existing requirements which remain valid.