The Workshop on Information Warfare and Deterrence was held at the National Defense University as the sixth in a series sponsored by the Directorate of Advanced Concepts, Technologies, and Information Strategies (ACTIS). The topic arose both from (1) issues that surfaced in earlier workshops on subjects as diverse as Coalition Command and Control (C2), Technologies and Operations Other Than War (OOTW), and Command Arrangements for Peace Operations; and (2) interests expressed by ACTIS sponsors in the Joint Staff (J-6) and the Office of the Secretary of Defense, Assistant Secretary of Defense for Command, Control, Communications and Intelligence (ASD/C3I).
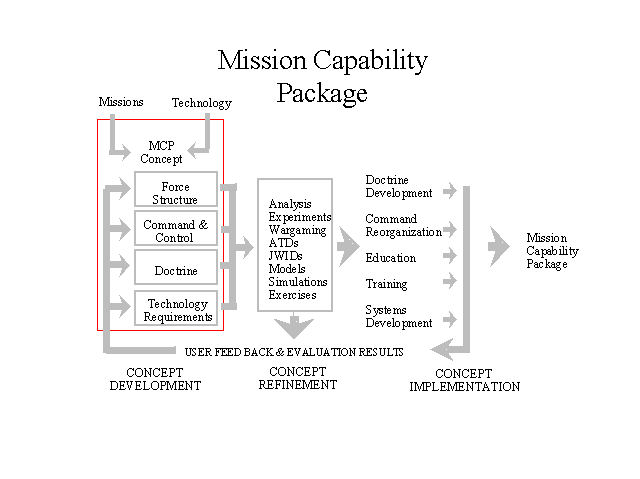
As with past ACTIS workshops, this one brought together senior analysts and technical experts, as well as active military leaders and action officers with operational responsibilities in the affected areas, for a non-attribution discussion working toward consensus or clear articulation of alternatives and their consequences. The list of attendees is included as Appendix A. The overall goal of the workshop series is to conceptualize and develop Mission Capability Packages (MCPs) that will support effective decision making and command and control in arenas where DoD has significant responsibilities. As Figure 1 illustrates, MCPs are coherent blends of doctrine, command organization, education, training, systems, and force structure that increase the likelihood of mission accomplishment across a range of anticipated situations and threats. Workshops are a beginning point for MCPs, suggesting novel concepts for later revision and analysis. As this process develops, the MCP is refined and its implications become better understood until an implementable concept emerges which can be passed from the research and development community to the practical world of implementation and action.

When exploring new or relatively new concepts like the relationship between IW and deterrence, analysts can be fairly certain that outcomes will likely be different than expectations. With this in mind the workshop sought to bound the initial explorations to those that might logically be achieved in a two-day effort. The workshop focused on three principal issues:
This workshop was conducted at the Secret level (except for one unclassified discussion of media war). Being restricted to classification levels no higher than Secret inhibited discussion of some topics largely by preventing discussion of particular systems and examples. However, the participants were still able to engage in a rich give-and-take and achieved a high degree of candor. A series of more focused roundtables (smaller working groups with selected expertise) is planned to follow up on significant issues left unresolved or where more sensitive issues need to be considered. Evidence Based Research, Inc. served as workshop organizer and rapporteur for the discussions.
On one level, deterrence and information warfare are well matched. Both belong to the world of robust ideas with broad implications. Both are highly relevant to the post-Cold War era in which conflict has been transformed from bipolar global structures to multi-sided, local and regional contests in which the military element is a crucial part of, but not the driving force for, competition and conflict. On the other hand, the two topics can be seen as orders of magnitude apart. IW is a huge domain, ranging from media wars to electronic combat and from economic competition to strategic conflict waged against civilian populations. Deterrence is actually a narrow topic that only applies when a set of quite restrictive assumptions apply. Not surprisingly, therefore, the workshop participants found the relationship between the two concepts to be spottyùhighly relevant on some topics, marginally so on others, and not at all relevant in many areas.
Many of our common notions of deterrence arise from the recently concluded Cold War. Strategic deterrence was equated with deterring both a Soviet invasion of Western Europe or a first strike on the United States, by the assured ability to reply with a devastating nuclear attack on the Soviet UnionÆs homeland. The workshop participants were well aware that most ôdeterrence theoryö is largely a product of that Cold War era. This suggests that those whose experience is from that era may bring extraneous concepts or baggage to the topic. Hence, they also heavily agreed that deterrence applications outside the nuclear war arena must be thought through carefully and should be exposed to domain experts from the appropriate arenas before they are considered mature.
Throughout history the primary form of deterrence has been defenses. These defenses have been both passive and active. Passive defenses include fortifications, moats and natural features such as rivers, oceans and high ground, and serve to deter by making attacks more difficult and costly. Active defenses and their ability to deter can best be summed up by the quotation frequently attributed to President Theodore Roosevelt: "Speak softly and carry a big stick." In the aggregate, this involves military defense forces.
Military capability or force is obviously not the only way to deter. For example, economic self-interest may deter. Just as an employee is restrained from insulting his employer or a businessman from annoying his customer, nations may be restrained from some information adventures either by the direct cost of the adventure or by the harm to future trade and other economic activity that may result. Building economic interdependency can therefore be considered as a form of deterrence. Likewise, information actions and interdependency might also be a kind of deterrence.
In any sphere, the retaliatory capability need not be real; but it must be perceived as real. Conversely, capability to deter may be insufficient if the adverse party is unaware of the capability or is not persuaded that the capability might be used. Military examples include the Strategic Defense Initiative as deterrence through perception management, and the reverse, when the perception of U.S. military might did not deter Iraq's 1990 invasion of Kuwait. Saddam Hussein either underestimated our power or our willingness to use that power.
The workshop readily reached consensus on a basic definition of deterrence as "prevention or discouragement, by fear or doubt, from acting." Clearly this definition implies an actor and a target. Moreover, the group also agreed on a simple set of conditions necessary for successful deterrence. These were seen as:
The simple, but crucial, step of defining what is encompassed by the term "information" is all too often ignored by those who write about its importance and its future. Appendix B is a study of the information dominance concept that was included as read-ahead material for workshop participants. It examines the hierarchy of information and the relationships of information interactions and the players who function in the arenas of interaction. It further suggests that what is commonly understood as "information warfare" might be too narrow a focus that ignores other significant information interactions across and through the full scope of human activity. Appendix C (also read-ahead material) addresses information warfare from perhaps the less theoretical and more practical viewpoint of a professional military practitioner. In spite of the contrasting approaches, both papers strongly assert that what we call information warfare today goes well beyond mere military interactions.
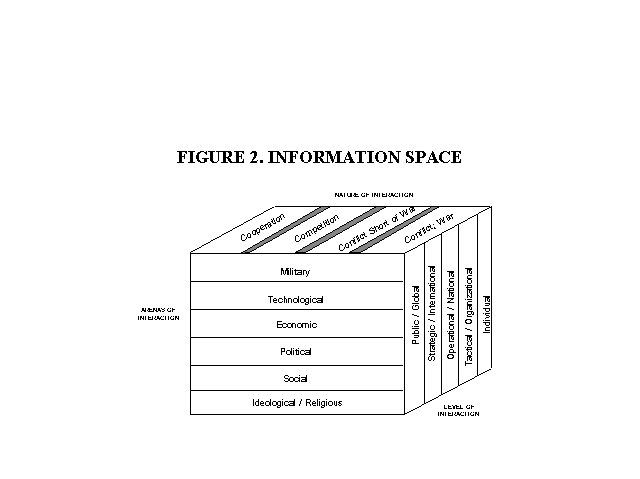
As Figure 2 illustrates, three relatively independent dimensions were required to capture and describe the information warfare arena: the degree of conflict/cooperation, substantive focus (political, military, social, economic, and so forth), and the nature of the actors involved (individuals, private organizations, nation states, international organizations, the general public, media, etc.).
The workshop participants generally accepted the broad nature of the information warfare domain and the central role of information systems and processes in the world today. However, they inferred several very important implications from this broad characterization of the relevant domain.
Workshop participants were aware of a variety of policy initiatives to create interagency working groups and coordinating mechanisms as well as public-private dialogues and mechanisms for both exchanging information and developing plans for dealing with information age threats that cut across communities. Considerable progress has been made in generating better awareness of the threat and there is some effort toward cooperation. However, the general consensus was that these helpful activities were only now developing momentum and were far from successful completion.
It is clear that the information age has spawned new relationships and greatly expanded the range of possible interactions. It is no longer possible to separate and isolate military, national, public, and private systems. Thus, concepts of national security, to include protecting information systems and deterring attacks, need to be expanded to consider the full range of likely interactions. This would help to determine where the boundary between DoD and the rest of the national information infrastructure should lie. It was in this context that the workshop primarily addressed the relationship between information warfare and deterrence.
At the abstract level, the interface between these two concepts is dependent on setting the context clearly. First, deterrence is always from an actor toward a target. The very nature of the actor and target, as well as the degree of asymmetry between them is important. A nation state has much greater power than an individual hacker and has broad powers of law enforcement that can be brought to bear if the individual is within its borders or the reach of accepted international laws. However, two nation states are, at least in legal terms, equal and must exercise the international system (diplomacy, warfare, etc.) to influence one another's behavior.
Moreover, the nature of the relationship between the parties is important to the analysis. The use of deterrence is unlikely in cooperative arrangements, more likely in competitive ones, and most likely in conflictual patterns. Finally, substantive context may also make a difference. For example, deterrence is most likely in military arenas where the credibility of threats is greatest and easiest to assess. Hence, specification of the context (type of relationship, nature of the actors, substantive domain) is essential before any conclusion is possible about the effectiveness of deterrence.
The most important insight arising from looking at the two concepts however, is the fact that they are only relevant to one another in highly selective contexts. The analogy that emerged was that of a steamroller and a wrench. Both are tools and depending on the situation, appropriate wrenches may be useful for, or even crucial to, the operation of the steamroller. However, most of the things the steamroller does are irrelevant to the wrench and most of the things the wrench can be used for do not involve a steamroller. In many cases, therefore, the workshop found itself venturing away from a pure consideration of the two concepts and into meaningful discussions in areas related to one or the other of the two central topics. These discussions revolved around the concepts, but kept slipping tangentially to more familiar issues such as command and control warfare (C2W), or IW in some other context such as retaliation in kind for an IW attack. It eventually became apparent that the main reason for frustration was that the related concepts and issues are grossly mismatched. IW is just too big and encompasses so much (particularly in the context of information dominance), while deterrence is limited and almost always case specific.
In retrospect, the revelation should not have been surprising. While workshop participants noted that certain IW actions are as old as warfare (a bluff for example), the exploding vistas of information technology and cyberspace are only beginning to be understood. Several of the participants were comfortable discussing deterrence as it might be related to command and control warfare (C2W). In this application there are five clearly defined "Pillars" which include Operational Security (OPSEC), Electronic Warfare (EW), Psychological Operations (PSYOPS), Military Deception, and Physical Destruction. The pillars are arrayed both offensively as "Counter-Command and Control" and defensively as "Command and Control Protection." Both arrays are dependent on and supported by intelligence. Any one of the pillars can have a deterrent effect. For example, in EW the presence of anti-radiation missiles may deter the use of air defense radar. Likewise, the adroit use of psychological operations might disrupt the enemy decision making process to the point where they are deterred from action, or at least their C2 process is greatly slowed.
While we believe that we understand C2W, the workshop brought into clear focus the fact that C2W is only a very small subset of IW, and it is that larger context that needs further exploration and analysis. Likewise, one size IW deterrence does not fit all. Equally important to the action itself is the intended recipient. Without getting into the adversary's mind and understanding his social, cultural, and religious values, as well as his education and past history, IW deterrence actions may be like the tree that falls in the forest and goes unheard. They may even be misunderstood and, therefore, have unintended consequences. The earlier discussion of deterrence stressed that creditable deterrence requires that the message be communicated clearly. Knowing how the adversary receives and understands messages is essential.
It also became increasingly clear that IW deterrent actions must be part of an orchestrated and integrated effort. Seldom will an IW action in and of itself be a creditable deterrent. However, skillfully combined as part of an overall information dominance concept, some combination of IW and other actions may produce the desired deterrence.
Table of Contents | Chapter 2 |