Information warfare (IW) has become virtually synonymous with the revolution in information technologies and its potential to transform military strategies and capabilities. There is a growing consensus that national prosperity, if not survival, depends on our ability to effectively leverage information technology. Without being able to defend vital information, information processes, and information systems, such a strategy is doomed to failure.
Information warfare is often thought of as being defined by a particular target set�decision makers, information, information processes, and information systems. The "battlespace" associated with IW has been a constantly expanding one, moving far beyond traditional military situations. In some quarters, IW has even been associated with the leveraging of information technologies to achieve greater effectiveness and efficiency. This has stretched the meaning of IW to the breaking point and has sowed more confusion than enlightenment. For this reason, this treatment of the subject uses the term "information strategies" to refer to the recognition and utilization of information and information technologies as an instrument of national power that can be independent of, or complementary to, military presence and operations.
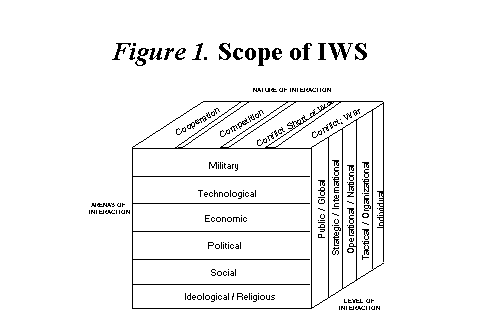
The scope, or battlespace, of information warfare and strategy (IWS) can be defined by the players and three dimensions�the nature of their interactions, the level of their interactions, and the arena of their interactions (see Figure 1, Scope of IWS). Nation states or combinations of nation states are not the only players. Non-state actors (including political, ethnic, and religious groups; organized crime; international and transnational organizations; and even individuals empowered by information technology) are able to engage in information attacks and to develop information strategies to achieve their desired ends.

The term "war" has been used so loosely in recent times (e.g., War on Poverty, War on Drugs, War on Crime) that is should be no surprise that IW has evolved over the past several years to become a "catch-all" term that encompasses many disparate activities, some of which have long been associated with competition, conflict, and warfare, and others that are of more recent origin. These include activities that range from propaganda campaigns (including Media War), to attacks (both physical and non-physical) against commanders, their information sources, and the means of communicating with their forces. Under this rather large umbrella that has become known as IW, one can find activities long associated with military concepts and operations, including deception, command and control warfare (C2W), and psychological operations (Psyops). Technological advances have added new forms such as electronic warfare (EW) and "hacker warfare."
The term "defensive information warfare" (IW-D) is used here to refer to all actions taken to defend against information attacks, that is, attacks on decision makers, the information and information-based processes they rely on, and their means of communicating their decisions. Strictly speaking, since these attacks can be launched during peace time at nonmilitary targets by nonmilitary groups, both foreign and domestic, the term IW-D should be IWS-D. However, IW-D is currently in wide use.
This overview of IW-D does not attempt to deal with the problems of defending against all of the different kinds of information attacks, but rather focuses its attention on the subset of IW that involves attacks against our information infrastructure, including what has become known as "hacker warfare" and in its more serious form, "digital warfare."