
As information age technologies become more useful and valuable across all arenas and levels of interaction, vulnerabilities to disruption, deception, penetration, theft, and destruction increase as well. The vulnerabilities cluster around two basic areas: the computers that form the heart of most information systems and increasingly control operating systems, and the communication networks that tie them together. Workshop participants noted that recent studies indicate that all too often computer security is still given short shrift. Records that would be locked up if they were paper are often left unprotected in computers. When computers are networked, they become even more vulnerable because information can be accessed from remote locations. Both locally and remotely, data can be manipulated, viruses inserted, and records stolen or destroyed. When the data being manipulated or moved represents money or other things of value, the manipulation is theft. Presently, the banking system is reportedly losing millions of dollars each year to computer theft. At the Department of Defense, hackers have penetrated DoD networks and systems (mostly unclassified). Moreover, recent tests indicate that only about five percent of attacks are detected, and of those detected, only five percent reported. If these figures are correct, the likelihood of knowing about an attack is .0025 (one-quarter of a percent) and the risk of being caught must be, by definition, even lower. Other military systems are likewise vulnerable. In many cases that vulnerability cannot be reduced by isolation because military systems depend on the national information infrastructure for about ninety percent of their traffic. Over ninety-five percent of all U.S. Government telecommunications within the U.S. travel on commercial circuits.
From the banking system to air traffic control, from military logistics to the telephone networks, from the stock exchanges to computer controlled trains, the United States, its economy, and its security are inexorably bound up in information technology. Many of the key systems lack safeguards or redundancy. Some, including some defense systems, are extremely fragile and easily disrupted. Most are vulnerable in one way or another. The U.S. information infrastructure is easily the world's biggest IW target.
Given these vulnerabilities, what can be done to enhance security and improve the likelihood that the United States can deter IW attacks? What are the DoD's responsibilities, and where are the boundaries of those responsibilities? Since U.S. forces cannot fight effectively without being well connected to the national information infrastructure, the responsibility would appear to go well beyond the protection of military systems alone. The workshop noted that this is a broad national security issue that the military cannot ignore. Since IW defense and deterrence are essential to military effectiveness, a crucial issue is to determine what role the professional military should have in this mission.
Beyond the attacks that one might envision in the context of classic IW and C2W, there are other vulnerabilities. For example:
This wide range of possibilities caused considerable discussion before the group could agree on the various types of computer attacks that must be considered. Initially, some felt the discussion should focus only on protection of internal DoD systems, while others wanted to include broad strategic or operational attacks on the banking system or other commercial or quasi-governmental arenas. The workshop was aware, however, of an ACTIS analysis of Defensive Information Warfare (Appendix D, the third and final part of the workshop read-ahead material) that differentiates attacks by their targets and implications into:
In addition, workshop participants stressed that not all information warfare attacks on computer systems need take the form of computer intrusion. Physical destruction of crucial telephone switching stations or other national information infrastructure assets would, in them-selves, be very damaging.
One significant finding was that the workshop participants consistently found themselves assuming that a visible set of defenses was the beginning point for deterring attacks on important computer systems. In essence, the argument was that attacks are instrumental acts and will not occur if the attacking party perceives little opportunity for success.
At the same time, the workshop also noted that "success" has very different meaning for different types of actors. Some individuals, particularly those with "typical" hacker attitudes, would be likely to perceive a more robust defensive posture as a challenge, not as discouragement. This, of course, is a lesson in the need for specific contexts when discussing deterrence and IW. What works in some circumstances may be very wrong for others.
Regardless of whether good defenses necessarily deter attacks, there was consensus that the set of defenses now in place is inadequate for discouraging any but the least well prepared intruder. As mentioned earlier, many systems are poorly protected, very few intrusions are detected, and very few of those detected are actually reported. Improved indications and warning, as well as improved reporting of detected attacks, are essential elements of improved defensive systems. In essence, the workshop concluded that assessing the ability of DoD or others to deter attacks will require much better documentation and understanding of the pattern of attacks being experienced.
Deterrence of cyber-attacks was also understood to depend on the nature of the attacker. On one level, deterrence requires identification of the values held by the potential attacker as well as the capacity to communicate with that attacker. Neither is possible without information about the nature of the person, group, or entity to be deterred. The variety of potential attackers is vast, which makes it impossible to create a "one size fits all" deterrence policy that will be effective. However, cyber-attacks and physical attacks on key computer systems can be prevented or discouraged by aggressive, visible, effective defensive systems. Analogies were drawn to terrorists, who also act from a variety of motives against a wide range of targets (including information domain targets), but who have been deterred in selected instances by explicit threats and retaliatory actions implying future threats unless the terrorists cease to attack some types of targets.
There is no single, simple solution. However, combinations of defensive measures are important initial building blocks. Further, defense against information attacks should be viewed as a continuing process rather than a "finishable" project. The process begins with awareness of the issues and problems and proceeds to indoctrination, education, training, and physical defensive measures. Awareness, education, and security training are being taught within the DoD but need to be improved across all levels. It would also appear that DoD should reach out further and address the issues to other government agencies and relevant non-governmental organizations through interagency seminars, vulnerability analysis, and training.
Systems vulnerability analysis is a critical first step. We should lay out our potential target sets and interconnecting networks and look for actual and potential vulnerabilities. Defensive nodal analysis (like that conducted in offensive command and control warfare) is particularly important. Once the weaknesses are identified, defensive measures should be put in place. Table 1 lists some of the common and accepted system defenses.
|
|
|
|
|
|
|
Systems vulnerability analysis and improved design can yield three positive results. Besides the obvious result of reducing vulnerability, the systems can be made less attractive targets; that is, successful attacks would yield less damage and publicity. As stated by VADM Cebrowski (the JCS J-6, and workshop luncheon speaker), decoupling IW attacks from their objectives is an effective deterrent technique. Since IW attacks, like almost all types of attack, are assumed to be conducted for instrumental purposes, he argued that de-coupling the attack from its goal was an important way to ensure such attacks were unsuccessful and also to deter the attacks themselves because the attackers saw little opportunity for success. Good design can also raise the potential costs of attacking in terms of time and equipment needed to penetrate. This also has a deterrent effect. Hardening and protective measures should be designed into all systems. This is an enormous field that spans the spectrum from satellite antenna design to electrical protection of personal computers and workstations.
Security training is absolutely essential at all levels, and without it other defensive measures are less effective. Password protection, for example, can make information systems less accessible, but bad procedures can defeat its purpose. One of the workshop participants described security exercises where he was able to penetrate password-protected computer networks by manipulating the password protection system itself. Perhaps more important, almost every penetration and technique tried on that exercise and those in the experience of other workshop participants had been successful in the vast majority of cases. Hence, the need for basic system security design, improved security procedures, and better training within DoD.
Other key steps include redundancy and backup. These methods reduce or limit the harmful effects of an attack or system penetration. Frequent backup can minimize the damage caused by lost, stolen, or disrupted data, and information can be rapidly restored or reconstituted. Redundant baseline data can also be used to check against unwanted changes or clandestine data manipulation.
Aggressive domestic and international law enforcement can certainly have a deterrent effect on potential adversaries. Since cyberspace recognizes no borders, international agreements and laws are necessary. This is particularly important because many information systems are not only national, but also worldwide. Telecommunications and international banking systems are prime examples. Further, hackers appear motivated by the challenge of defeating defenses. Defenses alone apparently just make hacking more enjoyable. To deter hackers, there must be a realistic threat of capture and punishment.
Tagging information systems hardware and software with electronic IDs can also deter would-be penetrators and attackers. The analogy is similar to caller ID, where those who penetrate systems are identified, and a record of the penetration is made.
"Embracing" is a concept that engages potential attackers by including them as stakeholders in the information system. By embracing and educating these possible adversaries, they may be less likely to consider attacks that could potentially cause self-harm. The concept is already in effect since many systems are worldwide, and an attack by one nation on another could have cascading effects beyond those intended. An attack on the banking system in one nation, for example, could have unintended consequences and cause disruptions around the world. Embracing would appear to have deterrent effect only on rational nation-states. There are two weaknesses to the concept. First, it is doubtful that cyber-terrorists would be deterred in such a scenario; rather, cascading consequences might actually make the attack more attractive. Second, what may be viewed as embracing by one party may instead be an opportunity for infiltration by the other. Again no "one size fits all" deterrence policy is available because of the range of motives that may be encountered.
Finally, we must develop an effective system of IW attack indications and warnings (I&W). The adage of "forewarned is forearmed" is particularly relevant here. Indications of attack can come from traditional intelligence sources, monitoring of events and activity, and perhaps other cyber-tags that we have yet to discover. Penetration warning systems should be designed and built into critical information networks, nodes and stations. Cyber I&W is an area that needs much more careful study, analysis, and debate.
Many of the defensive measures discussed are not unique to the deterrence arena, but rather reflect the workshop participants' assumption that some attacks will be deterred by effective defenses. The technical representatives in the workshop also stressed that for the foreseeable future the advantage will lie with the offense in the cyber-war arena. Hence, building defenses does not guarantee success, and creating redundancy as well as the capacity to contain, recover from, and reconstitute in spite of successful attacks are essential elements of a successful strategy.
An interactive exercise scenario introduced the topic of "SOFTWAR," which is a trade name for one concept of media war. This concept involves the use of television images to change or modify the political will of an opponent. SOFTWAR was defined as "the hostile utilization of instantaneous global television to shape another nation's will by changing its view of reality." The main technique of SOFTWAR is to unglue the adversary government's hold on the unifying national mass communications system, the most powerful medium of which is television, and distribute alternate video productions (or some other form of video manipulation) in its place. The speaker asserted that the controlled projection of video information has joined economic, political, and military power as a pillar of national security and that it will become a co-equal power by the year 2020.
The exercise scenario involved a campaign aimed initially at public attitudes in friendly and other regional countries whose cooperation is essential to major U.S. operations in and around the Persian Gulf, and later at public attitudes in the United States. In the demonstration scenario, the U.S. was the victim of a carefully orchestrated television campaign aimed at both the U.S. TV audience and at a selected Middle East and North Africa audience within the footprint of a direct broadcast satellite. The thrust of the argument was that prudent, even essential, military actions could well be called into question through media attacks with primarily political messages.
Some workshop participants were skeptical about the impact such a campaign might have on U.S. resolve and action. There are, however, past examples of how TV has affected U.S. political action going back to the Vietnamese War when rather primitive TV reporting (by today's standards) brought bloody battlefield images into U.S. homes for the first time. There is little doubt that television coverage of Vietnam changed or eroded the will of the U.S. population to sustain the conflict. Likewise, TV images of the bombing of the U.S. Marine Barracks in Lebanon tested our resolve and hastened our departure.
More recent examples include the Somalian relief mission where graphic, quite gruesome TV images of relatively light U.S. casualties soured the support for continued presence and led to an early U.S. pullout. In Haiti, TV images of U.S. soldiers standing by while Haitian police beat innocent people celebrating the arrival of U.S. forces caused an overnight change in policy as to how Rules of Engagement (ROE) were interpreted. The workshop agreed that indeed, television is an extremely effective, and potentially dangerous, medium for propaganda. Given the ability of modern technology to manipulate images, it becomes an even more powerful IW weapon. Several other conclusions emerged from the media war discussions:
Many of the workshop discussions naturally evolved into policy explorations. Two of the most prominent were: one, "Should the United States have a declarative policy about its response to IW attacks?" and two, "Should information be viewed as a separate element of national power?" Opinion was divided on both issues. Table 2 highlights the arguments for and against a declared policy on U.S. response to IW attacks.

The workshop participants were strongly in favor of a declared policy, with 70 percent voting for such a policy, 17 percent against, and 13 percent ambivalent. A declared policy was considered essential if there was to be any deterrent effect. Further, without a policy, there is no direction for the government, and many agencies are going their own ways and establishing their own policies. If we are to have cooperative international agreements and treaties, a declared policy is an essential starting point. The policy should be coordinated with industry and public debate encouraged to secure support and resources required to protect our interests. The overall workshop consensus was that there should be a broad, publicly stated, general policy phrased in terms of effects rather than method or type of attack (e.g., economic, military, social, political). One recommended statement was: "Attacks on the U.S., its infrastructure, or other interests (by whatever means) will receive an appropriate response using the fullest range of U.S. capabilities."
Those who were ambivalent or opposed to a declared policy were generally concerned that such a policy was premature, that we lacked sufficient understanding of IW attacks and their effects and consequences. By not stating a specific policy, we create ambiguity, which some felt was useful in terms of deterrence. There is much to think through before declaring an IW policy particularly in terms of the international implications and complications. Finally, and somewhat in agreement with those who advocated a formal policy, one reason not to have a policy is simply that there is no need to separate IW from other kinds of attacks.
On the second issue, whether information should be viewed as a separate element of national power, opinion was also divided; however, most participants viewed information as a separate element of national power. Table 3 summarizes the comments.
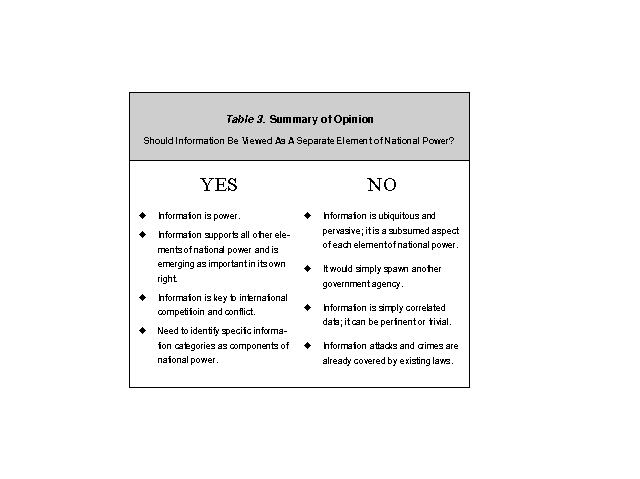
All participants agreed that information was an essential element of power. The debate ranged around whether that should be stated explicitly or not. Those in favor (80 percent) cited the growing importance of information and information age technologies, and how information is creating a cultural revolution and changes in the behavior processes between nation-states. For those who voted "no" (20 percent), the major consideration was that they viewed information as ubiquitous and pervasive in each element of power, and not an independent element. One participant made the analogy that information was like "electricity." It is subsumed in other elements and systems.
There were numerous other questions with policy implications and these included:
Since at present no one has the charter for IW (in the larger context -- beyond C2W) responses will be ad hoc at best. The boundary between DoD and the rest of the national infrastructure is blurred and undefined. The workshop reached no consensus as to where that line should be or what DoD's role should be within the larger context.
IW policy issues emerged as the area that needed much further study. Without policy definition, concepts like IW and deterrence can't be fully explored. Policy is essential and the workshop participants recommended a follow-on roundtable to explore policy issues. Basic policy statements have begun emerging, but final work appears necessary.
Given the low rate of reporting system penetrations and other security problems, the U.S. presently lacks the data needed to know just how serious the unauthorized penetration problem might be. Are we hemorrhaging or simply suffering "duck bites"? Better reporting is essential.
The starting point for DoD should be to raise the level of awareness, not only within the Department, but also throughout the national information infrastructure upon which it is so vulnerably dependent. Developing and implementing cyber I&W should also take high priority. One note of concern voiced was that the DoD procurement cycles and information technology growth cycles are greatly mismatched. That is, several technology cycles occur within one DoD procurement cycle. This can result in DoD developing yesterday's solutions for tomorrow's problems.
DoD's next priority should be a comprehensive vulnerability analysis, first of DoD systems and later expanded to the national infrastructure upon which they depend. At present, vulnerability is usually assessed for only a particular system or subsystem. Future vulnerability analyses should expand the studies to examine interrelated systems, and systems of systems. In due course, the analyses should be expanded to include all U.S. systems. We should implement defensive and deterrent actions as soon as vulnerabilities are uncovered.
Beyond DoD, there is a need for a national level, strategic debate to formulate a coherent IW policy and a determination of DoD's boundaries and responsibilities. Neither DoD nor the Federal Government can do this alone; all relevant public and private sectors should be included. But until there is policy about IW defense and deterrence, DoD still has the responsibility to protect its strategic, operational and tactical systems. The strategic systems appear reasonably well protected and redundant through hardening, elaborate security procedures, and multiple backups. Operational and tactical systems appear far less protected and need additional emphasis.
While recognizing that the variety of potential attackers, attack contexts, and arenas where information warfare attacks can occur is vast and too complex for simple solutions, the workshop participants were confident that the U.S. already has basic policies in place that serve as effective deterrents in many circumstances. In essence, information warfare attacks on the United States are deterred by the same policy that deters other types of attack. Acting under its rights as a sovereign state, the U.S. stands ready to respond to any attack on its interests with all appropriate means, including law enforcement as well as military capacity. As discussed in the workshop:
There was also consensus that information attacks may well pose some unusual challenges that may make them more difficult to deter. For example, information warfare attackers will likely seek to be anonymous, thereby making it impossible for the U.S. to punish them. Cyber-attackers, in particular, have a variety of mechanisms by which they can hide their identity. Since certainty of punishment is a prerequisite for deterrence, anonymity is an effective counter-strategy.
Moreover, information attacks can be hidden or made to look like natural events. In media war, this may be a half-truth fed to an aggressive reporter. In cyber-war it can be a destructive attack made to look like a system error or design flaw. Disguised attacks are also effective countermeasures for deterrence, regardless of the capability and will of the actor. Hence, while significant, overall U.S. capability and will do not guarantee deterrence of information attacks.
Finally, the workshop recognized that considerable legal work needs to be completed in this arena. First, U.S. law (both state and federal) needs to be clear about the definition of crimes in the information arena. Second, international agreements and treaties are needed to ensure that information criminals can be prosecuted effectively. Cases in which lack of appropriate law limited or prevented prosecution were easy for participants to recall. The Departments of Justice and State are generally aware of these needs and interagency working groups have been making some progress on them, but this area will require continued effort for some time to come.
Table of Contents | Chapter 3 |