The Department of Defense Critical Infrastructure Protection (CIP) Plan
A Plan in Response to
Presidential Decision Directive 63
"Critical Infrastructure Protection"
Prepared By:
DASD (Security and Information Operations)
Critical Infrastructure Protection Directorate
Approved:
_____________________________________
Deputy Secretary of Defense
18 November 1998
(page is intentionally blank)
Table of Contents
1. Executive Summary *
2. Critical Infrastructure Protection *
2.1 Background
*2.2 Scope and Purpose
*2.3 Key Terms and Concepts
*3. The National Structure for Critical Infrastructure Protection *
3.1 National Coordinator for Security, Infrastructure Protection and Counter-Terrorism
*3.2 Infrastructure Assurance Research and Development (R&D) Coordination
*3.3 National Infrastructure Assurance Council (NIAC)
*3.4 Critical Infrastructure Coordination Group (CICG)
*3.5 CICG National Defense Coordination Sub-Group
*3.6 Lead Agencies for Sector Liaison
*3.7 National Plan Coordination Office
*3.8 Information Sharing and Analysis Center (ISAC)
*3.9 National Communications System (NCS)
*3.10 National Security Telecommunications Advisory Committee (NSTAC)
*3.11 National Infrastructure Protection Center (NIPC)
*3.12 Lead Agencies for Special Functions
*4. The Department of Defense Structure and Responsibilities for Critical Infrastructure Protection *
4.1 DoD Critical Infrastructure Protection Responsibilities
*4.2 CIP Functional Coordinator for National Defense , DoD Chief Infrastructure Assurance Officer, and DoD Chief Information Officer
*4.3 DoD General Counsel [DoD(GC)]
*4.4 Chief Infrastructure Assurance Officer Council
*4.5 Chief Information Officer Council
*4.6 Lead Components for Defense Infrastructure Sector Assurance Coordination
*4.7 DoD Critical Asset Owners
*4.8 DoD Installations
*4.9 Lead Components for Coordination of DoD Special Functions
*4.10 Joint Task Force--Computer Network Defense (JTF-CND)
*4.11 DoD CIP Integration Activity (CIPIA)
*4.12 The CICG National Defense Coordination Sub-Group
*5. The DoD Critical Infrastructure Protection Life Cycle *
5.1 Infrastructure Analysis and Assessment
*5.2 Remediation
*5.3 Indications and Warning
*5.4 Mitigation
*5.5 Incident Response
*5.6 Reconstitution
*6. Implementation Schedule *
7. Program Resources *
Appendix A: Glossary A-*
Appendix B: National and Defense Critical Infrastructure Definitions B-*
Appendix C: DoD CIP Integration Activity (CIPIA) C-*
Appendix D: DoD Critical Asset Assurance Program (CAAP) D-*
Appendix E: Infrastructure Assurance Program (IAP) E-*
Appendix F: The Defense-wide Information Assurance Program (DIAP) F-*
Appendix G: Defense Infrastructure Sector Assurance Plans G-*
Appendix H: Table of Acronyms H-*
The DoD has improved operational readiness through a comprehensive, fully integrated, and sustainable life cycle process for protection of those elements of defense, national, and global infrastructure essential to its operations. – DoD CIP Vision 2000
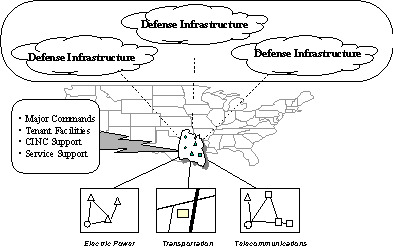
Presidential Decision Directive 63 (PDD 63), Critical Infrastructure Protection, was approved 22 May 1998, in response to the findings and recommendations of the President’s Commission on Critical Infrastructure Protection (PCCIP). The Directive states that certain national infrastructures, e.g., energy, information and communications, and banking and finance, are critical to the national and economic security of the United States and the well being of its citizenry, and that the United States will take all necessary measures to protect them. The Directive calls for a public-private partnership to provide protection, establishes a national organizational structure to effect that partnership (Figure 1-1), and directs the development of two sets of plans: each Federal department’s or agency’s plan to protect its portion of the Federal Government Critical Infrastructure and a comprehensive National Infrastructure Assurance Plan with input from all infrastructure sectors.
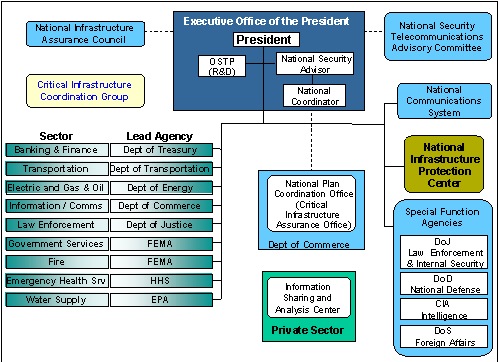
Figure 1-1. National Structure for Critical Infrastructure Protection
This document addresses how the Department of Defense (DoD) will protect its portion of the Federal Government Critical Infrastructure. Where appropriate, the DoD Critical Infrastructure Protection (CIP) program will capitalize on the work occurring under the DoD Antiterrorism Force Protection (AT/FP) Program, e.g., installation vulnerability assessments. CIP and Force Protection (FP) are complementary efforts. CIP protects assets and assures the viability of infrastructures critical to mission success. FP protects people, facilities and equipment from an installation viewpoint.
The DoD portion of the Federal Government Critical Infrastructure is defined as the defense-wide sectors that provide infrastructure services within the Department: Defense Financial Services; the Defense Information Infrastructure; Defense Logistics; Defense Transportation; Defense Space; Defense Personnel; Defense Health Affairs; Defense Public Works; Defense Command, Control, and Communications; Defense Intelligence, Surveillance and Reconnaissance; and Defense Emergency Preparedness.
The portion of the national infrastructure that directly supports the Defense Infrastructure is defined as the National Defense Infrastructure. As the CIP Functional Coordinator for National Defense, DoD is responsible for identifying the National Defense Infrastructure and working with the national CIP organizational structure and with the private sector to ensure its protection.
The Assistant Secretary of Defense (Command, Control, Communications, and Intelligence) (ASD(C3I)) is appointed the Department Chief Infrastructure Assurance Officer (CIAO) and the CIP Functional Coordinator for National Defense. In these roles, the ASD(C3I) is responsible both for protection of DoD critical infrastructure and for DoD participation in the national program. The ASD(C3I) is also the DoD Chief Information Officer.
Additionally, Lead Components for Defense Infrastructure Sector Assurance are established. Each Lead Component will appoint a Sector Chief Infrastructure Assurance Officer. The DoD and Sector CIAOs, together with the CIP Special Function Coordinators (i.e., Military Plans and Operations, Intelligence Support, International Cooperation, Research and Development, and Education and Awareness), and the Services comprise the DoD CIAO Council. The DoD CIAO will establish a CIP Integration Activity to support coordination among DoD CIP entities and a number of extant DoD programs with functions that contribute to CIP, e.g., the Critical Asset Assurance Program (CAAP), the Defense-wide Information Assurance Program (DIAP), and the Infrastructure Assurance Program (IAP). The DoD organizational structure for Critical Infrastructure Protection is illustrated in Figure 1-2.
The DoD Critical Infrastructure Protection Program will address the full life cycle of protection. The life-cycle phases are described below:
Infrastructure Analysis and Assessment
. Coordinated identification of DoD, National Defense, and International Defense critical assets, their system and infrastructure configuration and characteristics, and the interrelationships among infrastructure sectors; assessment of their vulnerabilities; quantification of the relationship between military plans and operations and critical assets / infrastructures; and assessment of the operational impact of infrastructure loss or compromise.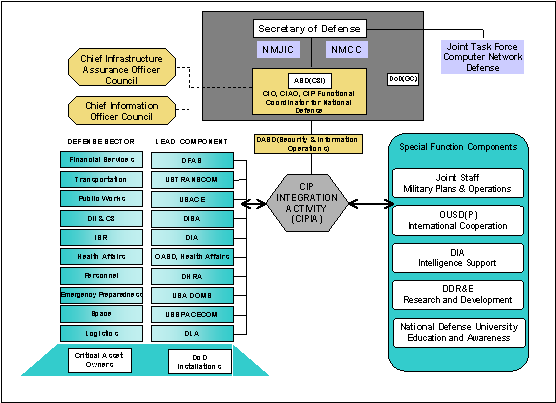
Figure 1-2. DoD Structure for Critical Infrastructure Protection
Remediation
Indications and Warning. Tactical indications through the implementation of sector monitoring and reporting, strategic indications through Intelligence Community support, and warning in coordination with the National Infrastructure Protection Center (NIPC) in concert with existing DoD and national capabilities.
Mitigation. Pre-planned and coordinated operator reactions to infrastructure warning and/or incidents designed to reduce or minimize impacts; support and complement emergency, investigatory, and crisis management response; and facilitate reconstitution.
Response. Coordinated third party (not owner/operator) emergency (e.g., medical, fire, hazardous or explosive material handling), law enforcement, investigation, defense, or other crisis management service aimed at the source or cause of the incident. Response to infrastructure incidents involving Defense infrastructure will follow one of two paths: (1) affected Components and/or the Joint Task Force -- Computer Network Defense (JTF-CND) will defend against and respond to all cyber incidents in accordance with granted authorities and established operational procedures, or (2) affected Components will defend against and respond to all non-cyber incidents in accordance with granted authorities and established operational procedures.
Reconstitution. Owner/operator directed restoration of critical assets and infrastructure.
The DoD will achieve critical infrastructure protection through the development (November1999) and implementation (November 2000) of coordinated Defense Infrastructure Sector and Special Function plans. The DoD will fulfill its CIP National Defense responsibilities by participating in the interagency Critical Infrastructure Coordination Group (CICG), chairing the CICG National Defense Coordination Sub-Group, and supporting the NIPC.
2. Critical Infrastructure Protection
Executive Order (EO) 13010, Critical Infrastructure Protection, dated July 1996, states that certain national infrastructures are critical to the national and economic security of the United States and the well being of its citizenry. These infrastructures are potentially vulnerable to disruption by acts of terrorism and information warfare and are considered to be likely targets of opportunity. The EO established the President’s Commission on Critical Infrastructure Protection (PCCIP) composed of both public and private sector representatives, and charged them to assess the threats and vulnerabilities to the Nation’s infrastructures and to recommend national policy and a strategy for protection.
The PCCIP submitted its report, Critical Foundations, in October 1997. An electronic version is available at www.pccip.gov. The PCCIP’s findings and conclusions can be summarized as follows:
- US infrastructures are currently vulnerable to disruptions by both physical and cyber means. The vulnerability is increasing because of the ease of access to physical and cyber weapons and capabilities, including weapons of mass destruction; the low cost of weapons and capabilities; the high economic and political value of the infrastructures; the low probability of detection given the relative anonymity of the infrastructure environments; and the low probability of reprisal given the relative immaturity of criminal codes applicable to infrastructure disruptions.
- These vulnerabilities are exacerbated by several business trends within the infrastructures: extensive cybernation or widespread use of information automation; deregulation and restructuring; physical consolidation; globalization; and adoption of a "just-in-time" operational tempo.
- The United States has no more than a three to five year window to implement a comprehensive national infrastructure protection program before these trends begin to affect national and economic security.
- There is a general lack of awareness among both the public and private sector regarding vulnerabilities.
- The interdependent nature of infrastructures creates a shared risk environment. Managing that risk will require a public-private partnership. There exist many legal, social, cultural, and economic impediments to the kind of public-private partnership necessary for national protection.
The PCCIP report was the basis for Presidential Decision Directive 63 (22 May, 1998), Critical Infrastructure Protection, which establishes national policy and an organizational structure for effecting a public-private partnership and for accomplishing the special protection functions that are inherently the responsibility of government. The national structure for critical infrastructure protection is described in Section 3 of this document. Electronic white papers and facts sheets are available at www.ciao.gov.
This document responds to the PDD 63 tasking to each federal Department and Agency to develop a plan for protecting its portion of the Federal Government Critical Infrastructure, and to submit that plan to the National Coordinator for Security, Infrastructure Protection and Counter-Terrorism for interagency review. This document describes the way the DoD will organize to identify and protect DoD owned infrastructure assets, and how the Department will interact with entities in the national program to effect that protection. It also describes the way the Department will identify and coordinate assurance requirements for those elements of US government and national infrastructure that are critical to Defense operations (the National Defense Infrastructure) and for those elements of global infrastructure that are critical to Defense operations (the International Defense Infrastructure).
This document does not address responsibilities of DoD’s Antiterrorism Force Protection (AT/FP) Program. This document does not address the life-cycle protection of the National Infrastructure, National Defense Infrastructure (NDI) or International Defense Infrastructure (INDI); nor the Federal Government’s partnership with the private sector.
These issues will be addressed in the forthcoming National Infrastructure Assurance Plan, to which DoD will contribute.
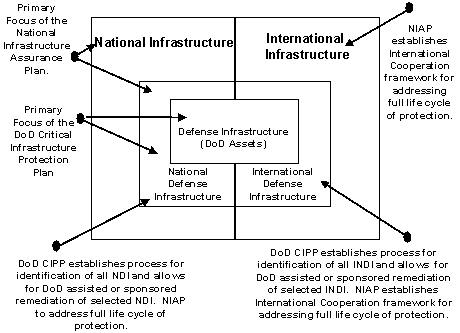
Figure 2.1. National Infrastructure Assurance Plan
PDD 63 requires the implementation of Federal Government Critical Infrastructure Protection plans within two years, coinciding with an Initial Operating Capability (IOC) for the national program. Target Full Operating Capability (FOC) for the national program is five years. DoD will achieve protection of its portion of the Federal Government Critical Infrastructure through the development and implementation of a series of DoD Critical Infrastructure Protection Plans. This document is the first in that series and is intended to establish roles and responsibilities, initial resources, and oversight and coordination mechanisms. This plan is not intended in and of itself to be sufficient guidance for DoD Components to generate supporting plans, nor is it intended to be comprehensive in its delineation of CIP responsibilities for those DoD Components which also have national responsibilities, e.g., the Defense Intelligence Community.
2.3 Key Terms and Concepts
Infrastructure Assurance and Infrastructure Protection
Providing assurance and protection for DoD critical infrastructure is a complex problem. The complexity of the problem manifests itself in several ways:
- The lack of a shared understanding of the terminology, insufficiently precise terminology, and misuse of terminology
- The use of "infrastructure", "infrastructure assurance", and "infrastructure protection" terminology both in DoD and at the national level is abundant; however, there is a general lack of rigor necessary to convey meaning consistently, ensure methodical use, and promote a healthy maturation of the lexicon
- The variety of different and valid perceptions held by the Department’s and the nation’s leadership and its practitioners about the meaning and discipline of designing, evolving, assuring and protecting infrastructures
- The breadth of the communities and disciplines which must be engaged and their attendant specialized and unreconciled lexicons
- An apparent suspicion of the government’s motives and capabilities on the part of many of the private sector entities that own the national infrastructures upon which the nation and DoD depend
The national policy and strategy articulated in PDD 63 calls for both infrastructure assurance and infrastructure protection; however, it fails to consistently distinguish between the two. Prior to PDD 63, the prevailing usage of assurance and protection within DoD was consistent with the third definition listed below. However, one can view the title of PDD 63 as an indication that the national trend will be toward the fourth definition below. The DoD has begun to move in that direction with the naming of the newly established Critical Infrastructure Protection Directorate and with the defining of the protection life cycle in Section 5 of this document. While DoD uses the term "assurance" according to the third definition, in interagency activities we must consider the term "protection" as a synonym for "assurance." For those elements of the Department interacting with the interagency community, it is important to note that at least five competing meanings are emerging, and unfortunately, are being applied within single documents and discussions:
- Assurance and protection as interchangeable synonyms (also interchangeable with security)
- Assurance as an umbrella term for the activities of analysis, assessment and remediation and protection as an umbrella term for indications and warning and response
Section 5 of this document contains a more detailed discussion of these activities. The designation of mitigation and reconstitution as either assurance or protection is less clear, with mitigation being included somewhat more often in protection and reconstitution somewhat more often in assurance.
- Assurance as a comprehensive term that includes all activities (analysis, assessment, remediation, I&W, mitigation, response, and reconstitution) with protection a subset of these activities (indications and warning, mitigation, and response)
This usage is consistent with DoDD 5160.54, Critical Asset Assurance Program, and DoD information assurance policy and programs.
- Protection as a comprehensive term that includes all activities (analysis, assessment, remediation, I&W, mitigation, response, and reconstitution) with assurance as a subset of these activities (analysis, assessment, remediation and sometimes reconstitution)
- Assurance : the state of having confidence, of being free from doubt and uncertainty; satisfaction with the truth or certainty of a matter based on an understanding of the risks
Protection: the state of being defended, safeguarded, or shielded from injury, loss, or destruction
The emerging national meaning of ‘infrastructure protection’ must necessarily include the concepts contained in the fifth definition. Clearly, the DoD must strive to understand the risks to critical infrastructures. It must also understand the risks to national security and national defense operations posed by dependence on fragile or vulnerable interdependent critical infrastructures. Likewise, DoD must strive to shield its own operations from infrastructure compromise or disruption, in addition to supporting any national effort directed at the protection of critical national infrastructures. Decisions regarding infrastructure safeguards must be based upon a systematic and scientific understanding of infrastructure risks and the value of infrastructure to national security and national defense operations. The challenge for the Department and for the national program is to develop the ability to articulate how our current and planned infrastructure assurance and protection capabilities fit in the context of National Security, Economic Security, and National Defense.
Vulnerability and Criticality
PDD 63 also calls for assessments of the vulnerability of critical infrastructures to both physical and cyber attack. These assessments are to include, as appropriate, "the determination of the minimum essential infrastructure in each sector," and remedial plans are to be developed based on these assessments. This begs the questions: essential or critical to whom or for what? The DoD Critical Asset Assurance Program (CAAP) views criticality (or minimum essential) as a function of time and situation for two classes of assets: (1) those assets necessary to maintain a defined level of service for a given window of time within an infrastructure sector, and (2) those assets necessary to connect identified users to that service. Service level, service duration, and service connectivity requirements are driven by the user. For DoD, the primary user is the military operator. Protection activities are investments aimed at improving the probability that those service requirements will be met. The challenge for the DoD CIP program is to have military requirements drive protection investments. To do so, the Department must develop the ability to directly relate the cost/benefit of protection to user requirements.
Assets, Infrastructures, and Interdependencies
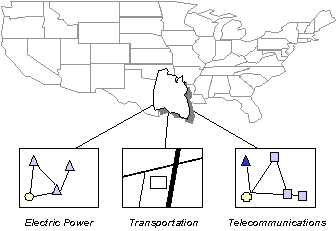
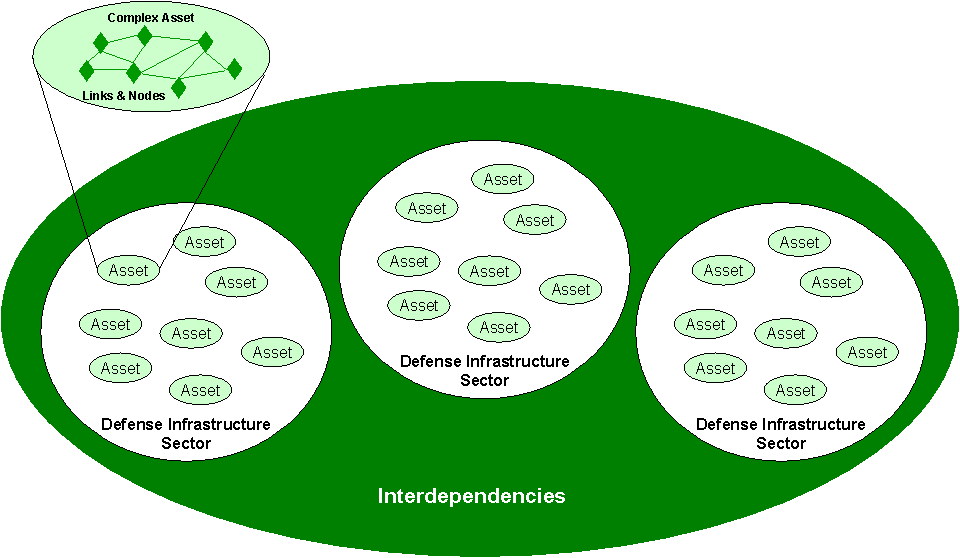 In early 1997, prior to the issuance of PDD 63, the Deputy Secretary established the Critical Infrastructure Protection Working Group (CIPWG) and recommended that the new CAAP, developed to implement the requirements of Executive Order 12656, Assignment of Emergency Preparedness Responsibilities, also be the DoD mechanism for providing infrastructure assurance. They did so with an understanding that Defense Infrastructure is composed of assets which can be organized into sectors, as illustrated in Figure 2-2. An asset may be a simple contiguous facility with one geographic location or a complex asset composed of geospatially-distributed links and nodes. For example, the Global Command and Control System (GCCS) is a complex asset in the C3 defense infrastructure sector that is dependent on the Defense Information Infrastructure sector for services.
In early 1997, prior to the issuance of PDD 63, the Deputy Secretary established the Critical Infrastructure Protection Working Group (CIPWG) and recommended that the new CAAP, developed to implement the requirements of Executive Order 12656, Assignment of Emergency Preparedness Responsibilities, also be the DoD mechanism for providing infrastructure assurance. They did so with an understanding that Defense Infrastructure is composed of assets which can be organized into sectors, as illustrated in Figure 2-2. An asset may be a simple contiguous facility with one geographic location or a complex asset composed of geospatially-distributed links and nodes. For example, the Global Command and Control System (GCCS) is a complex asset in the C3 defense infrastructure sector that is dependent on the Defense Information Infrastructure sector for services.
Appendices A and B contain additional terms and infrastructure definitions.
(page is intentionally blank)
3. The National Structure for Critical Infrastructure Protection
The national structure for CIP is established by PDD 63 and illustrated below.
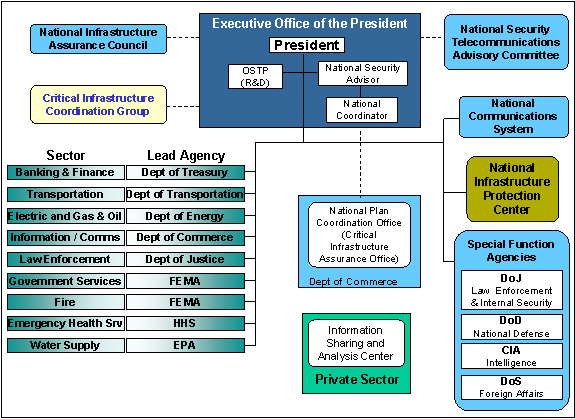
Figure 3-1. National Structure for Critical Infrastructure Protection
Key entities of the national CIP structure include the following:
3.1 National Coordinator for Security, Infrastructure Protection and Counter-Terrorism
The National Coordinator reports to the President through the Assistant to the President for National Security Affairs (i.e., National Security Advisor). The National Coordinator provides budget advice and ensures interagency coordination for policy development, implementation, and crisis management.
3.2 Infrastructure Assurance Research and Development (R&D) Coordination
The Office of Science and Technology Policy (OSTP) in the Executive Office of the President is responsible for coordinating a national portfolio for infrastructure assurance research and development through the National Science and Technology Council (NSTC). An NSTC Interagency Working Group (IWG) for CIP R&D is co-chaired by OSTP and deputy co-chaired by DoD and Department of Commerce. The Directorate of Defense Research and Engineering (DDR&E) provides the DoD deputy co-chair.
An advisory panel of major infrastructure providers and state and local government officials is to be appointed by the President to serve as the NIAC. The NIAC will enhance the partnership of the public and private sectors in protecting the nation’s critical infrastructures and will provide reports to the President. Senior Federal Government officials will participate in NIAC meetings, as appropriate.
The Sector Liaison Officials and Functional Coordinators, as well as representatives from other relevant Federal departments and agencies, including the National Economic Council, meet as the CICG to coordinate the implementation of PDD 63. The National Coordinator chairs the CICG. All Lead Agencies are required to establish and chair CICG sub-groups to address assigned responsibilities.
A permanent sub-group to the CICG for coordination of National Defense related issues. Its purpose is to assist the Functional Coordinator for National Defense in the planning and provision of infrastructure services required for national defense under all circumstances, including crisis or emergency, attack, recovery, and reconstitution. The DoD Director for Critical Infrastructure Protection chairs the sub-group. Proposed membership is provided in Section 4 of this document.
For each infrastructure, a single US Government department serves as the Lead Agency for liaison with the private sector for infrastructure assurance. Each Lead Agency appoints a senior official of Assistant Secretary rank or higher to serve as the Sector Liaison for that area and to cooperate with the private sector representatives (i.e., Sector Coordinators). The national critical infrastructures are described in Appendix B.
A National Plan Coordination (NPC) Office staff will be contributed on a non-reimbursable basis by the Federal departments and agencies. Additionally, each Lead Agency for Sector Assurance will work with its sector to develop a sector assurance plan. The NPC staff will integrate the various sector plans into the National Infrastructure Assurance Plan (NIAP) and coordinate analyses of the US Government’s own dependencies on critical infrastructures. Within 180 days of the issuance of the PDD, a schedule for completion of the NIAP will be submitted to the President. NPC staff will also help coordinate a national education and awareness program, and legislative and public affairs. The National Plan Coordination Office is located in the Department of Commerce where, subsequent to the approval of the PDD, it has been renamed the Critical Infrastructure Assurance Office (CIAO). The Critical Infrastructure Assurance Office is distinct from and should not be confused with Federal Department and Agency Chief Infrastructure Assurance Officers (CIAOs).
The National Coordinator, working with the Sector Coordinators, Sector Liaison Officials, and the National Economic Council will consult with the owners and operators of the critical infrastructures to encourage creation of a private sector information sharing and analysis center. Such a center could serve as a mechanism for gathering, analyzing, appropriately sanitizing, and disseminating private sector information and information received from the NIPC regarding critical infrastructure protection, including information about vulnerabilities, threats, intrusions, and anomalies. Within 180 days of issuance of the PDD, the National Coordinator, with the assistance of the CICG, including the National Economic Council, will identify possible methods of providing Federal assistance to facilitate the startup of the ISAC.
The NCS is an interagency organization initially established in 1963, and re-chartered by Executive Order 12472 in April 1984, to assist the Executive Office of the President in exercising wartime and non-wartime emergency telecommunications responsibilities. The mission of the NCS is to coordinate the planning for and provisioning of national security and emergency preparedness (NS/EP) communications for the Federal Government under all circumstances. The NCS consists of the telecommunications assets of twenty-three Federal departments and agencies. The Secretary of Defense is the Executive Agent of the NCS.
PDD 63 affirmed that, while the Department of Commerce is the lead agency for information and communications, DoD will retain its Executive Agent responsibilities for the NCS.
3.10 National Security Telecommunications Advisory Committee (NSTAC)
The NSTAC was created by Executive Order 12382 in September 1982, to provide industry-based analyses and recommendations to the President regarding policy and enhancements to NS/EP telecommunications. The NSTAC is composed of up to thirty chief executives, appointed by the President, representing elements of the Nation’s telecommunications industry, including the information services, electronics, aerospace and banking sectors. DoD, as Executive Agent of the NCS, provides technical, executive and administrative support to the NSTAC. This responsibility was reaffirmed by PDD 63.
The NIPC serves as a national critical infrastructure threat assessment, warning, vulnerability, and law enforcement investigation and response entity. The NIPC staff includes representatives from the Federal Bureau of Investigation (FBI) and investigators from other agencies experienced in computer crimes and infrastructure protection, as well as representatives detailed from DoD, the Intelligence Community and Lead Agencies. All executive departments and agencies are to cooperate with the NIPC providing such assistance, information, and advice as the NIPC may request, consistent with applicable legal authorities. The NIPC provides the principal means of facilitating and coordinating the Federal Government’s response to infrastructure incidents, mitigating attacks, investigating threats, and monitoring reconstitution efforts. The NIPC may be placed in a direct support role to either DoD or the Intelligence Community, depending on the nature and level of a foreign threat or attack, protocols established between special function agencies (DoD, Department of State [DoS], Central Intelligence Agency [CIA] and Department of Justice [DoJ]), and the ultimate decision of the President.
Certain functions related to critical infrastructure protection must be performed chiefly by the Federal Government (national defense, foreign affairs, intelligence, and law enforcement). Each Lead Agency appoints a senior official of Assistant Secretary rank or higher to serve as Functional Coordinator for the Federal Government. DoD is the CIP Functional Coordinator for National Defense.
4. The Department of Defense Structure and Responsibilities for Critical Infrastructure Protection
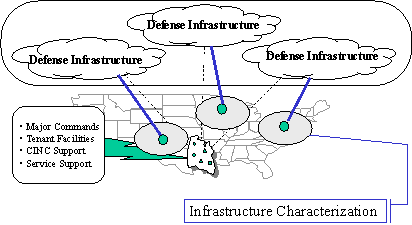
The DoD organizational structure for critical infrastructure protection must reflect, complement, and effectively interact with the national structure for CIP which is established by PDD 63 and described in the preceding section of this document. The DoD organizational structure is established by this document and is illustrated below.
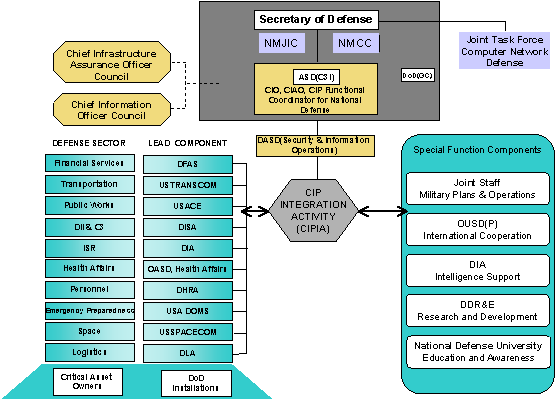
Figure 4-1. DoD Organizational Structure for Critical Infrastructure Protection
4.1 DoD Critical Infrastructure Protection Responsibilities
For critical infrastructure protection, DoD has responsibility to:
- Identify DoD owned critical assets and infrastructure and provide assurance through analysis, assessment, and remediation
- Identify National Defense Infrastructure (NDI) and International Defense Infrastructure (INDI) requirements to industry and other government agencies and monitor their inclusion in protection planning
- Address in DoD acquisitions the assurance and protection of commercial assets and infrastructure services that are critical for DoD operations
- Assess the potential impact to DoD operations (military and support) that would result from the loss or compromise of infrastructure services
- Embrace prudent business and operational planning practices to mitigate the potential impact of the loss or compromise of infrastructure services
- Monitor DoD operations and detect and respond to infrastructure incidents
- Provide Department Indications and Warning (I&W) as part of the national I&W process
- Support national critical infrastructure protection
4.2 CIP Functional Coordinator for National Defense , DoD Chief Infrastructure Assurance Officer, and DoD Chief Information Officer
ASD(C3I) is responsible for CIP policy and executive direction, and, in accordance with PDD 63, will serve in the following roles:
- Critical Infrastructure Protection Functional Coordinator for National Defense and the DoD representative on the interagency Critical Infrastructure Coordination Group
- DoD Chief Information Officer (CIO), responsible for information assurance
- DoD Chief Infrastructure Assurance Officer (CIAO), responsible for protection of all other aspects of DoD critical infrastructures not addressed by information assurance
The ASD(C3I) will ensure all DoD critical infrastructure protection needs are identified and satisfied in a timely, effective, and efficient manner, will advocate and support appropriate funding initiatives under the CIP program, and will ensure DoD General Counsel review of critical infrastructure related matters.
The Director for Critical Infrastructure Protection within ASD/C3I will directly support the DoD CIAO and, through the establishment and management of the DoD CIP Integration Activity, will provide integration at two levels:
- Integration of the activities of the various DoD CIP organizational entities identified in this document
- Integration of extant DoD programs which will either contribute to or be realigned into a single comprehensive DoD Critical Infrastructure Protection program
Among such programs are the Critical Asset Assurance Program, the Infrastructure Assurance Program and the Defense-wide Information Assurance Program.
The DoD contingent to the NIPC is responsible for ensuring the integration of intelligence, counter-intelligence, and law enforcement in support of DoD critical infrastructure protection.
The DoD General Counsel [DoD(GC)] is responsible for legal review of critical infrastructure related matters.
The Chief Infrastructure Assurance Officer Council will provide executive oversight for the implementation of the DoD CIP Plan and advice to the ASD(C3I) regarding responsibilities as CIAO, CIO, and CIP Functional Coordinator for National Defense. The CIAO Council will be composed of senior department officials. The CIAO Council will be chaired by the ASD(C3I). Membership will include: Defense Sector Chief Infrastructure Assurance Officers (Sector CIAOs); Defense Special Function Coordinators; the Military Services; the Joint Staff; the JTF-CND Commander; the Manager, National Communications System; the Under Secretary of Defense (Comptroller) [USD(C)]; and the DoD(GC). The CIP Directorate will provide executive secretary support to the CIAO Council.
The DoD CIO Council was established in 1997 as the principal DoD forum to advise the Secretary and Deputy Secretary of Defense on the full range of matters pertaining to information technology (IT); to exchange pertinent information and discuss issues regarding DoD IT and IT management; and to coordinate the implementation of DoD activities under Division E (Information Technology Management Reform) of the Clinger-Cohen Act of 1996 (Public Law 104-106). For purposes of the CIO Council charter, the term "IT" encompasses both IT and national security systems (NSS) as defined in the Act. CIO Council members include the DoD CIO, the CIOs for the Departments of Air Force, Army and Navy; the Under Secretary of Defense for Acquisition and Technology [USD(A&T)]; the Under Secretary of Defense for Policy [USD(P)]; the USD(C); Director, Program Analysis and Evaluation [Director, PA&E]; CIO, Marine Corps; Director, Command, Control, Communications, and Computers, Joint Staff (J-6), and the Deputy CIO, DoD.
4.6 Lead Components for Defense Infrastructure Sector Assurance Coordination
Defense operations are supported by complex, interrelated, and decentralized networks of systems and services without single points of management that traverse DoD organizational boundaries. These support networks or defense infrastructure sectors research, design, develop, and produce defense-unique goods and services. They also acquire, add value to, assemble, and extend commercial services to defense operators.
The defense infrastructures share the vulnerabilities of the national infrastructures and have some unique vulnerabilities as well. They are also subject to the same business forces that exacerbate those vulnerabilities in the private sector. The defense infrastructure sectors are further described in Appendix B. Lead Components for DoD Infrastructure Sectors provide single focal points for planning and coordination of assurance activities within each sector.
Coordination is established as follows:
|
Defense Infrastructure Sector |
Lead Component for Sector Assurance Coordination |
|
Financial Services |
Defense Finance and Accounting Service |
|
Transportation |
US Transportation Command |
|
Public Works |
US Army (Corps of Engineers) |
|
Defense Information Infrastructure Command, Control, and Communications (C3) |
Defense Information Systems Agency |
|
Intelligence, Surveillance and Reconnaissance |
Defense Intelligence Agency |
|
Health Affairs |
OASD, Health Affairs |
|
Personnel |
Defense Human Resources Agency |
|
Emergency Preparedness |
US Army (Director of Military Support) |
|
Space |
US Space Command |
|
Logistics |
Defense Logistics Agency |
Responsibilities of the Lead Components for Sector Assurance Coordination include but are not limited to:
- Appointment of a senior official at the Flag / SES rank to serve as the Sector Chief Infrastructure Assurance Officer (CIAO) and to represent the sector on the CIAO Council
- Identification of the sector’s critical assets, to include NDI and INDI, and defense infrastructure characterization of the sector (see Section 5.1)
- Coordination with all DoD Components that own and/or operate elements of the sector to develop and implement a Sector Assurance Plan, which includes sector monitoring and reporting. General requirements for Sector Assurance Plans are at Appendix G
- Cooperation with the JTF-CND and the CIP Integration Activity in infrastructure protection and integration activities
- If applicable, participation in the CICG National Defense Coordination Sub-Group in order to coordinate with and monitor the activities of national Lead Agencies in support of NDI and INDI protection
- Appropriate legal review for assigned critical infrastructure matters
Critical assets fall into four broad categories:
- DoD assets that support Force Projection or other Military Plans and Operations
- DoD assets that are components of defense infrastructure sectors
- DoD assets that support the site, installation or unit
- NDI or INDI assets that support DoD critical assets
DoD critical assets will be the focus of implementation for the majority of DoD protection activities.
Heads of Components are responsible for:
- Assuring the availability, integrity, survivability and adequacy of critical assets IAW DoD Directive 5160.54, DoD Critical Asset Assurance Program (CAAP), 20 January 1998; the Defense-wide Information Assurance Program (DIAP), information assurance policy and programs; and the guidelines established in this document
- Cooperating with the applicable DoD Sector CIAO and Special Function Coordinators in the planning, coordinating, and execution of assurance activities
- Monitoring and reporting the assurance status of critical assets in accordance with Sector CIAO guidance and the Sector Assurance Plan
DoD installations occupy a special place in the CIP organizational structure in that they are the Department’s primary interface with host nation, federal, state and local law enforcement, emergency services personnel, and commercial infrastructure providers. DoD installations are likely to be the first to identify and react to infrastructure incidents.
Heads of Components will ensure that commanders of DoD installations worldwide review and support the assurance requirements of DoD Critical Asset Owners IAW DoDD 5160.54 and the guidelines of this document.
CIP efforts will closely coordinate with DoD’s Antiterrorism Force Protection (AT/FP) Program. CIP and Force Protection are complementary. CIP’s major concern is assuring the viability of infrastructures critical to mission success, whereas Force Protection has an installation viewpoint with emphasis on protecting people, facilities, and equipment. The Antiterrorism Force Protection Program has instituted Joint Staff Integrated Vulnerability Assessments (JSIVA) to review installation AT/FP programs. The JSIVAs look at physical security measures, AT/FP training, operational intelligence fusion, structures, and plans for responding to terrorist incidents. DoD’s CIP program will utilize these vulnerability assessments to preclude the potential for duplicative effort.
4.9 Lead Components for Coordination of DoD Special Functions
Lead Components for certain special functions are established to interface with the equivalent national Functional Coordinators and to coordinate all activities related to the function within the Department of Defense. The following table assigns the DoD Lead Components for these special functions.
|
Special Function |
DoD Lead Component |
National Lead Agency or Office of Primary Responsibility |
|
Military Plans and Operations |
Joint Staff |
NA |
|
International Cooperation (National = Foreign Affairs) |
Under Secretary of Defense for Policy |
Department of State |
|
Intelligence Support (National = Foreign Intelligence) |
Defense Intelligence Agency |
Central Intelligence Agency |
|
Research and Development |
Director of Defense Research and Engineering |
Office of Science and Technology Policy |
|
Education and Awareness |
National Defense University |
Critical Infrastructure Coordination Group |
Lead Component for Coordination with Military Plans and Operations
The primary focus of the DoD CIP program is the shielding or safeguarding of DoD operations from infrastructure compromise or disruption. The Joint Staff will take the lead, working with the Military Services and the DoD CIP organizational structure to ensure the following are incorporated into the military deliberate and crisis action planning process:
- Capability to quantify operational requirements for infrastructure services and to communicate those requirements by plan or operation to the defense infrastructure service providers
- Capability to identify operational dependencies upon and connectivity to infrastructures and to account for those dependencies in operational planning
- Capability to monitor infrastructure readiness and availability in preparation for and during operations
International cooperation in critical infrastructure protection issues and information exchange is pursued in coordination with the national CIP program with other nations, international organizations, and industrial security officials of nations with multinational corporations within their borders. Objectives may include, but are not limited to the following:
- Improving infrastructure assurance and emergency planning at military and supporting sites outside the United States
- Supporting intelligence activities
- Improving cooperation for incident response
- Understanding the impact of globalization on US infrastructure
- Ensuring that Defense Security Service (DSS) implementation mechanisms are appropriately included in existing and future international agreements whenever CIP and/or Information Assurance are addressed
Any applicable international agreements are distributed from Office of the Under Secretary of Defense - Policy [OUSD(P)] to the JTF-CND, DIA, the CIP Integration Activity, and affected DoD components. The CIP Integration Activity incorporates the agreements into the DoD CIP process and coordinates new requirements, which are passed to OUSD(P) for action. DSS will participate in the CIP Integration Activity to provide advice and support for implementing international industrial security related arrangements.
Intelligence Support
In addition to and complementing its national CIP responsibilities, the entire Defense Intelligence Community will work together under the leadership of the DoD Functional Coordinator for Intelligence Support and provide intelligence support to the Department of Defense in protection of the Defense portion of Federal Government Critical Infrastructure. The DoD Functional Coordinator for Intelligence Support will develop an annual CIP Intelligence Support Plan for consolidation into the DoD CIP Plan, and will provide status to the DoD CIAO Council on its implementation. The CIP Intelligence Support Plan will address the Defense Warning System (DWS), Alert & Notification, specific roles and responsibilities within the Defense Intelligence Community, and interfaces with the national Intelligence Community in the provision of:
- Timely and accurate state, non-state, (domestic and foreign), and individual (domestic and foreign) threat assessments, to include intentions and specific capabilities
- Indications and warning of all potential attacks to those elements of defense, national and global infrastructures essential to defense operations
This includes advice and support to Sector CIAOs in the development of defense infrastructure sector monitoring and reporting.
- Effective crisis management support for all contingencies affecting the security of those elements of defense, national and global infrastructures essential to defense operations
- Effective counter-intelligence in defense of those elements of defense, national and global infrastructures essential to defense operations
Support to the DoD contingent of the NIPC in the integration of intelligence, counter-intelligence, and law enforcement.
The Department of Defense will develop and manage an infrastructure and information assurance and protection research and development portfolio that complements and leverages the national portfolio. The Office of Director, Defense Research and Engineering will coordinate with the DoD CIAO, CIP Integration Activity, Sector CIAOs, and Service/Agency research and development activities to formulate a CIP DoD research and development agenda responsive to the Defense Sector and critical interdependency R&D needs. Additionally, the ODDR&E will coordinate with R&D activities ongoing within the DIAP, CAAP, IAP, and other programs that are identified to be CIP related. The CIP DoD R&D agenda will leverage ongoing research in DoD and the Federal Government. The ODDR&E, as the DoD representative and deputy co-chair to the National CIP R&D Interagency Working Group, will provide feedback and advice to the CIAO and Council regarding national issues and initiatives. The ODDR&E will reconcile the DoD agenda with the national R&D agenda and provide DoD input to the national agenda.
Although education and awareness may rightly be considered everyone’s responsibility, a comprehensive education and awareness strategy is essential for a successful DoD CIP program. The PCCIP Critical Foundations report repeatedly stresses the systemic lack of awareness regarding infrastructure vulnerabilities and PDD 63 calls for a national education and awareness program.
The National Defense University (NDU) will provide advice and assistance to the CIAO in assessing DoD education and awareness requirements and will develop and maintain the CIAO Education Program, which may be modeled after or combined with the CIO Certificate Program. The NDU may be tasked to assist in the development of any special education or training required for CIP crisis management personnel, e.g., those personnel assigned to the NIPC. The NDU will support both DoD and national CIP policy and strategy formulation and executive leadership development through periodic "infrastructure games." Additional information on the DoD CIO Certificate Program is available electronically at www.ndu.edu/irmc.
The Joint Task Force – Computer Network Defense is the primary DoD agent for the defense of DoD computer networks. In this role, the JTF will perform a variety of activities designed to synchronize technical, operational, and intelligence assessments of the nature of a computer network attack. The JTF will within the services and agencies, coordinate, and if necessary, direct the DoD response to a computer network attack (CNA) to limit the scope or impact of an attack, and coordinate and direct as required, actions to restore network functionality. Finally, the JTF will plan defensive measures to deter and defeat future computer network attacks. JTF-CND operations will be coordinated with the Services, unified Commands, DoD agencies, Joint Staff/OSD, law enforcement agencies, and the National Infrastructure Protection Center (NIPC). JTF-CND directive authority will flow from the Secretary of Defense for implementation by the task force. DISA will be the core and host of the JTF-CND.
The DoD CIP Integration Activity, under the policy guidance and oversight of the Director, Critical Infrastructure Protection and with the full time liaison of domain experts for the defense infrastructures, military operations and planning, infrastructure analysis and information assurance, will provide a common management environment within which the Critical Asset Assurance, Defense-wide Information Assurance, and Infrastructure Assurance Programs are planned, coordinated, implemented, and administered. The CIPIA will leverage these programs to assist the Sector CIAOs in the development of Sector Assurance Plans and the Special Function Coordinators in the development of annual CIP support plans. The CIPIA will support the integration of these plans into an overall DoD CIP plan and into the deliberate and crisis action planning process, and it will support the implementation of the DoD CIP Plan. Additionally, the CIPIA will:
- Coordinate with, and where appropriate, provide direct support to the JTF-CND or affected Component(s) responsible for the conduct of defensive operations in response to significant attacks on Defense Infrastructure
- Support the Sector CIAOs, Components, the JTF-CND, and the Defense Intelligence Community in the integration and implementation of defense infrastructure monitoring and reporting
- Map Defense Infrastructure to the National and International Defense Infrastructures
- Perform infrastructure interdependency analyses
- Prepare and coordinate DoD responses to the Critical Infrastructure Coordination Group, its sub-groups, or other interagency entities on behalf of the CIP Functional Coordinator and to the NIPC for other than operations affecting the JTF-CND
- Coordinate the activities of the DoD Lead Components with the national Lead Agencies and other interagency working groups
- Prepare and coordinate DoD input to the National Infrastructure Assurance Plan, interface with the National Plan Coordination Office, and function as the primary DoD interface to the national Information Sharing and Analysis Center(s)
- Support the development and administration of the Critical Asset Assurance Program
- Coordinate with and leverage other related DoD programs, e.g., Force Protection
- Coordinate and integrate infrastructure protection and information assurance
For information assurance, the DoD will be organized in accordance with the Defense-wide Information Assurance Program (DIAP), approved January 1998.
The differences and interrelationships among the Critical Asset Assurance Program, the Defense-wide Information Assurance Program and Critical Infrastructure Protection are illustrated in Figure 4-2. Further discussion of the CIP Integration Activity is provided at Appendix C. Additional information on the CAAP, IAP, and DIAP is available at Appendices D-F.
|
Differences and Interrelationships |
||
|
CAAP |
DIAP |
CIP |
|
Identifies Critical Assets (physical and information)
Provides business case for asset assurance investments Reconciles Component and Sector assurance activities Coordinates engineering standards for physical assurance designs, practices, and countermeasures Provides integrated risk management decision support environment |
Assists in identifying critical assets in the DII and C3 sectors Determines required level of information assurance for critical information assets in all DI sectors Provides business case for information assurance investments, especially shared risk remediation investments Provides engineering standards for information assurance designs, practices, and countermeasures |
Determines interrelationships among assets (both physical and information) within sectors and among sectors. Determines required level of infrastructure assurance for all DI sectors. Provides business case for infrastructure protection investments, especially I&W, Mitigation, & Response Links DI sectors to Military Plans and Ops Links DI CIP to national CIP |
Figure 4-2. CAAP, DIAP, CIP Differences and Interrelationships
4.12 The CICG National Defense Coordination Sub-Group
The Director for Critical Infrastructure Protection will chair a permanent sub-group to the interagency Critical Infrastructure Coordination Group (CICG) for coordination of National Defense related issues. The Sub-Group will assist the Functional Coordinator for National Defense in the planning for and provision of infrastructure services required for national defense under all circumstances, including crisis or emergency, attack, recovery and reconstitution. This sub-group will link DoD Critical Infrastructure Protection efforts to national efforts and provide the mechanism for addressing national defense requirements in the national infrastructure sectors. Specifically, the sub-group will ensure that the National Defense Infrastructure identified by the DoD CIP program is incorporated in the national Sector Assurance Plans and in the NIAP.
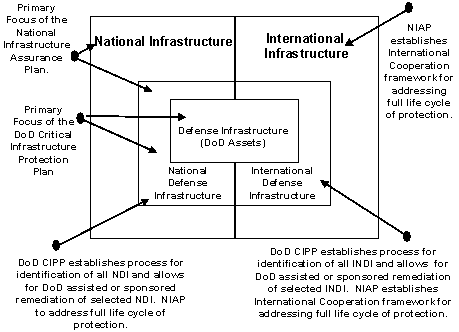
Figure 4-3. Interrelationships Between DoD CIP Plan and NIAP
Proposed membership for the CICG National Defense Coordination Sub-Group is listed on the following page.
|
National |
Defense |
|
|
SECTOR LIAISON |
Dept of Treasury – Banking and Finance |
Defense Finance & Accounting Service (DFAS) – Defense Financial Services |
|
Dept of Energy - Electric Power and Oil and Gas Storage and DistributionEnvironmental Protection Agency – Water Supply |
U.S. Army (Corps of Engineers) – Defense Public Works (includes all installation level utilities, e.g., electric power, fuels, and water supply) |
|
|
Dept of Transportation – all transportation sub-sectors |
U.S. Transportation Command (USTRANSCOM) – Defense Transportation |
|
|
National Communications System – Telecommunications for National Security and Emergency PreparednessDept of Commerce – Information and Communications |
Defense Information Systems Agency (DISA) – the Defense Information Infrastructure (DII) and Command, Control and Communications (C3) |
|
|
Federal Emergency Management Agency – Continuity of Government Services and Emergency Fire Protection ServicesDept of Justice/FBI – Emergency Law Enforcement Services |
U.S. Army (Directorate of Military Support) – Emergency Preparedness |
|
|
Department of Health and Human Services – Public Health |
Assistant Secretary of Defense (Health Affairs) – Health Affairs |
|
|
National |
Defense |
|
|
SPECIAL FUNCTIONS |
Department of State – Foreign Affairs |
Under Secretary of Defense for Policy – International Cooperation |
|
Central Intelligence Agency – Foreign Intelligence |
Defense Intelligence Agency – Intelligence Support |
|
|
Department of Justice/FBI – Law Enforcement and Internal Security |
Joint Staff – Military Plans and Operations |
|
|
National Infrastructure Protection Center – Warning and Response |
Joint Task Force - Computer Network Defense (JTF-CND) – Warning and Response |
|
|
Office of Science and Technology Policy – Research and Development |
Directorate of Defense Research and Engineering (DDR&E) – Research and Development |
|
(page is intentionally blank)
5. The DoD Critical Infrastructure Protection Life Cycle
The DoD has improved operational
readiness through a comprehensive, fully integrated and sustainable process of life-cycle protection for those elements of defense, national, and global infrastructures essential to DoD. – DoD CIP Vision 2000The six life cycle phases – Infrastructure Analysis and Assessment, Remediation, Indications and Warning, Mitigation, Response, and Reconstitution – span activities that occur before, during, and after events which may result in infrastructure compromise or disruption. As shown in the figure, Infrastructure Analysis and Assessment, Remediation, and Indications and Warning primarily occur before events. Mitigation occurs both before and during events. Response occurs during events, and Reconstitution may start during events but is generally concentrated afterward. The figure also shows which entities within the DoD and national organizational structures have primary assurance or protection responsibilities in which phases. Supporting and coordinating entities have responsibilities throughout the life cycle that will be described later in this section. The activities of national CIP entities in this section represent current understanding and planning assumptions, and are included to provide a context for DoD activities. This characterization of the activities of national CIP entities is intended to be neither comprehensive nor directive in nature. Figure 5-1 illustrates the DoD CIP life cycle.
|
Before Event |
During Event |
After Event |
||||||
|
Analysis & Assessment |
Remediation |
Indications and Warning1 |
Mitigation |
Response |
Reconstitution |
|||
|
Critical Asset Owners |
u |
u |
u |
u |
u |
|||
|
DoD Installations |
u |
u |
u |
u |
u |
u |
||
|
DI Sector CIAOs |
u |
u |
u |
u |
u |
|||
|
JTF-CND |
u |
u |
||||||
|
NIPC |
u |
u |
u |
|||||
|
Natl Sector Liaison Officials |
u |
u |
u |
u |
u |
|||
|
1 Critical Asset Owners, DoD Installations, Defense Infrastructure Sector CIAOs and National Sector Liaison Officials are responsible for monitoring critical assets and infrastructure sectors and for reporting incidents, which may be indicators. |
||||||||
Figure 5-1. The DoD Critical Infrastructure Protection Life Cycle
Within each cell of this life cycle matrix, the responsible entity will be able to select among protection activities ranging from immediate and low-to-no cost, e.g., increased awareness, to programmed asset or infrastructure improvements. An increasing number of protection activities will be aimed at the risks inherent in shared environments, and therefore require collaboration among entities to be effective. Some protection activities will have prerequisites, that is, activities must build upon one another. Protection activities that have a cumulative effect may be grouped within a single cell, down a given column, across a given row, or across multiple rows and columns.
The Infrastructure Analysis and Assessment phase encompasses a continuum of activities:
Critical Asset Identification
Through coordinated domain expertise and inspection, assets that are critical for military operations or defense infrastructure operations are identified to the Critical Asset Assurance Program Critical Assets and include DI, NDI, and INDI components. The CAAP will have the capability to associate criticality attributes to the asset and to derive a criticality index for planning.
Defense Infrastructure Characterization
Through coordinated domain expertise and the application of systems engineering and analysis methods and modeling and simulation technologies, critical asset functions and relationships within a defense infrastructure sector are mapped and associated with the critical assets in the Critical Asset Assurance Program Defense Infrastructures are also mapped to the National and International Defense Infrastructures.
Operational Impact Analysis
Through the development of operational dependency matrices and the application of operations research methods, the relationship between military plans and operations and critical assets is established along with the service level requirements such as maximum allowable down time. This information is associated with both the military plan/operation and the critical asset. Potential operational impacts and service level requirements will be reflected in the asset’s criticality attributes and criticality index.
Vulnerability Assessment
Through CAAP, all critical assets will have an associated baseline vulnerability index which is calculated from inputs associated with the class of asset and geographic region (i.e., probability of natural disasters, criminal or national security events, technological failures, etc.). Information regarding asset operational readiness and emergency preparedness will be associated with the critical asset and factored into the vulnerability index rating. Asset operational readiness and emergency preparedness information may be provided by the asset owner, the host installation, the Sector CIAO, or by various Defense programs (e.g., National Industrial Security Program).
Interdependency Analysis
Through coordinated domain expertise and the application of systems engineering and analysis methods and modeling and simulation technologies, functions and relationships among defense infrastructure sectors will be mapped. The criticality attributes of current critical assets may be updated and additional critical assets may be identified to the Critical Asset Assurance Program.
|
Infrastructure Analysis and Assessment Activities by Organizational Entity |
||
|
Organizational Entity |
Activities |
Comments |
|
DoD Critical Asset Owners |
Critical Asset Identification Asset Level Vulnerability Assessment |
Coordinate with DI Sector CIAOs, Military Plans & Operations Functional Coordinator & DoD CIP Integration Activity |
|
DoD Installations |
Installation Level Vulnerability Assessment Critical Asset Identification |
Coordinate among tenants |
|
DI Sector CIAOs |
Defense Infrastructure Characterization DI Sector Level Vulnerability Assessment Critical Asset Identification |
Coordinate with Critical Asset Owners, Military Plans & Operations Functional Coordinator, & DoD CIP Integration Activity |
|
DoD Functional Coordinator for Military Plans & Operations |
Operational Impact Analysis Military Operations Critical Asset Identification |
Sponsor and coordinate |
|
DoD Functional Coordinator for Intelligence Support |
Provide threat information |
|
|
DoD Functional Coordinator for Research and Development |
Provide tools, methods, and models |
|
|
DoD CIP Integration Activity |
Defense Infrastructure Interdependency Analysis Operational Impact Analysis Defense-wide Vulnerability Assessment Defense Infrastructure Characterization Critical Asset Identification |
Sponsor Defense-wide analysis and assessment Provide technical and systems support and integration for all other levels |
|
DoD CIAO Council |
Provide oversight and resources, set priorities |
|
|
CIP Functional Coordinator for National Defense |
Critical Asset Identification |
Identify to National Sector Liaison Officials those assets in the national infrastructure sectors that are critical to National Defense |
|
National Sector Liaison Officials |
National Sector Critical Asset Identification National Sector Infrastructure Characterization National Sector Vulnerability Assessment |
|
|
NIPC |
National Interdependency Analysis Nation-wide Vulnerability Assessment Nation-wide and Federal Government-wide operational impact analysis |
|
Remediation refers to those precautionary actions taken before undesirable events occur to improve known deficiencies and weaknesses that could cause an outage or compromise a defense infrastructure sector or critical asset. The precautions are applicable regardless of whether those events are acts of nature, technology, or malicious actors. Remediation may include education and awareness, operational process or procedural changes, system configuration changes (e.g., physical diversity, redundancy, deception) or system component changes (e.g., hardware, software, links).
The Defense Infrastructure Sector Assurance Plans establish priorities and resources for remediation. Requirements are determined by the following:
- Analysis and assessment
- Input from military planners
- Input from other Defense Infrastructure sectors
- Lessons learned from Defense Infrastructure sector monitoring and reporting
- The National Infrastructure Assurance Plan and other plans, reports, and information on national infrastructure vulnerabilities and remediation
- Lessons learned from infrastructure protection operations and exercises
- Intelligence estimates and assessments of threats
The Critical Asset Assurance Program will provide the means to track the status of remediation activities for critical assets.
|
Remediation Activities by Organizational Entity |
|
|
DoD Critical Asset Owners |
Resource and perform asset level remediation |
|
DoD Installations |
Resource and perform installation level remediation |
|
DI Sector CIAOs |
Resource and perform sector level remediation Integrate and reconcile asset level remediation within each sector |
|
DoD Functional Coordinator for Military Plans and Operations |
Ensure the results of operational impact analysis are considered during the deliberate and crisis action planning process |
|
DoD Functional Coordinator for Research and Development |
Provide design and material improvements to critical assets and defense infrastructure configuration and management |
|
DoD CIP Integration Activity |
Integrate and reconcile defense sector level remediation |
|
DoD CIAO Council |
Provide oversight and resources, set priorities |
|
DoD CIO Council |
Sponsor development of IT remediation solutions and their incorporation in IT systems |
|
CIP Functional Coordinator for National Defense (supported by CICG National Defense Coordination Sub-Group) |
Monitor national sector remediation activities and advocate remediation for national infrastructure assets that are critical to national defense. |
|
National Sector Liaison Officials |
Coordinate development and implementation of national Sector Assurance Plans |
Infrastructure indications are preparatory actions or preliminary infrastructure conditions that signify that an incident is likely, is planned, or is under way. This definition both embraces and expands upon the Department’s traditional focus on intelligence of foreign developments. Expansion is necessary because the indications may be related to domestic criminal activity or technical anomalies that indicate system failure or degradation is likely. Infrastructure owners and operators are the most likely detectors of changes in infrastructure state, and must therefore be considered full partners in the indications process. The innovative fusion of traditional intelligence information with sector monitoring and reporting information is essential for critical infrastructure indications and warning.
When a determination is made that an infrastructure incident is likely to occur, is planned, or is under way, an official warning is issued by the responsible organization. The NIPC is the primary national warning center for significant infrastructure attacks. It will exchange information aimed at improving the definition and collection of I&W for DoD CIP with the Service Law Enforcement and Counter-Intelligence Communities, DIA and the CIP Integration Activity. Indications of infrastructure incidents will be defined, observed and reported by the Defense Infrastructure Sectors and DoD Components to the NMCC. Indications of computer network attacks will also be reported to the JTF-CND. The NMCC and JTF-CND will assess these indications and pass them on to the NIPC and appropriate DoD organizations. These initial assessments will be used for tactical warning. DIA and NIPC will provide long range indications and warning. The CIPIA and JTF-CND will provide the IC with priority intelligence requirements (PIR) and indications and warning requirements for potential attacks against DoD infrastructure.
The NMCC and JTF-CND will pass the NIPC warnings and alerts to the DoD Components. These warnings may include or be supplemented with guidance regarding additional protection measures DoD should take.
DoD Critical Asset Owners and Sector CIAOs are responsible for monitoring events and conditions that could or have led to disruption of operations or provision of services to DoD and for reporting appropriately.
|
Indications and Warning Activities by Organizational Entity |
|
|
DoD Critical Asset Owners |
Participate in the definition of reportable incidents. Monitor and report infrastructure incidents. |
|
DoD Installations |
Participate in the definition of reportable incidents. Monitor and report infrastructure incidents. |
|
Sector CIAOs |
Develop and implement sector monitoring and reporting IAW Appendix G of this document. |
|
NMCC/NMJIC and JTF-CND |
Receive, consolidate, and assess sector reports. Develop DoD indications through the fusion of sector reports with traditional intelligence information. Report DoD indications to the NIPC. Issue DoD warning. Receive, assess, and disseminate national warning. |
|
DoD CIP Integration Activity |
Provide technical integration, support and process improvement. |
|
DoD Functional Coordinator for Research and Development |
Provide improved materials, tools, methods, and models for detection. |
|
DoD Functional Coordinator for Intelligence Support |
Provide intelligence support to the NMCC and JTF-CND. Provide expert advice, assistance and support to Sector CIAOs in the development and implementation of DI sector monitoring and reporting. |
|
DoD CIAO Council |
Provide oversight and resources, set priorities. |
|
CIP Functional Coordinator for National Defense (supported by CICG National Defense Coordination Sub-Group) |
Participate in the development of national indications requirements. Participate in the design of national sector monitoring and reporting. |
|
NIPC |
Lead the development of national indications requirements. Participate in the design and development of national sector monitoring and reporting. Receive, consolidate, and assess national sector reporting. Develop infrastructure indications through the fusion of national sector reporting and traditional intelligence information. Issue national warning. |
|
National Sector Liaison Officials |
Lead the design, development, and implementation of national sector monitoring and reporting. |
Mitigation actions are those actions taken by DoD Critical Asset Owners, DoD Installations, defense infrastructure sectors, and military operators in response to an infrastructure warning or incident. Mitigation actions are intended to minimize or alleviate the potentially adverse effects on a given military operation or infrastructure, facilitate incident response, and quickly restore the infrastructure service. Such actions may include measures to safeguard information, gracefully degrade service or shed load in accordance with established priorities, restart equipment or software, or switch to emergency or backup service options.
DoD Critical Asset Owners, DoD Installations, and Sector CIAOs, in concert with the NMCC and the JTF-CND develop, train for and exercise mitigation responses in various scenarios. The CAAP provides the means to programmatically track mitigation plans and attendant approval and coordination requirements.
DoD Critical Asset Owners, DoD Installations, and Sector CIAOs, during times of warning, emergency, and/or infrastructure incidents, are responsible for initiating mitigation action to sustain services to DoD and for providing status information to the NMCC and JTF-CND.
The NMCC monitors for consequences within one defense infrastructure sector that extend enough to significantly affect other sectors, for events occurring across two or more sectors and advises on prioritization and coordination of mitigating actions. Continued escalation of either the threat or consequences results in NMCC activation of appropriate authority to direct mitigation actions by sector to ensure DoD-wide coordination and response.
The NMCC and the JTF-CND keep the NIPC apprised of any significant mitigation activities.
|
Mitigation Activities by Organizational Entity |
|
|
DoD Critical Asset Owners |
Develop, train for, and exercise asset level mitigation activities. Initiate asset level mitigation activities in response to warning, emergency, or infrastructure incident. Report mitigation status to the NMCC, JTF-CND, and affected Sector CIAOs. |
|
DoD Installations |
Develop, train for, and exercise installation level mitigation activities. Initiate installation level mitigation activities in response to warning, emergency, or infrastructure incident. Report mitigation status to the NMCC, JTF-CND, and affected Sector CIAOs. |
|
Sector CIAOs |
Integrate and reconcile asset level mitigation planning and activities within the sector. Develop, train for, and exercise sector level mitigation activities. Initiate sector level mitigation activities in response to warning, emergency, or infrastructure incident. Report mitigation status to the NMCC and JTF-CND. |
|
NMCC and JTF-CND |
Monitor emergencies and incidents, provide mitigation status to affected DoD entities and Components, and recommend or direct mitigation activities. |
|
DoD CIP Integration Activity |
Provide technical integration support to the NMCC, JTF-CND, and Sector CIAOs. |
|
DoD CIAO Council |
Provide oversight and resources, set priorities |
|
DoD CIO Council |
Enable mitigation activities through IT. |
|
CIP Functional Coordinator for National Defense (supported by CICG National Defense Coordination Sub-Group) |
Advocate mitigation planning within national sectors, especially for assets critical to National Defense. Sponsor "joint" planning, training and exercise of the coordination and interface between DoD and national mitigation activities at all levels – asset, infrastructure sector, and national defense. |
|
NIPC |
Monitor national emergencies and incidents, provide mitigation status to affected national entities, and recommend mitigation activities. |
|
National Sector Liaison Officials |
Lead national sectors in the planning, training and exercise of mitigation activities. |
Response refers to those activities undertaken to eliminate the cause or source of an event. It includes emergency measures from dedicated third parties (i.e., not the asset owners/operators themselves) such as law enforcement, investigation, medical, and fire and rescue. Response to incidents impacting DoD owned assets may take one of two paths, depending on whether the impacted asset is under the defense of the JTF-CND. Response to incidents impacting assets under the defense of the JTF-CND will follow JTF-CND direction. Response to incidents involving all other DoD-owned assets will follow traditional channels and procedures, coordinated by installation commanders and critical asset owners. Sector CIAOs will be included in initial notification and status reporting for all incidents on all assets within their sectors. Initial response to incidents impacting NDI is a law enforcement responsibility, whether local, state, or federal, and coordinated by the National Infrastructure Protection Center (NIPC) as appropriate.
DoD Critical Asset Owners and Sector CIAOs are responsible for coordinating mitigation and reconstitution activities with the incident responders, to include the NIPC for assets not under the defense of the JTF-CND.
The primary function of the JTF-CND is to staff, plan, train, and conduct defense and response operations for the DoD computer networks. The JTF-CND coordinates or directs appropriate actions within the DoD to stop the computer network attack, contain and mitigate damage, and restore minimum required functionality. The JTF-CND is responsible for requesting and coordinating any support or assistance from other Federal agencies and civilian organizations during any incident for which it has responsibility.
|
Incident Response Activities by Organizational Entity |
|
|
DoD Critical Asset Owners |
Coordinate with appropriate response entities. |
|
DoD Installations |
Plan, train for, and exercise local emergency response. Coordinate with appropriate response entities. |
|
Sector CIAOs |
Monitor response activities and coordinate appropriate sector mitigation and reconstitution activities. Provide support to the NMCC. |
|
JTF-CND |
Respond to incidents impacting assets under its defense. |
|
NMCC |
Monitor status of response activities. |
|
DoD CIP Integration Activity |
Provide technical support to the NMCC, the JTF-CND and Sector CIAOs. |
|
NIPC |
Coordinate national response. |
|
National Sector Liaison Officials |
Monitor incident response activities and coordinate appropriate national sector mitigation and reconstitution activities. Provide support to the NIPC. |
Reconstitution refers to the actions required to rebuild or restore an infrastructure after it has been damaged.
Asset owners are responsible for reconstitution and status reporting to the NMCC. The affected Sector CIAOs are responsible for monitoring and coordinating reconstitution efforts, for providing any sector specific reports to the NMCC, and for conducting any sector level reviews. DoD Critical Asset Owners are responsible for identifying any changes to Critical Assets and Sector CIAOs are responsible for reflecting any changes to the sector configuration or architecture in the DI sector characterization. The NMCC coordinates any NIPC information requirements regarding reconstitution.
Following certain significant computer network attacks, the JTF-CND, in conjunction with the NIPC, will hold an after-action review to collect lessons learned. This information will be shared with the Sector CIAOs and affected Components for consideration in reconstitution. All post-computer incident status reporting, as well as after-action reports and reviews with the NIPC, is the responsibility of the JTF-CND. The JTF-CND also advises on substantial computer network reconstitution activities within the DoD and reports the status of these activities to the NMCC and NIPC as appropriate.
|
Reconstitution Activities by Organizational Entity |
|
|
DoD Critical Asset Owners |
Reconstitute critical assets. Report status of reconstitution efforts to Sector CIAOs. |
|
DoD Installations |
Support the reconstitution activities of DoD Critical Asset Owners. |
|
Sector CIAOs |
Monitor reconstitution activities. Share information with the NMCC, the JTF-CND and NIPC as appropriate. Conduct sector level reviews and sponsor or initiate CIP process improvements. Update DI sector characterization. |
|
JTF-CND |
Monitor and advise on reconstitution of assets under its defense. Provide input from response after action analysis to Sector CIAOs and affected Component(s) for consideration in reconstitution. |
|
NMCC |
Monitor reconstitution of significant DoD assets and coordinate any NIPC information requirements. |
|
DoD CIP Integration Activity |
Provide technical support to the NMCC, the JTF-CND, affected Component(s) and Sector CIAOs. |
|
DoD CIAO Council |
Provide oversight and resources, set priorities |
|
DoD CIO Council |
Incorporate and leverage IT advances in reconstitution. |
|
CIP Functional Coordinator for National Defense (supported by CICG National Defense Coordination Sub-Group) |
Represent DoD requirements and equities in the reconstitution of national infrastructure assets. |
|
NIPC |
Provide incident response review results as input to reconstitution planning. Monitor significant national infrastructure reconstitution efforts and coordinate as appropriate. |
|
National Sector Liaison Officials |
Monitor reconstitution activities within sector. Share information with the NIPC as appropriate. Conduct national sector level reviews and sponsor or initiate CIP process improvements. Update national sector characterization. |
|
FEMA |
Function as the Lead Agency for Consequence Management of national emergencies IAW the Federal Response Plan |
Organizational Entity Activities Across the DoD CIP Life Cycle
The following tables group DoD CIP life cycle activities by organizational entity.
|
DoD Critical Asset Owner Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
Critical Asset Identification Asset Level Vulnerability Assessment Coordinate with Sector CIAOs, Military Plans & Operations Functional Coordinator & DoD CIP Integration Activity |
|
Remediation |
Resource and perform asset level remediation. |
|
Indications and Warning |
Participate in the definition of reportable incidents. Monitor and report infrastructure incidents |
|
Mitigation |
Develop, train for, and exercise asset level mitigation activities. Initiate asset level mitigation activities in response to warning, emergency, or infrastructure incident. Report mitigation status to NMCC, JTF-CND, and affected Sector CIAOs. |
|
Incident Response |
Coordinate with appropriate response entities. |
|
Reconstitution |
Reconstitute critical assets. Report status of reconstitution efforts to Sector CIAOs. |
|
DoD Installation Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
Installation Level Vulnerability Assessment Critical Asset Identification Coordinate among tenants. |
|
Remediation |
Resource and perform installation level remediation. |
|
Indications and Warning |
Participate in the definition of reportable incidents. Monitor and report infrastructure incidents. |
|
Mitigation |
Develop, train for, and exercise installation level mitigation activities. Initiate installation level mitigation activities in response to warning, emergency, or infrastructure incident. Report mitigation status to NMCC, JTF-CND, and affected Component(s) and Sector CIAOs. |
|
Incident Response |
Plan, train for, and exercise local emergency response. Coordinate with appropriate response entities. |
|
Reconstitution |
Support the reconstitution activities of DoD Critical Asset Owners. |
|
Defense Infrastructure Sector CIAO Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
Defense Infrastructure Characterization DI Sector Level Vulnerability Assessment Critical Asset Identification Coordinate with DoD Critical Asset Owners, Military Plans & Operations Functional Coordinator, & DoD CIP Integration Activity. |
|
Remediation |
Resource and perform sector level remediation Integrate and reconcile asset level remediation within each sector |
|
Indications and Warning |
Develop and implement sector monitoring and reporting IAW Appendix G of this document. |
|
Mitigation |
Integrate and reconcile asset level mitigation planning and activities within the sector. Develop, train for, and exercise sector level mitigation activities. Initiate sector level mitigation activities in response to warning, emergency, or infrastructure incident. Report mitigation status to the NMCC and JTF-CND. |
|
Incident Response |
Monitor response activities and coordinate appropriate sector mitigation and reconstitution activities. Provide support to the NMCC. |
|
Reconstitution |
Monitor reconstitution activities. Share information with the NMCC, the JTF-CND and NIPC as appropriate. Conduct sector level reviews and sponsor or initiate CIP process improvements. Update DI sector characterization. |
|
JTF-CND Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
|
|
Remediation |
|
|
Indications and Warning |
Receive, consolidate, and assess sector reports. Develop DoD indications through the fusion of sector reports with traditional intelligence information. Report DoD indications to the NIPC. Issue DoD warning. Receive, assess, and disseminate national warning. |
|
Mitigation |
Monitor emergencies and incidents, provide mitigation status to affected DoD entities and Components, and recommend or direct mitigation activities. |
|
Incident Response |
Respond to incidents impacting assets under its defense. |
|
Reconstitution |
Monitor and advise on reconstitution of assets under its defense. Provide input from response after action analysis to Sector CIAOs for consideration in reconstitution. |
|
NMCC / NMJIC Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
|
|
Remediation |
|
|
Indications and Warning |
Receive, consolidate, and assess sector reports. Develop DoD indications through the fusion of sector reports with traditional intelligence information. Report DoD indications to the NIPC. Issue DoD warning. Receive, assess, and disseminate national warning. |
|
Mitigation |
Monitor emergencies and incidents, provide mitigation status to affected DoD entities and Components, and recommend or direct mitigation activities. |
|
Incident Response |
Monitor status of response activities. |
|
Reconstitution |
Monitor reconstitution of significant DoD assets and coordinate any NIPC information requirements. |
|
DoD CIP Integration Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
Defense Infrastructure Interdependency Analysis Operational Impact Analysis Defense-wide Vulnerability Assessment Defense Infrastructure Characterization Defense Infrastructure mapping to National and International Defense Infrastructures Critical Asset Identification Technical and systems support and integration for all levels. |
|
Remediation |
Integrate and reconcile defense sector level remediation |
|
Indications and Warning |
Provide technical integration, support and process improvement. |
|
Mitigation |
Provide technical integration support to the NMCC, JTF-CND, affected Component(s), and Sector CIAOs. |
|
Incident Response |
Monitor status of response activities. |
|
Reconstitution |
Provide technical support to the NMCC, JTF-CND, affected Component(s), and DI Sector CIAOs. |
|
DoD Functional Coordinator for Military Plans and Operations |
|
|
Infrastructure Analysis and Assessment |
Sponsor and coordinate Operational Impact Analysis Sponsor and coordinate Military Operations Critical Asset Identification |
|
Remediation |
Ensure the results of operational impact analysis are considered during the deliberate and crisis action planning process |
|
Indications and Warning |
|
|
Mitigation |
|
|
Incident Response |
|
|
Reconstitution |
|
|
DoD Functional Coordinator for Research and Development Activities |
|
|
Infrastructure Analysis and Assessment |
Provide tools, methods, and models for all analysis and assessment activities. |
|
Remediation |
Provide design and material improvements to critical assets and defense infrastructure configuration and management. |
|
Indications and Warning |
Provide improved materials, tools, methods, and models for detection. |
|
Mitigation |
|
|
Incident Response |
|
|
Reconstitution |
|
|
DoD Functional Coordinator for Intelligence Support Activities |
|
|
Infrastructure Analysis and Assessment |
Provide threat information for all levels of vulnerability assessment. |
|
Remediation |
|
|
Indications and Warning |
Provide intelligence support to the NMCC and JTF-CND. Technically support the development and implementation of DI sector monitoring and reporting. |
|
Mitigation |
|
|
Incident Response |
|
|
Reconstitution |
|
|
DoD CIAO Council Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
Provide oversight and resources, set priorities. |
|
Remediation |
|
|
Indications and Warning |
|
|
Mitigation |
|
|
Incident Response |
|
|
Reconstitution |
|
|
DoD CIO Council Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
|
|
Remediation |
Sponsor development of IT remediation solutions and their incorporation in IT systems |
|
Indications and Warning |
|
|
Mitigation |
Enable mitigation activities through IT. |
|
Incident Response |
|
|
Reconstitution |
Incorporate and leverage IT advances in reconstitution |
|
CIP Functional Coordinator for National Defense Activities (supported by the CICG National Defense Coordination Sub-Group) |
|
|
Infrastructure Analysis and Assessment |
Identify to National Sector Liaison Officials those assets in the national infrastructure sectors that are critical to National Defense. |
|
Remediation |
Monitor national sector remediation activities and advocate remediation for national infrastructure assets which are critical to national defense. |
|
Indications and Warning |
Participate in the development of national indications requirements. Participate in the design of national sector monitoring and reporting. |
|
Mitigation |
Advocate mitigation planning within national sectors, especially for assets critical to National Defense. Sponsor "joint" planning, training and exercise of the coordination and interface between DoD and national mitigation activities at all levels – asset, infrastructure sector, and national defense. |
|
Incident Response |
|
|
Reconstitution |
Represent DoD requirements and equities in the reconstitution of national infrastructure assets. |
|
NIPC Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
National Interdependency Analysis Nation-wide Vulnerability Assessment Nation-wide and Federal Government-wide operational impact analysis |
|
Remediation |
|
|
Indications and Warning |
Lead the development of national indications requirements. Participate in the design and development of national sector monitoring and reporting. Receive, consolidate, and assess national sector reporting. Develop infrastructure indications through the fusion of national sector reporting and traditional intelligence information. Issue national warning. |
|
Mitigation |
Monitor national emergencies and incidents, provide mitigation status to affected national entities, and recommend mitigation activities. |
|
Incident Response |
Coordinate national response. |
|
Reconstitution |
Provide incident response review results as input to reconstitution planning. Monitor significant national infrastructure reconstitution efforts and coordinate as appropriate. |
|
National Sector Liaison Official Activities Across the DoD CIP Life Cycle |
|
|
Infrastructure Analysis and Assessment |
National Sector Critical Asset Identification National Sector Infrastructure Characterization National Sector Vulnerability Assessment |
|
Remediation |
Coordinate development and implementation of national Sector Assurance Plans. |
|
Indications and Warning |
Lead the design, development, and implementation of national sector monitoring and reporting. |
|
Mitigation |
Lead national sectors in the planning, training and exercise of mitigation activities. |
|
Incident Response |
Monitor incident response activities and coordinate appropriate national sector mitigation and reconstitution activities. |
|
Reconstitution |
Monitor reconstitution activities within sector. Share information with the NIPC as appropriate. Conduct national sector level reviews and sponsor or initiate CIP process improvements. Update national sector characterization. |
|
Activity |
FY 1999 |
FY 2000 |
||||||
|
1Q |
2Q |
3Q |
4Q |
1Q |
2Q |
3Q |
4Q |
|
|
Approve and distribute DoD CIP Plan Version 1.0 |
u |
|||||||
|
Establish CIAO Council |
u |
|||||||
|
Establish National Defense Coordination Sub-Group |
u |
|||||||
|
Develop DoD CIP Plan Version 2.0 (Integrated Defense Infrastructure Sector Assurance Plans) |
u |
|||||||
|
Implement DoD CIP Plan Version 2.0 |
u |
|||||||
|
Implementation Schedule |
|
|
Nov 1998 |
DoD CIP Plan Version 1.0 approved and distributed |
|
Dec 1998 |
CIAO Council established |
|
Jan 1999 |
National Defense Coordination Sub-Group charter and issues/requirements for preliminary work plan reviewed by CIAO Council |
|
Jan 1999 |
Sector and Special Function Plan guidance published |
|
Feb 1999 |
National Defense Coordination Sub-Group established |
|
Apr 1999 |
Status of Sector and Special Function Plans reviewed by CIAO Council |
|
Jul 1999 |
Completed Sector and Special Function Plans submitted for integration into DoD CIP Plan V 2.0 |
|
Sep 1999 |
DoD CIP Plan V 2.0 reviewed by CIAO Council |
|
Oct 1999 |
DoD CIP Plan V 2.0 approved and published |
|
Oct 2000 |
DoD CIP Plan V 2.0 implemented |
(page is intentionally blank)
In support of developing the baseline, and to respond to requests from the Office of Management and Budget (OMB) and the National Security Council (NSC) to identify CIP funding, OUSD(C) has developed proposed policy guidance and submission requirements to identify existing baseline funding. Key elements of that guidance are provided below. OUSD(C) will provide final guidance in a special CIP FY 2000/2001 Budget Call.
The CIP budget submission will require DoD elements to identify baseline CIP program funding levels by appropriation for each Defense Infrastructure Sector and will include an accelerated program review (see attachment 1, next page). These program reviews will be conducted jointly by the Program Analysis and Evaluation (PA&E) and Program/Budget staff, OASD (C3I), and will be supported by the CIP Sector Lead Components. The results will be used to produce the specified OMB/NSC CIP program data sheets. Specific guidance is contained in the attachments and is applicable to all appropriations and fund accounts of the DoD.
This CIP Plan will be the basis for responding to the OMB/NSC budget call. To facilitate completion of this program and budget review, Lead Component organizations should provide the names, phone numbers, and email addresses of their program and financial points of contact to Ms. Sallie Morse by email to [email protected].
The results of the overall CIP effort will be documented in a Program Budget Decision during the latter portion of the FY 2000/2001-budget review. A formal response to the OMB/NSC data call will be forwarded after the CIP baseline and programmatic adjustments are finalized.
Attachment 1
BUDGET SUBMISSION: CIP BASELINE
Purpose
: Information on critical infrastructure protection (CIP) resource levels is required by the Office of Management and Budget (OMB) and the National Security Council (NSC) as part of a government-wide crosscut program and budget review for FY 2000. This same data is also required by the Department to effectively program and manage the CIP Program.Submission Requirements: Each DoD Component will complete the CIP Exhibit 1, Critical Infrastructure Protection Funding, to correspond with their FY 2000/2001 Budget Estimates Submission. Specific instructions are provided on the following pages. Four copies of each completed CIP Exhibit 1 should be provided to the OUSD(C) Program/Budget Operations and Personnel, Room 3D868.
Special Instructions:
a. The ASD (C3I) Director for Critical Infrastructure Protection; ODASD (Security and Information Operations) will participate with representatives of the OUSD(C), ODPA&E, and OMB in the review of all CIP budget exhibits to ensure reporting consistency across DoD and to comply with government-wide program directions.
b. Each Lead Component for Sector Assurance will participate with the ASD (C3I), OUSD(C), and ODPA&E in appropriate working group efforts to review/assess CIP baseline budget submissions.
c. CIP resources will be reported at the Defense Infrastructure Sector (Sector) program level. Within DoD, the CIP Director has established 7 programs that correspond to the CIP life cycle phases. These programs are infrastructure analysis and assessment, remediation, indications and warning, mitigation, response, reconstitution, and all phases. Tab A provides definitions for the Sector programs. Only these programs will be used to complete the CIP budget exhibit.
d. OMB/NSC requires that the cost of personnel supporting CIP activities be identified. DoD Components should report the military pay and civilian pay for personnel who are dedicated full-time to CIP activities (for the purposes of this exhibit, dedicated equates to those personnel spending at least 80% of their time working CIP efforts). More specific guidelines for reporting CIP manpower costs will be developed for future budget calls based on lessons learned this year.
e. Defense Working Capital Fund (DWCF) resources should be reported only by the DWCF manager -- the service provider. DoD Components (the billpayer) should not include funding in their CIP Exhibit 1 that represents payments to a DWCF.
Attachment 1
CRITICAL INFRASTRUCTURE PROTECTION
[COMPONENT TITLE]
[DEFENSE INFRASTRUCTURE SECTOR TITLE]
TOA $ in Thousands
|
Appn/Program/BA/BSA |
FY1996 |
FY1997 |
FY1998 |
FY1999 |
FY2000 |
FY2001 |
FY2002 |
FY2003 |
FY2004 |
FY2005 |
A SEPARATE FORMAT IS REQUIRED FOR EACH APPLICABLE DEFENSE INFRASTRUCTURE SECTOR (Sector): Defense Information Infrastructure, C3, Financial Services, Space, Logistics, Transportation, Public Works, Health Affairs, Personnel, Emergency Preparedness, and ISR.
FOR EACH DEFENSE INFRASTRUCTURE SECTOR, REPORT BY APPROPRIATION AS FOLLOWS:
- Military Personnel - report by Sector program level only.
- O&M/DHP - report at each applicable Sector program by budget activity
- Procurement - report at each applicable Sector program by budget activity/P1 line item.
- RDT&E - report at each applicable Sector program by budget activity/program element
- Military Construction - report at each applicable Sector program by location/project title
- Defense Working Capital Fund - report at each applicable Sector program at the Working Capital Activity level
Military Personnel
Program A
Program B
Total, MilPay
Operation and Maintenance
Program A
BA1, Opr Forces
BA2, Train & Recruit
Subtotal
Program B
BA1, Opr Forces
BA2, Train & Recruit
Subtotal
Total, O&M
CIP Exhibit 1
Attachment 1
|
Appn/Program/BA/BSA |
FY1996 |
FY1997 |
FY1998 |
FY1999 |
FY2000 |
FY2001 |
FY2002 |
FY2003 |
FY2004 |
FY2005 |
Procurement
Program A
BA1/P1 Title
BA1/P1 Title
Subtotal
Program C
BA2/P1 Title
BA4/P1 Title
Subtotal
Total, Procurement
RDT&E
Program D
BA1/PE Title
BA3/PE Title
Subtotal
Program E
BA1/PE Title
BA 1/PE Title
Subtotal
Total, RDT&E
etc.
SUMMARY BY PROGRAM (all appropriations):
Program A
Program B
Program C
TOTAL
Attachment 1
TAB A: CRITICAL INFRASTRUCTURE PROTECTION
PROGRAM CATEGORIES
Infrastructure Analysis and Assessment:
A set of related processes, which include the following activities:- Defense Infrastructure Sector Characterization
- Military Plans And Operations Infrastructure Dependency Characterization
- Critical Asset Identification
- Characterization Of Critical Asset Dependencies On Defense And Commercial Infrastructures
- Potential Military Operational Impacts Assessments
- Critical Asset/Defense Infrastructure Vulnerability Assessments
- Sector Interdependency Analysis
Budget exhibits should include database design and development, tools and models development, asset and site surveys, data/information collection, and analysis and assessment.
Remediation: Owner/operator precautionary measures taken to improve known deficiencies and weaknesses in defense infrastructure sectors or critical assets. Examples include education and awareness, operational process or procedural changes, system configuration changes (e.g., physical diversity, redundancy, deception), system component changes (e.g., hardware, software, and links).
Budget exhibits should include only projected remediation activities that will directly result from the infrastructure analysis and assessment activities.
Indications and Warning: Indications are adversary actions or infrastructure conditions that signify an event is likely, planned, or underway. Defense infrastructure sectors will define, monitor, and report infrastructure conditions. The NIPC will provide national warning for significant infrastructure attacks. The Intelligence Community will provide long range indications and warning.
Budget exhibits should include Sector/Component activities, processes, and equipment required to define, monitor and report infrastructure conditions, NIPC support, DoD IC activities, processes, and equipment to provide long range CIP indications and warning, and DoD IC support to DoD Sector/Components in infrastructure monitoring and reporting
Mitigation: Operator actions resulting from an infrastructure warning or incident to (1) minimize or alleviate the impact to military operation(s) or infrastructure service(s), (2) facilitate incident response, and/or (3) quickly restore services. Examples include information safeguards, graceful service degradation, load shedding, network partitioning, increased monitoring, heightened security measures, emergency and backup services, and relocation.
Budget exhibits should include planning, training, exercises, and equipment.
Response: Dedicated third party (not defense infrastructure operator) activities undertaken to eliminate the cause or source of an event. Examples include computer network defense and emergency response, law enforcement, investigation, medical, fire, and rescue.
Reconstitution: Actions required rebuilding or restoring an infrastructure after it has been damaged or compromised.
All phases: Budget exhibits should include: Sector CIAO and staff support, Sector participation in the CIP Integration Activity and the interagency National Defense Coordination Subgroup, DoD Component staff support and cooperation with Sector CIAOs and Special Function Coordinators.
|
Assurance |
In the context of CAAP, assurance is a process of identifying assets deemed critical to the Department of Defense in peacetime, crisis and war; assessing the potential threats to these assets and the capabilities they provide; quantifying the likely non-availability to the Department of Defense under various hazard scenarios; identifying potential actions that can be taken to restore those assets (or functionality they provide) if they are lost, damaged, corrupted, or compromised; and identifying and recommending options to protect, mitigate, and improve the availability of these Critical Assets to the DoD organizations that own, use, and control them. It includes a range of activities to systematically inform planners and decision makers of the probability of availability and quality (e.g., integrity, reliability, confidentiality, survivability, endurability, capacity, adequacy) of specific assets or services under given scenarios; quantifying the likely impact of non-availability to the military operation or defense activity; and identifying and prioritizing options to improve the likelihood of the availability of specific assets or services in specific scenarios. Examples of assurance activities that can improve the likelihood of asset availability include protection (preventing, by whatever means, the disruption or corruption of an asset); mitigation or moderation of the effects of disruption or corruption (by controlling the damage, providing alternative services, and reducing demand on the asset); and planning for and providing timely restoral or recovery. Alternatively, plans can be made to absorb the loss of otherwise anticipated services. Assurance of a Critical Asset is the responsibility of the owning or controlling DoD Component. (DoDD 5160.4) |
|
Computer Emergency Response Team (CERT) |
An organization chartered by an information system owner to coordinate and/or accomplish necessary actions in response to computer emergency incidents that threaten the availability or integrity of its information systems. (DODD 5160.54) |
|
Critical Asset |
Any facility, equipment, service or resource considered essential to DoD operations in peace, crisis and war and warranting measures and precautions to ensure its continued efficient operation, protection from disruption, degradation or destruction, and timely restoration. Critical Assets may be DoD assets or other government or private assets, (e.g., Industrial or Infrastructure Critical Assets), domestic or foreign, whose disruption or loss would render DoD Critical Assets ineffective or otherwise seriously disrupt DoD operations. Critical Assets include both traditional "physical" facilities and equipment, non-physical assets (such as software systems) or "assets" that are distributed in nature (such as command and control networks, wide area networks or similar computer-based networks). (DoDD 5160.54) |
|
Criticality Index, Criticality Metric |
Measurement established within an asset class, organization or sector, to assist in ranking assets for assurance or protection activities. An example would be a graduated indicator of impact from system-wide slight degradation of service to cessation of operations. (CAAP Working Definition) |
|
Criticality-Vulnerability Ratio |
Comparison of criticality and vulnerability indices. (CAAP Working Definition) |
|
Defense Infrastructure |
Infrastructure owned, operated or provided by the Department of Defense. Defense Infrastructure Sectors include the DII, C3, Space, ISR, Financial Services, Logistics, Public Works (includes DoD-owned or -operated utilities, roads, rails and railheads and their interface to commercial and other Government systems), Personnel, Health Affairs and Emergency Preparedness. (Modified from DoDD 5160.54) See also definitions of Infrastructure, National Infrastructure, National Defense Infrastructure, and International Defense Infrastructure. |
|
DoD Installation
Force Protection |
A facility subject to the custody, jurisdiction, or administration of any DoD Component. This term includes, but is not limited to, military reservations, installations, bases, posts, camps, stations, arsenals, or laboratories where a DoD Component has operational responsibility for facility security and defense. Examples are facilities where the military commander or other specified DoD official under provisions of DoD Directive 5200.8 has issued orders or regulations for protection and security. Both industrial assets and infrastructure assets, not owned by the Department of Defense, may exist within the boundaries of a military installation (DoDD 5160.54) Security program developed to protect Service members, civilian employees, family members, facilities and equipment, in all locations and situations, accomplished through planned and integrated application of combating terrorism, physical security, operations security, personal protective services supported by intelligence, counterintelligence, and other security programs. (Draft DoDD 2000.12) |
|
Industrial Asset |
Any factory, plant, building or structure used for manufacturing, producing, processing, repairing, assembling, storing, or distributing a product or components that supports a DoD Component. A Critical Industrial Asset is an industrial asset deemed essential to DoD operations or the functioning of a Critical Asset. (DoDD 5160.54) |
|
Information Assurance |
Information Operations that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. This includes providing for restoration of information systems by incorporating protection, detection, and reaction capabilities. (DoDD S-3600.1) |
|
Information System |
The entire infrastructure, organization, personnel and components that collect, process, store, transmit, display, disseminate and act on information under DoDD S-3600.1. |
|
Infrastructure |
The framework of interdependent networks and systems comprising identifiable industries, institutions, and distribution capabilities that provide a continual flow of goods and services essential to the defense and economic security of the United States, the smooth functioning of government at all levels, or society as a whole. (DoDD 5160.54) |
|
Infrastructure Analysis and Assessment |
Coordinated identification of DoD, National Defense Infrastructure, and International Defense Infrastructure critical assets, their system and infrastructure configuration and characteristics, and the interrelationships among infrastructure sectors; assessment of their vulnerabilities; quantification of the relationship between military plans and operations and critical assets / infrastructures; and assessment of the operational impact of loss or compromise. (CIP Working Definition) |
|
Infrastructure Asset |
Any infrastructure facility, equipment, service or resource that supports a DoD Component. A Critical Infrastructure Asset is an infrastructure asset deemed essential to DoD operations or the functioning of a Critical Asset. (DoDD 5160.54) |
|
Infrastructure Indications and Warning |
Tactical indications through the implementation of sector monitoring and reporting, strategic indications through Intelligence Community support, and warning in coordination with the National Infrastructure Protection Center (NIPC) in concert with existing DoD and national capabilities. (CIP Working Definition) |
|
Interdependence |
Dependence among elements or sites of different infrastructures, and therefore, effects by one infrastructure upon another. (Modified from IAP Working Definition) |
|
International Defense Infrastructure |
Those elements of international infrastructure that are critical to Department of Defense operations. (CIP Working Definition) |
|
Mitigation |
Preplanned and coordinated operator reactions to infrastructure warning and/or incidents designed to reduce or minimize impacts; support and complement emergency, investigatory, and crisis management response; and facilitate reconstitution. (CIP Working Definition |
|
National Defense Infrastructure |
Those assets in the other government and national infrastructure sectors and industrial assets that are critical to National Defense. (CIP Working Definition) |
|
National Infrastructure |
Those infrastructures essential to the functioning of the nation and whose incapacity or destruction would have a debilitating regional or national impact. National infrastructures include telecommunications, electrical power systems, gas and oil transportation and storage, water supply systems, banking and finance, transportation, emergency services, and continuity of government operations. (DoDD 5160.54) |
|
Reconstitution |
Owner/operator directed restoration of critical assets and/or infrastructure. |
|
Remediation |
Deliberate precautionary measures undertaken to improve the reliability, availability, survivability, etc. of critical assets and/or infrastructures, e.g., emergency planning for load shedding, graceful degradation and priority restoration; increased awareness, training and education; changes in business practices or operating procedures, asset hardening or design improvements, and system level changes such as physical diversity, deception, redundancy and backups. (CIP Working Definition). |
|
Response |
Coordinated third party (not owner/operator) emergency (e.g., medical, fire, hazardous or explosive material handling), law enforcement, investigation, defense, or other crisis management service aimed at the source or cause of the incident.(CIP Working Definition) |
|
Technical Attack |
An attack that can be perpetrated by circumventing or nullifying hardware or software protection mechanisms, or exploiting hardware or software vulnerabilities, rather than physical destruction or by subverting system personnel or other users. (DoDD 5160.54) |
|
Vulnerability Index, Vulnerability Metric |
Measurement or indicator based upon various conditions such as threat, environment, geographic area, readiness, etc. (CAAP Working Definition) |
(page is intentionally blank)
Appendix B: National and Defense Critical Infrastructure Definitions
The President’s Commission on Critical Infrastructure Protection (PCCIP) defined critical infrastructures as an infrastructure that is so vital that its incapacitation or destruction would have a debilitating impact on defense or economic and the national critical infrastructures.
- Banking and Finance: A critical infrastructure characterized by entities; such as retail and commercial organizations, investment institutions, exchange boards, trading houses, and reserve systems, and associated operational organizations, government operations, and support activities; involved in all types of monetary transactions, including their storage for saving purposes, their investment for income purposes, their exchange for payment purposes, and its disbursement in the form of loans and other financial instruments.
- Electrical Power Systems: A critical infrastructure characterized by generation stations, and transmission and distribution networks that create and supply electricity to end users so that end users achieve and maintain nominal functionality. It includes the transportation and storage of fuel essential to that system.
- Emergency Preparedness: A critical infrastructure characterized by medical, police, fire, and rescue systems and personnel that are called upon when an individual or community responds to emergencies. These services are typically provided at the local level (county or metropolitan area). In addition, state and Federal response plans define emergency support functions to assist in response and recovery.
- Gas and Oil Production, Storage, and Transportation: A critical infrastructure characterized by the production and holding facilities for natural gas, crude and refined petroleum, and petroleum-derived fuels; the refining and processing facilities for these fuels; and the pipelines, ships, trucks, and rail systems that transport these commodities from their sources to systems that depend on gas and oil in one of their useful forms.
- Government Services: Sufficient capabilities at the federal, state, and local levels of government required to meet the needs for essential services to the public.
- Information and Communications: A critical infrastructure characterized by computing and telecommunications equipment, software, processes, and people that support the following:
- Processing, storage, and transmission of data and information
- Processes and people that convert data into information and information into knowledge
- Data and information
- Transportation: A critical infrastructure characterized by the physical distribution system critical to supporting the national security and economic well-being of this nation, including the national airspace system, airlines, aircraft, and airports; roads and highways, trucking and personal vehicles; ports and waterways, and the vessels operating on them; mass transit, both rail and bus; pipelines, including natural gas, petroleum, and other hazardous materials; freight and long haul passenger rail; and delivery services.
- Water Supply Systems: A critical infrastructure characterized by the sources of water; reservoirs and holding facilities; aqueducts and other transport systems; the filtration, cleaning, and treatment systems; and the pipelines, cooling systems, and other delivery mechanisms that provide for domestic and industrial applications, including systems for dealing with water runoff, waste water, and fire fighting.
The DoD Defense Infrastructure Sectors and lead for each sector are listed as follows:
- Financial Services: Financial institution services fall into two categories. The first category consists of servicing official DoD (i.e., appropriated fund) disbursing and paying operations and providing cash and accepting deposits for credit to officially designated Treasury General Accounts. The second includes servicing individuals and on-base organizations (i.e. non-appropriated funds) with normal deposit, maintenance of accounts, safekeeping, and other financial services functions. The Defense Finance and Accounting Service (DFAS) supports official DoD activities and provides military and civilian pay, travel pay, transportation pay, vendor pay, contractor pay, dispersing, payment of foreign military sales, and general and defense business operations fund accounting. DFAS is responsible for coordinating the assurance activities of this defense infrastructure sector
- Transportation: The Defense Transportation System (DTS) includes resources (surface, sea and lift assets; supporting infrastructure; personnel; and related systems) and interrelationships of DoD, federal, commercial, state/local agencies, and non-US activities that support DoD global transportation needs. The US Transportation Command (USTRANSCOM) is the single manager for DoD transportation and is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Public Works: Public works includes four distinct physical infrastructure sectors: electric power, oil and natural gas, water and sewer; and emergency services (fire, medical, hazardous material handling, etc). This defense infrastructure sector is composed of networks and systems, principally for the distribution of the associated commodities. The generation, production, and transport of these commodities for and to DoD are primarily the function of their respective national infrastructures. The US Army Corp of Engineers is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Space: The Space defense infrastructure sector is composed of both space- and ground- based assets including launch, specialized logistics, and control systems. Facilities are located worldwide on both DoD-controlled and private sites. The US Space Command (USSPACECOM) is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Logistics : The Logistics defense infrastructure sector includes all activities, facilities, networks, and systems that support the provision of supplies and services to US forces worldwide. The logistics defense infrastructure includes material acquisition and development; the storage, movement (strategic movement is the responsibility of the Transportation defense infrastructure and USTRANSCOM), and distribution of supplies; maintenance of material and supplies; and the final disposition of material no longer needed by DoD. The Defense Logistics Agency is responsible for managing most consumable supplies, administering contracts, and acquiring materials and services, and for coordinating the assurance activities of this defense infrastructure sector.
- Emergency Preparedness : DoD provides direct support to the domestic sector under a number of programs. These programs depend on DoD’s ability to marshal and coordinate many assets, facilities, networks and systems DoD-wide. DoD supports, through selected operations, civil authorities in times of domestic emergencies, civil disturbances, civil law enforcement actions, and natural disasters. DoD also supports domestic response to weapons of mass destruction (WMD) situations, and when required, special events of national significance. The Director of Military Support (DOMS) is the Executive Agent for management of DoD’s capability to provide military support to the civilian sector, through coordination and direction of DoD assets. Additionally, the DOMS is the action agent for the Office of the Secretary of Defense (OSD) Continuity of Operations Plan (COOP) as well as other special related responsibilities. The DOMS is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Health Affairs : DoD maintains an extensive health care infrastructure across its facilities worldwide. In addition, DoD manages a larger system of non-DoD care facilities within its health care network. The health care infrastructure consists of facilities and sites located at DoD installations, information systems linking those facilities, and networks of health care among the services and components. The office of Assistant Secretary of Defense for Health Affairs is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Personnel : The Personnel defense infrastructure sector includes a large number of assets hosted on Component sites; a network of facilities within and among service components; and computational and information systems linking those sites and facilities. The personnel infrastructure is not only responsible for its own assets, but also coordinates commercial services and facilities that support the personnel function including, but not limited to, recruitment, record keeping, and general training requirements. The Defense Human Resources Agency is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Defense Information Infrastructure : The DII is the web of communications networks, computers, software, databases, applications, weapon system interfaces, data, security services, and other services that meet the information processing and transport needs of DoD users across the range of military operations. It encompasses: (1) sustaining bases, tactical, DoD-wide information systems, and Command, Control, Communications, Computers, and Intelligence (C4I) interfaces to weapons systems, (2) the physical facilities used to collect, distribute, store, process, and display voice, data, and imagery; (3) the applications and data engineering tools, methods, and processes to build and maintain the software that allow Command and Control (C2), Intelligence, Surveillance, and Reconnaissance (ISR), and Mission Support users to access and manipulate, organize, and digest proliferating quantities of information; (4) the standards and protocols that facilitate interconnection and interoperation among networks; and (5) the people and assets which provide the integrating design, management and operation of the DII, develop the applications and services, construct the facilities, and train others in DII capabilities and use. (DII Master Plan Version 7.0, page 2.1). DISA is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Command, Control, and Communications (C3): This defense infrastructure sector is composed of a number of assets, facilities, networks, systems and business processes and practices that support the command, control, and communications functions necessary for Defense operations. DISA is responsible for coordinating the assurance activities of this defense infrastructure sector.
- Intelligence, Surveillance, and Reconnaissance (ISR): This defense infrastructure sector is composed of those assets, facilities, networks and systems that support the development, production and conduct of ISR activities, such as intelligence production centers and fusion centers. DIA is responsible for coordinating the assurance activities of this infrastructure sector.
Note that the national infrastructures presented in Figure 3-1 National Critical Infrastructure Protection Organization combine the two energy infrastructures and separate three emergency service infrastructures (i.e. government services, fire, and emergency health services) to show Lead Agency responsibilities.
(page is intentionally blank)
Appendix C: DoD CIP Integration Activity (CIPIA)
The Director, Critical Infrastructure Protection provides policy guidance and oversight for the functional requirements of CIP. However, in order to implement and further develop the DoD CIP plan and program, CIP activities must be coordinated and integrated. This requires the full-time liaison of domain experts for the defense infrastructures; military operations and planning; infrastructure analysis and information assurance. These activities, coordinated and integrated by the Director, Critical Infrastructure Protection, are necessary to:
- Integrate the infrastructure assurance related activities of the Defense Infrastructure Sector Lead Components, the CIP Special Function Components, the Critical Asset Assurance Program (CAAP), the Defense-wide Information Assurance Program (DIAP), the JPO-STC managed Infrastructure Assurance Program (IAP), the military deliberate and crisis planning process, and other DoD programs as appropriate
- Integrate the Defense Sector Assurance Plans into a comprehensive DoD Infrastructure Assurance Plan
- Coordinate with and, where appropriate, provide direct support to the JTF-CND or affected Component(s) responsible for the conduct of defensive operations in response to significant attacks on Defense Infrastructure
- Support the Sector CIAOs, the Components, the JTF-CND, and the Defense Intelligence Community in the integration and implementation of defense infrastructure monitoring and reporting
- Map Defense Infrastructure to the National, National Defense, and International Defense Infrastructures
- Perform interdependency analyses
- Prepare and coordinate DoD responses to the Critical Infrastructure Coordination Group, its sub-groups, or other interagency entities on behalf of the CIP Functional Coordinator and to the NIPC for other than operations affecting the JTF-CND
- Coordinate the activities of the DoD Lead Components with the national Lead Agencies and other interagency working groups
- Prepare and coordinate DoD input to the National Infrastructure Assurance Plan, interface with the National Plan Coordination Office, and function as the primary DoD interface to the national Information Sharing and Analysis Center
- Support the development and administration of the Critical Asset Assurance Program
- Coordinate with and leverage other related DoD programs, e.g., Force Protection
- Coordinate and integrate infrastructure protection and information assurance
Organization
The CIPIA will be co-located with the DIAP office and will include:
- Full-time Liaison from the Defense Infrastructure Sectors
- Full-time Joint Staff/Services Planning Liaison (Deliberate/Crisis Action Planning integration)
- Full-time Infrastructure Assurance Program Liaison and Analysis Cell (JPO-STC)
- As required liaison from Special Functions and related programs, e.g., industrial security (Defense Security Service) and Force Protection (Defense Threat Reduction Agency)
- Full-time contract administrative and technical support
Defense Infrastructure Liaison
Responsibilities of liaison representatives from the Defense Infrastructure Sector Coordination Lead Components --DFAS, DLA, DISA, DIA, USACE, USTRANSCOM, USSPACECOM, HA, DHRA, and DOMS -- include but are not limited to:
- Representing the Defense Infrastructure Sectors in CIPIA activities
- Coordinating with corresponding Lead Agencies for National Infrastructures
- Integrating Sector Assurance Plans and Programs into the DoD CIPP
- Assisting Joint Staff in incorporating Defense Infrastructure into Deliberate and Crisis Planning process
- Supporting the incorporation of Defense Infrastructure into CAAP decision support tools and processes
- Coordinating operational monitoring and reporting requirements
CIPIA Functional Area Responsibilities
- Executive Decision Support
- Defensive Operations direct support
- Defense Infrastructure Characterization and Integration
- Military Planning and Operations Integration
- CAAP Support and Execution
- Supporting Services Coordination
A summary of the sub-tasks under each functional area is provided in Table C-1.
|
Table C-1 Summary of CIPIA Functional Area Sub-Tasks |
|
|
Functional Area |
Sub-Tasks |
|
DoD Critical Infrastructure Protection Plan (CIPP) |
|
|
National Liaison |
Lead and Special Component activities with interagency counterparts must be coordinated to insure consistency of interaction with the interagency community and the identification of DoD requirements for inclusion in the NIAP.
This will require the expertise of and a coordinated effort from the representatives of the Defense Lead and Special Function Components
|
|
International Liaison |
|
|
Executive Decision Support |
|
|
Defensive Operations direct support |
|
|
Defense Infrastructure Characteri- zation and Integration |
Provide the mechanism for coordinating Sector activities, information sharing and configuration management and control in defining, designing, and completing sector characterization. Each Sector is responsible for developing and implementing a Sector Assurance Plan and Program. However, while each Sector must address the unique attributes and circumstances of its sector, each sector plan must be developed to integrate into the DoD plan.
Provide a single point within the DoD to reconcile and integrate infrastructure analysis and assessment requirements from CINCs/Joint Staff, OSD, Services, Defense Agencies, related Defense programs (e.g., CAAP, DIAP, and Force Protection). In addition, incorporate any unique requirements resulting from DoD’s role as the Special Function Agency for National Defense. DoD is supported by Defense, National Defense, and International Defense Infrastructure and has a role in the protection of National Infrastructure. The information necessary to support infrastructure protection analysis is both geographic (e.g., location and topology of the node and links that make up the physical infrastructure) and operational (e.g., operating parameters, defense missions supported, etc.). Collecting and maintaining this information in a media and format that will be useful to DoD decision-makers is a critical function. Specifically:
The relationships between commercial infrastructures and defense operations must be identified to determine the components necessary to maintain an acceptable level of service for network performance, and the components necessary to maintain an acceptable level of service for defense operations. Standard analytic methods must be developed and implemented. To achieve this objective, the CIP Integration Activity will be responsible for the following:
Information Management Services The requirements for the DoD Critical Infrastructure Information Management System must be developed. A comprehensive information management system should include:
|
|
Military Planning and Operations Integration |
The CIPIA will also be responsible for coordinating and supporting standards for the decentralized conduct of assessments, including:
This activity will be responsible for the vertical implementation of assessment results that identify remediation and mitigation actions. The assessment results will be passed to the DoD entity with cognizance over the impacted site. The Integration Activity will coordinate support for implementation from CINCs/Joint Staff, OSD, Services, and Defense Agencies, related DoD Programs (e.g., CAAP and DIAP). |
|
CAAP Support and Execution |
|
|
Supporting Services Coordination |
|
Life Cycle Activities
The following chart details CIPIA activities across the CIP life cycle.
|
Table C-2 Detailed CIP integration Activities Across the CIP Life Cycle |
|
|
Life Cycle Phase |
Action |
|
Analysis and Assessment |
|
|
Remediation |
|
|
Indications & Warning |
|
|
Mitigation |
|
|
Incident Response |
|
|
Reconstitution |
|
|
Phase Independent |
|
|
|
|
|
|
|
|
|
|
|
|
CIP Integration Activities Reserved to the ODASD(S&IO)CIP |
|
Liaison with the CIAO Office |
|
Executive Secretariat to the CIAO Council |
|
Chair and Executive Secretariat to the National Defense Coordination Sub-Group |
Appendix D: DoD Critical Asset Assurance Program (CAAP)
The Critical Asset Assurance Program (CAAP) was established in January1998 by DoD Directive 5160.54 to implement the requirements of Executive Order 12656, Assignment of Emergency Preparedness Responsibilities, and to improve DoD's mission readiness by accounting for dependencies on assets and infrastructure in the Deliberate and Crisis action planning process.
The Critical Infrastructure Protection Integration Activity (CIPIA) under the direction and oversight of the Director, Critical Infrastructure Protection will support the development and administration of the CAAP. CAAP is a set of processes, tools, and information intended to assist DoD Critical Asset Owners, DoD Installations, DoD Components, Sector CIAOs, and the DoD Special Function Coordinators in their execution of the following:
- Identification of critical assets . The program will support the identification of critical assets by standardizing identification requirements and processes.
- Monitoring and reporting of the status of critical assets . The program will support monitoring and reporting by standardizing terminology and identifying the set of assets to be monitored, associating monitoring and reporting criteria with each asset or class of assets, and providing an environment for the exchange of information.
- Improved asset assurance . The program will support improved asset assurance by standardizing criticality and vulnerability metrics; enabling remediation based on criticality and vulnerability ratios; enabling mitigation activities based on warning and alert conditions; and enabling assurance and protection activity status tracking.
- Improved risk analysis and management . The program will support risk analysis and management by providing an integrated decision framework and an automated critical asset information system.
A key concept of the Critical Asset Assurance Program is asset criticality as a function of time and situation. In order to conduct risk tradeoff analyses and leverage protection and assurance resources, decision makers will need standardized, timely information about the operational or business value of assets, e.g., what military operations or services depend on a given asset and how dependencies change across time; how sensitive the operation or service is to the loss or compromise of the asset (the maximum allowable down time); the assurance profile of the asset (whether asset restoration or a switch to a designated backup can occur within the allowable down time). The term criticality attributes refers to those elements of information required to determine an asset’s criticality. Some "baseline" elements of information will be fairly static or independent of time and situation and can be routinely identified and collected; however other elements of information essential for analysis and decision making will be identified by time and situation and collected accordingly. As the program, the user requirements, and the information mature, criticality attributes may be aggregated into a criticality index such as a numeric scale for ease of reference, display and comparison. Similarly, vulnerability attributes, baseline and situational elements of information about asset vulnerability, may be aggregated into a vulnerability index. A criticality-vulnerability ratio is a comparison of the criticality and vulnerability indices.
Appendix E: Infrastructure Assurance Program (IAP)
The Infrastructure Assurance Program is a research and engineering program established in 1995 and sponsored by the Office of the Secretary of Defense (OSD) and the Joint Staff. The US Navy is the Executive Service. The program is administered by the Joint Program Office for Special Technology Countermeasures (JPO-STC) and will contribute the following to the DoD Critical Infrastructure Protection effort:
- Engineering methods, metrics and tools for all activities in the CIP analysis and assurance life cycle phase (critical asset identification, defense infrastructure characterization, operational impact analysis, vulnerability assessment, and interdependency analysis) customized for all levels (asset, installation, defense infrastructure sector, military operation, and defense-wide)
- Centralized DoD expertise in and responsibility for infrastructure interdependency analysis
- Centralized DoD expertise in and responsibility for mapping DoD critical assets and Defense Infrastructure to National and International Defense Infrastructure
- Infrastructure information security research and standards
- Analytic and integration support to Military Plans and Ops and Intelligence Support
- Information engineering
The IAP represents the majority of DoD’s investment to date, both in time and resources, to address DoD dependencies on critical commercial infrastructures. This effort has resulted in an established and proven process tailored to DoD mission needs with important insight regarding other approaches. The process proposed for DoD’s Critical Infrastructure Protection will build on the system developed to support the JPO-STC’s Infrastructure Assurance Program, and extend it to address DoD infrastructures. The following describes the process:
The process begins with the identification of a site. The term site, as used here, is defined as a geographic location that supports a DoD mission (as a provider of capabilities or a receiver of services) and is a DoD receiving point for National Defense Infrastructure (NDI) or International Defense Infrastructure (INDI) infrastructure commodities.
Figure E-1. Identification of Sites
Sites will include military facilities as well as supporting facilities from the defense infrastructure sectors. Examples of sites from the defense infrastructure are shown in Table E-1.
Table E-1. Examples of Sites
|
Defense Infrastructure Sector |
Example |
|
Defense Information Infrastructure Command, Control and Communications (C3) |
Megacenters Command Center (e.g., NMCC) |
|
Financial Services |
DFAS Facilities Operational Locations |
|
Space |
Terrestrial Downlink Locations Data Processing Locations |
|
Logistics |
Fuel Depots Inventory Control Points |
|
Transportation |
Rail Heads |
|
Public Works |
Water Treatment Facilities Fire Stations |
|
Health Affairs |
Military Hospitals |
|
Personnel |
Personnel Centers |
The most expedient means of identifying the various sites is through the Registered Asset List (RAL) developed to support the CAAP. The RAL is a geographic information system (i.e., a relational database with a map interface) containing most of the physical sites upon which the DoD Components depend to carry out their mission. In developing the RAL, the emphasis has been on the objective question "What physical sites do you depend on?" rather than the much more subjective inquiry into what supporting sites are critical to the operation of a given site. The latter inquiry was the central tenet of the old Key Asset Protection Program (KAPP) and proved to be a non-useful line of questioning when moved outside the context of physical protection.
The RAL contains a large volume of data that identifies the location, mission and function of thousands of sites throughout the world. To assist in the identification and assessment process, the sites are logically grouped into Defense Infrastructure Sectors that provide services and support to the military. This permits the DoD to determine the business connectivity among the Defense Infrastructure Sectors in a way never before possible within the DoD.
Characterize the National Defense or International Defense Infrastructure Supporting the Site
An analysis of the supporting NDI or INDI is performed for each site. The characterization of the NDI/INDI begins with taking the raw data for a given infrastructure system (e.g., electric power, telecommunications, transportation) and converting it into a usable format. This information is then translated into a geographic information system (GIS) for use in conducting analyses. A suite of analytic tools assists the analyst in determining which system components are critical to a geographic site or area of interest to the DoD. The characterization is completed without a specific scenario defined. This "threat-independent" approach requires the analysts to approach the question of criticality in an unbiased manner so as to uncover both direct and indirect impacts. The end result of the infrastructure characterization, as depicted in Figure E-2, is an array of products that depict the infrastructures in and around the site of interest.
Figure E-2. Infrastructure Characterization
Identify major functions at the site
To address the uniqueness of each site, and to prepare for the analysis and assessment of the supporting defense infrastructure sectors requires the identification of the major functions that take place within the confines of the site. The functions will include, as a minimum, Major Commands, CINC Support Activities, Tenant Facilities, and Service Support Activities.
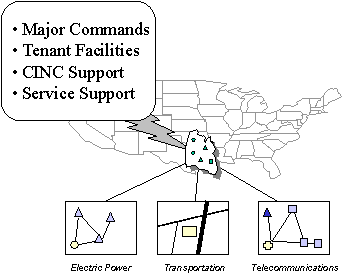
Figure E-3. Major Functions at the Site
Subdividing the major functions at the site permits the analysts to capture the wide diversity of activities that can take place at a given location. Following the identification of these major functions, the NDI/INDI characterization at the site will be reevaluated to determine if additional dependencies exist specific to the major functions.
Identify Defense Infrastructure Dependencies for the Site’s Primary Functions
The next step in the process maps the primary functions to the Defense Infrastructure components supporting the functions at the site of interest. The result of this mapping is a dependency matrix indicating the Defense Infrastructure Sector sites necessary to support the wide range of missions for each site. In effect, the dependency matrix represents static information that objectively identifies a dependency of the military site.
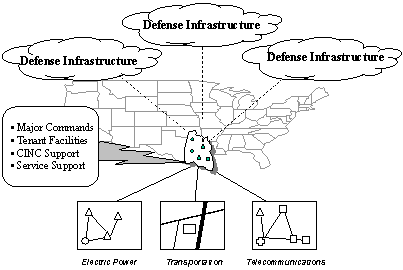
Figure E-4. Defense Infrastructure Dependencies
The process to build the dependency matrix is relatively straightforward, but the information necessary to compile an accurate picture of the dependency is often difficult to acquire. The process can be seen by the table below. To build the matrix, one simply fills in the right column with the name of a Defense Infrastructure site.
|
Defense Infrastructure |
Site of Interest Function X is supported by: |
|
Defense Information Infrastructure |
|
|
C3 |
|
|
Financial Services |
|
|
Space |
|
|
Logistics |
|
|
Transportation |
|
|
Public Works |
|
|
Health Affairs |
|
|
Personnel |
|
|
Emergency Preparedness |
|
|
ISR |
Characterize Interdependencies among the Defense Infrastructures Sectors Supporting the Site
The previous step represents a pair-wise mapping of supporting Defense Infrastructure Sector sites to a primary function. An equally important aspect of protecting critical infrastructure is identifying the interdependencies among the Defense Infrastructure Sectors. In effect, the interdependencies are highlighting how one business component of DoD depends on the other business components. By characterizing the interdependencies among its Defense Infrastructure Sector components, the DoD can establish a first order representation of its "business connectivity." An important outgrowth of this process will be the further classification of Defense Infrastructure sites as Supporting Sites and/or Supported Sites.
Figure E-5. Interdependencies among the Defense Infrastructure Sectors
Characterize the NDI/INDI Supporting the Defense Infrastructure Sites
For each Defense Infrastructure Sector site supporting the site of interest, a complete analysis of the supporting infrastructure can be performed (see Figure E-5). This characterization will be identical in scope to that performed for the site of interest, but will provide new insight into the potential effect losing a remote infrastructure component can have on a military base or other important facility.
Figure E-6. Characterizing Infrastructure Dependencies at the Defense Infrastructure Sector Sites
Characterize National Defense Infrastructure Interdependencies Supporting the Site
The final step is one of shared responsibility between the DoD and the National Infrastructure Assurance Program. PDD 63 calls upon the National Coordinator to develop a capability to evaluate the interdependencies within the national infrastructures. This is generally accepted to reflect the need to look at infrastructures on a regional and nation-wide basis. DoD will continue to analyze and assess the effect of local interdependencies to get a complete picture.
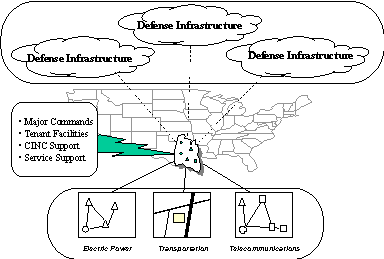
Figure E-7. Interdependencies within the National Defense Infrastructure
Assessing Operational and Business Impacts
The analytic process described above produces detailed information regarding the criticality of defense assets, information which can be summarized in numeric criticality ratings and associated with the assets in the Registered Asset List. Criticality ratings will be used to prioritize and schedule asset vulnerability assessments which incorporate, among other things, threat information; sector monitoring input; and asset emergency planning and readiness profiles. This will result in recommended remediation and mitigation options. The Critical Asset Assurance Program (CAAP) automated information system will track the status of remediation and mitigation projects.
(page is intentionally blank)
Appendix F: The Defense-wide Information Assurance Program (DIAP)
The capability of DoD to carry out its integrated mission is highly dependent upon the interconnected set of information systems and networks called the Defense Information Infrastructure (DII). In today's environment of sophisticated weaponry and rapid, global force protection, the ability to provide accurate information when needed is vital to all aspects of DoD’s operations (warfighting and peacekeeping). Today’s dynamic information age provides DoD an unprecedented capability to conduct day-to-day business and to perform contingency or emergency operations using open, interconnected, largely public, information systems. This ability to acquire, process and move vast amounts of important DoD information virtually around the world in mere seconds has created new capabilities, dependencies, and vulnerabilities. DoD’s reliance on broadly networked information systems results in a DII shared risk environment. Shared risk refers to risk that, when accepted by a single DoD activity, subjects all users of interconnected systems and networks to the same risk. Added to this already complex environment is DoD’s growing dependence on supporting commercial infrastructures (e.g., power, telecommunications, petroleum, oil, and lubricants).
These increased capabilities, dependencies, and vulnerabilities have led to the emergence of the concept and practice of IA. Information assurance requires an approach that goes beyond the "classic" protection of DoD’s information based principally on national security classification. The approach must consider how critical the information is to mission accomplishment and provide the means, commensurate with that criticality, to ensure that information is authentic, uncorrupted in transmission and available when needed and to ensure the availability of supporting critical infrastructures. In addition, IA relies on a number of interrelated and interdependent security disciplines -- communications security (COMSEC), computer security (COMPUSEC), information security, information systems security (INFOSEC), emanation security, physical security, personnel security, operations security (OPSEC), and industrial security -- as well as training, the application of uniform engineering and installation standards, and a recognition of the importance of the supporting critical infrastructures. Standardized implementation of these disciplines and standards is a critical component of IA. IA is also an evolutionary and dynamic discipline that requires flexibility, adaptability and responsiveness to new technologies, and changing threats and vulnerabilities.
The Department will provide Information Assurance (IA) through a Defense-wide Information Assurance Program (DIAP) and an associated set of management processes and structure that will:
- Integrate, and provide effective program oversight of DoD’s Information Assurance (IA) activities
- Provide the structure that will enable DoD to monitor and manage the readiness posture of mission essential components of the DII
- Detail the responsibilities and authorities of the DoD Chief Information Officer (CIO), the DoD CIO Council, the Senior DIAP Steering Group, the DoD Director of Information Assurance, the Information Assurance Group, and the DIAP Staff Director and Staff as they relate to the DIAP
- Ensure the DIAP is a partnership between OSD and its Components that is based on integrated planning, decentralized execution, and continuous centralized oversight
The DIAP is the Department’s management vehicle, which provides a common IA implementation framework, continuously monitors and integrates its IA activities, and maximizes the return on IA investments. The DIAP will accomplish this through creation of a dedicated staff consisting of a core set of DoD personnel augmented by Component IA Program Representatives (PR) and IA Functional Representatives (FR). Consistent with DoD policies, Component mission requirements, the Program Planning and Budgeting System (PPBS) and existing resources, Component PRs will be charged with maximizing their Component’s investment in their IA programs. In so doing, Components will be providing the IA operational capabilities (i.e., Protection, Detection and Response) required to assure the DII provides the reliability, availability, integrity, confidentiality and non-repudiation of information necessary to ensure the operational success of the Department.
DIAP Staff Functional Representatives, through analysis of the threat, Defense-wide operational requirements, and detailed knowledge of their functions, will determine the optimal mix of IA functions (i.e. readiness, Assessment, Human Resources, Operational Policy and Doctrine Implementation, Acquisition support and Product Development, and research and Technology). The continuous development and analysis of IA programs and functions will provide a picture of the DoD’s IA investments, and deficiencies in resources, functional and operational capabilities.
The Figure F-1 depicts a high level view of the DIAP. Subsequent narratives describe roles and responsibilities of the key components of the DIAP.
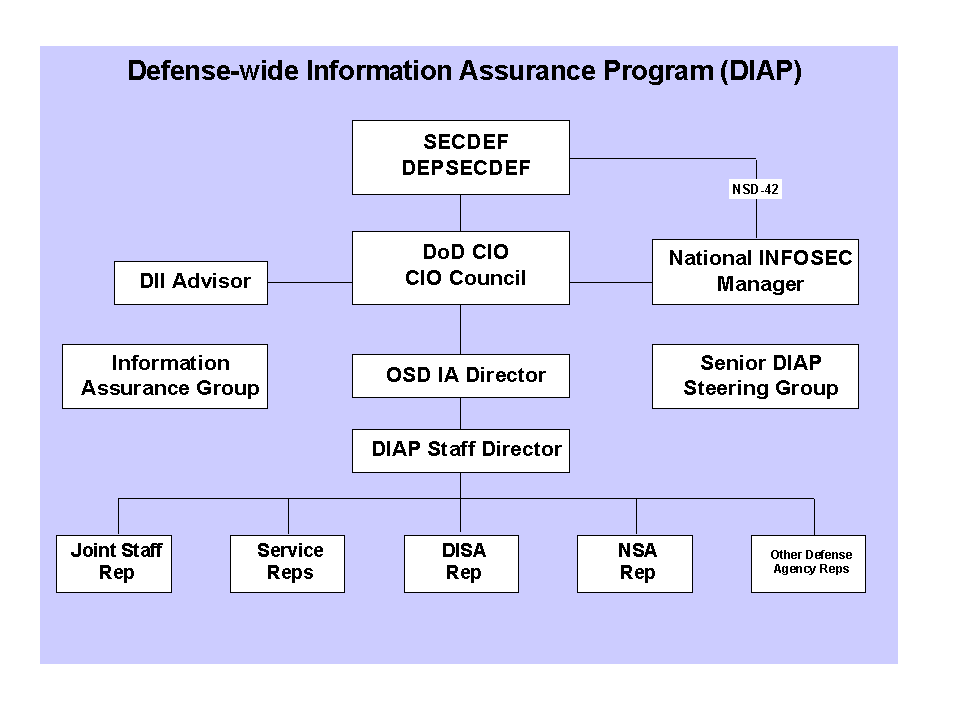 Figure F-1. DIAP Overview
Figure F-1. DIAP Overview
Chief Information Officer
The Department’s implementation of the Clinger-Cohen Act (Information Technology Management Reform) assigns the DoD CIO responsibility for ensuring information technology and information resources are meet the operational requirements. PDD 63 expands CIO responsibility to include IA.. The DIAP is the mechanism that will enable the DoD CIO to execute his Defense-wide IA responsibilities.
CIO Council
The current Charter for the DoD CIO Council mandates that the Council monitor and coordinate the Department’s investment review, budget formulation and financial execution processes for information technology (IT). At present, the membership of the DoD CIO Council does not include representation from all DoD Components with significant IA responsibilities. Given the DIAP’s scope and the interdependence of IA and IT, the DoD CIO will explore expansion of the Council to ensure balanced representation across DoD.
National Manager
Under the provisions of National Security Directive 42 (NSD-42), the Director, National Security Agency (DIRNSA), as the National Manager for National Security Telecommunications and Information Systems Security, is directly responsible to the Secretary and Deputy Secretary of Defense for ensuring the security of all National Security Systems. In conjunction with National Institute of Standards and Technology (NIST), the DIRNSA provides information systems security (INFOSEC) technical guidance, advice, and support to US Government departments and agencies. Under NSD-42, the DIRNSA also acts as the U.S. Government focal point for cryptography and INFOSEC for national security systems. In this capacity, DIRNSA will review and approve all standards, techniques, systems, and equipment related to the security of national security systems. The DIRNSA will also disseminate threat(s) to and assess the overall security posture and vulnerability of national security systems. The DIRNSA will annually assess the National Security Telecommunications and Information Systems Security Programs’ budget recommendations of the Executive departments and agencies for the Executive Agent. Consistent with the above authorities and responsibilities, and as a member of the Senior DIAP Steering Group, the DIRNSA will serve as an advisor to the DoD CIO on IA related national security issues.
Defense Information Infrastructure (DII) Advisor
The Director, Defense Information Systems Agency (DISA), with management responsibilities for the DII, is responsible to the Assistant Secretary of Defense of Command, Control, Communications, and Intelligence (ASD (C3I)) for the planning, development, and support of Command, Control, and Communications (C3), and information systems that serve the needs of the National Command Authorities (NCA) under all conditions of peace and war. Additionally, the Director, DISA, serves as the Department’s DII System Engineer providing end-to-end system engineering and direction, including network management and security for the DII. Consistent with these responsibilities, the Director, DISA, will serve as the DII Advisor to the DoD CIO and DoD CIO Council, and the Senior DIAP Steering Group.
DISA is responsible for assuring sufficient, cost effective communications services to DoD Components via the Defense Information Systems Networks (DISN). DISA applies modeling, simulation and assessment expertise to evaluate the level of efficiency and effectiveness of the DISN for its customers, for peacetime, contingency, and wartime scenarios, and to conduct impact assessments to support integration of new communication systems within the DISN.
Senior DIAP Steering Group
The DoD CIO, Director, DISA; the Joint Staff, J6; Director, NSA; and Service C4 Chiefs will constitute the membership of a Senior DIAP Steering Group. This group shall provide strategic advice to the DoD CIO and the DoD CIO Council on all IA issues.
Director, Information Assurance
The OASD(C3I) Director of Information Assurance is the principal advocate for IA throughout the Department. Additionally, he will supervise the DIAP Staff Director (SD) and oversee the daily operations of the DIAP Staff. The Director IA is also responsible to the DoD CIO for the overall operation of the DIAP and serves as Executive Secretariat for the Senior DIAP Steering Group.
Information Assurance Group (IAG)
Currently the Director, IA, is supported by the IAG, which serves as the Department’s principal IA forum. The IAG addresses a number of functional issues through a series of working groups that are composed of representatives from the DoD Components. The IAG Working Groups’ principal responsibilities include establishing functional objectives, furthering their Defense-wide development, integration, and coherent implementation, and developing DoD-wide performance criteria. The IAG Policy Working Group will continue to function and support the policy mission of the IA Directorate. While subject to modification, in implementing the DIAP, the present IAG Working Groups will be phased into the DIAP and provide virtual support teams to the following functional areas:
- Readiness Assessment
- Human Resources Development
- Operational Policy and Doctrine Implementation
- Security Management
- Operational Monitoring
- Architectural Standards and System Transformation
- Acquisition support and Product Development
- Research and Technology
The experience and expertise existing in the present IAG Working Groups will greatly enhance the initial operational capabilities of the DIAP. Accordingly the IAG Working Groups shall:
- Provide coordinated IA advice and recommendations to the Director, Information Assurance
- Support and develop coordinated Defense IA policies, strategies, and technologies, and other means required to mitigate information systems and network vulnerabilities while simultaneously providing adequate protection from activities that could reduce or deny the availability, security, and integrity of information and the systems and networks upon which DoD depends
- Identify and recommend actions to eliminate gaps and shortfalls in DoD IA activities and programs, and identify issues requiring review by the Director, IA, the Senior DIAP Steering Group, the DoD CIO Council, and the Defense Resources Board
- Serve as the principal, working level forum for recommending coordinated DoD positions, recommendations on all issues involving the end-to-end protection of the Defense Information Infrastructure
DIAP Staff Director (SD)
The SD shall be responsible for coordinating DIAP development within the DoD Planning Programming and Budgeting System (PPBS); developing a comprehensive process to assess the Department’s return on its IA investments; and providing for the continuous oversight of the execution of the Department’s IA policies, functions, and programs.
Services, Joint Staff, and Agencies
Services, Joint Staff, and Agencies will plan and execute their IA responsibilities consistent with DoD policy and direction, their operational requirements, the DoD Programming Planning and Budgeting System (PPBS) and direction provided by the DoD CIO through the DIAP.
The DIAP is composed of two teams. They are the Functional Evaluation and Integration Team and the Program Development and Integration Team. Figure F-2 depicts the interaction and integration process between the two teams.
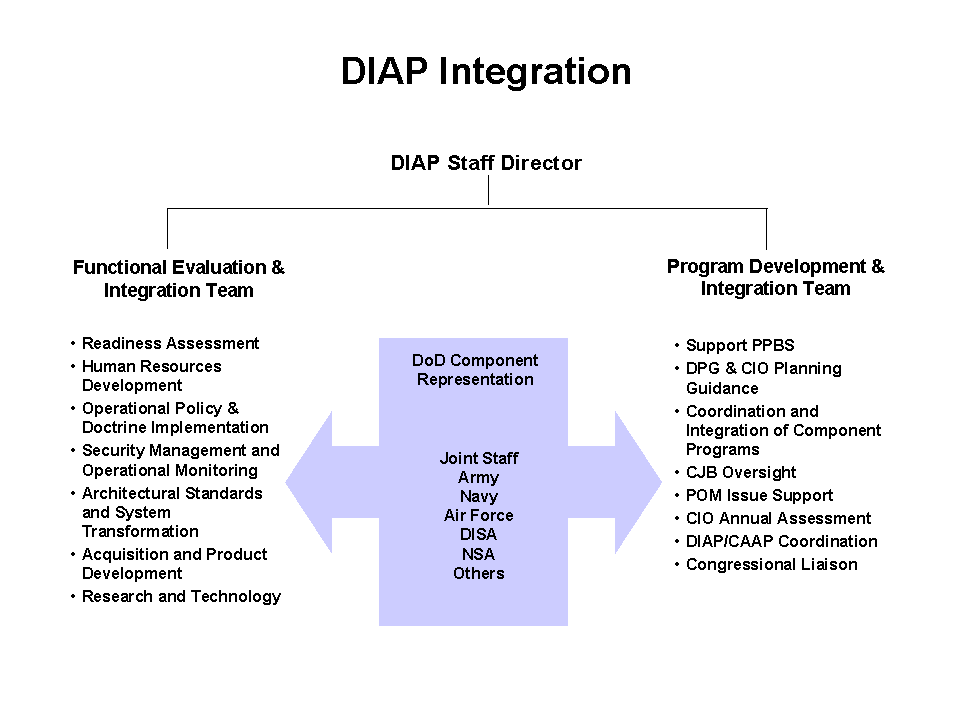
Figure F-2. DIAP Integration
Functional Evaluation and Integration Team (FEIT)
Subject to changes in information technologies, threat, and DoD-wide missions, the FEIT will initially be composed of assigned DoD IA experts in each of the functional areas listed below. FEIT members will be charged with the development of performance goal and oversight of their respective functions (listed and defined in Table F-1) and their coherent integration through the DoD.
TABLE F-1. FEIT Functional Areas and Responsibilities
|
Provides data needed to accurately assess IA readiness and for use in focusing plans and decisions in the PPBS
|
|
|
Human Resources |
Provides for sufficient, adequately trained and educated personnel to conduct IA functions throughout the DoD
|
|
Operational Policy and Doctrine Implementation |
Provides for objective assessment of the implementation of DoD IA related policies and doctrine throughout the DoD. National Security Policies/Priorities DoD IA Policies/Priorities DoD Component Missions & Doctrine Policy Implementation/Adherence Defense-wide IT/IA Interoperability |
|
Security Management and Operational Monitoring |
Provides the IA services needed to operate and monitor information systems and networks in a manner consistent with policy, doctrine, and operational requirements.
|
|
Architectural Standards and System Transformation |
Provides for the integration of adequate IA technologies, products, and supporting procedures in the information technologies and information systems and networks acquired by the DoD.
|
|
Acquisition Support and Product Development |
Provides guidance to the commercial sector regarding the IA requirements of the DoD and provides a means for determining whether commercial-off-the-shelf (COTS) or Government produced products best satisfy DoD requirements.
|
|
Provides for the research for the development of IA technologies and techniques consistent with current and anticipated DoD mission needs and changes in information technologies.
|
FEIT members, in collaboration with DoD, and in coordination with government, commercial, and academic community subject matter experts will:
- Be the DIAP’s principal evaluators for their particular function
- Ensure the program integration of their particular functions with the other functions in the FEIT
- In coordination with the members of the Program Development and Integration Team (PDIT), be responsible for the continuous evaluation of Component IA programs to ensure the Defense-wide application of the FEIT’s capabilities and functions are consistent, integrated, efficient, and programmatically supported
- In those instances where IA Component programs fail to provide the resources necessary to adequately protect the DII, the FEIT will, in coordination with the PDIT, develop program recommendations within the DIAP to resolve the problem.
In those instances where programmatic solutions cannot be found, the FEIT will, in coordination with the PDIT, develop Program Objective memorandum (POM) and budget issues for submission to the Senior DIAP Steering Group, the DoD CIO and DoD CIO Council.
- With the approval of the DoD CIO, the FEIT, in collaboration with the PDIT, will provide support to PA&E presentation of the DIAP Issue to the Defense Resources Board and to the Joint Staff presentation to the Joint Requirements Oversight Council (JROC)
Program Development and Integration Team (PDIT)
The PDIT and its Component Program Representatives will be responsible for the oversight, coordination, and integration of the DoD’s IA resource programs. The PDIT will:
- Develop broad, easily understood, operationally oriented, DIAP program categories (e.g., Protect, Detect, and React) that will serve as the foundation and identify the operational capabilities of the DIAP
- Develop input to the Defense Planning Guidance for DIAP Components. Oversee Component participation in the PPBS
- Continuously monitor the IA plans, activities, and resource investments of the DoD Components, and in conjunction with the Critical Asset assurance Program (CAAP), assess the adequacy of resources necessary to ensure the continuous operational readiness of the DII
- On behalf of the DoD CIO, prepare Program Guidance for the DIAP
- Staff and correlate responses to IA program queries from the congress, OUSD (Comptroller) and the Office of Program Analysis and Evaluation (PA&E)
- Prepare and coordinate the DoD CIO’s Annual IA Assessment
- Develop, coordinate and support DoD-wide program and resource issues for submission by the Director, IA, to the Senior DIAP Steering Group, and provide support to PA&E as part of the DRB process
- Review, and as appropriate, recommend adjustments to the Component POMs to support the Integrated Priority Lists (IPLs) of the Combatant Commanders
- Beginning with the FY 2000 edition, and in coordination with the Information Systems Security Program Staff, prepare the DIAP Congressional Justification Book (CJB)
- Work with the OUSD(Comptroller) and PA&E staffs to design and implement appropriate budget exhibits for collecting, monitoring, and reporting DIAP resources
- Develop and coordinate input for the IA portion of the DoD Information Technology Strategic Plan
Common IA Implementation Framework
To manage the shared risk and ensure an acceptable level of infrastructure protection and information assurance across the DII, a common implementation is required. A common implementation framework will guide those who are responsible for determining their information assurance requirements. Through this common implementation framework, the DIAP will help ensure that equivalent protection (IA measures) is provided for comparable information and systems. The framework can be expected to evolve and change over time in response to changing requirements and environments.
The implementation framework will consist of Mission Critical Categories to help define the Level of Assurance required, Levels of Assurance at which the system or network will operate, and Minimum Assurance Requirements to be implemented within each Level of Assurance.
Mission Critical Categories
The intent is to encourage a culture change that places value on information based upon the contribution the information makes toward mission accomplishment and warfighting missions, rather than the classic information valuation, which is largely based upon the national security classification of the information. Such a change would recognize that the value of information is not static. Mission Criticality of the information is one of the factors to be considered in assigning the Level of Assurance to an information system or network. Thus, information value and the strength of the assurance measures are based upon the importance of the information to the DoD’s mission.
Levels of Assurance
Each DoD system and network will be developed, managed and operated in accordance with the criteria and requirements of one of the Levels of Assurance: Basic, Medium, or High, defined as minimal, increased or most stringent levels of assurance. The definitions provide a general understanding for the concepts of LoA but the definitions are not "implementable" without further amplifying guidance. Criteria and requirements will be identified by the DoD Chief Information Officer (CIO) for each LoA. Consideration might be given to revising the definitions to make them more implementable; however, IA is a dynamic discipline and it may be worthwhile to let the definitions remain "conceptual," adding the granularity necessary for implementation in subordinate policy and guidance. LoAs are key to cross-leveling assurance measures across all DoD systems and networks. It is envisioned that they will conserve and help focus resources and will provide users at each level some assurance that (1) all systems operated at that level have met specific requirements, and (2) each level is isolated or protected from the vulnerabilities and weaknesses of systems managed and operated at a lower level of assurance. Levels of Assurance do not map to traditional classification levels (e.g., basic level to unclassified; medium level to secret; and high level to top secret). In fact, there will most likely be an unclassified infrastructure or Defense Sector, which will support all three levels of assurance within the infrastructure (there will be a certified process similar to Secret and Below Interoperability (SABI) to go between levels of assurance).
Required Processes and Minimum Assurance Requirements
For each LoA, Required Processes and Minimum Security Requirements will be mandated by the DoD CIO. The focus of these mandates will be protecting the infrastructure and ensuring that undue weaknesses in the systems of one DoD organization do not threaten the assurance of other organizations’ systems.
The required processes include the DoD of Defense Information Technology Security Certification and Accreditation Process (DITSCAP), the Secret and Below Interoperability (SABI) Process, the Top Secret and Below Interoperability (TABI) Process, and the Defense Information System Network (DISN) Connection Approval Process (CAP). Minimum Assurance Requirements are expected to include technical, operational, and personnel requirements.
Guiding Principles
The implementation framework is based on a foundation of principles or precepts. These principles guide the development and evolution of the implementation framework and minimum assurance requirements, in much the same sense that the foundation of a building prescribes the general shape of the building. Preliminary guiding principles are listed below:
- The purpose of Levels of Assurance is to mitigate the shared risk created by the interconnection of systems and networks in the DII
- Levels of Assurance apply to information systems and networks, not to data or information.
- Mission criticality, and other requirements, of data and information is a factor in determining the system LoA
- Systems and networks supporting a functional area (logistics, personnel, finance, etc.) may require different levels of assurance; e.g.; some logistics systems may require High Assurance; others may require Medium or Basic Levels of Assurance
- Systems assigned a High LoA will generally require stringent security features in all security attributes (Confidentiality, Integrity, Availability, Authenticity, and Nonrepudiation)
- Systems assigned a Medium Level of Assurance will generally require stringent security features in a subset of the security attributes
- There is not a one-to-one correspondence between LoA and Mission Criticality. Mission Criticality and Interconnectivity may, however, be dominant factors in determining required Levels of Assurance
- Levels of Assurance apply to all information systems and networks. In addition to meeting the requirements based on LoA, systems processing national security information will meet the requirements of Public Law, National policy and other DoD policy
- Systems processing information for which special handling or protection is required by Public Law, Federal Regulation or Executive Order, will, at a minimum, be assigned a Basic LoA
In addition to meeting the requirements based on LoA, systems processing such information will meet the requirements of Public Law, National policy, and other DoD policy.
Mission Critical Categories, Determining Levels of Assurance, and Information Assurance Roadmap
Determining Mission Critical Categories
The purpose of the mission critical categories is to assist the operators in defining and implementing assurance measures. The categories were incorporated to inaugurate a change in culture where the value of information, information systems, and networks and the assurance measures that are implemented are based upon the relative importance of the information, information system, and networks to the accomplishment of the DoD’s missions. It would be fiscally impossible and technically challenging, if not impossible, to provide absolute assurance for the preponderance of information which is distributed over highly interconnected, largely public, information systems. Assurance provided must be commensurate with the value of the information. This is the essence of IA.
Knowing the value—mission criticality—of information, system, and/or network is also critical in determining the appropriateness of crisis actions taken to protect or restore information or capabilities. Network and security managers must be able to triage requirements for restoration and extraordinary protective and response measures.
- Key Concepts
The following concepts are key to understanding and implementing mission critical categories. These concepts will likely be modified as IA implementation discussions widen.
- The mission criticality of information handled is one of the factors to be considered in determining the appropriate LoA of an information system or network
There is not a one-to-one correspondence between mission criticality and LoA; however, information may be so critical to mission accomplishment that it becomes a dominant factor in determining the appropriate LoA.
- It is conceivable that the mission critical categories of the same information may change based upon where and how the information is used
For example, personnel information, although detailed and aggregated in large databases, would be Administrative when used within the personnel function for routine purposes such as reassignments and calculating and reporting gross numbers. However, personnel information on unit strengths or shortages of key military specialties in forward or deployed units might be considered Mission Support.
- Within the Services and Agencies various mission criticality ratings already exist
The objective of a standard DoD-wide mission critical category system recognizes the joint nature and requirements of day-to-day and crisis operations and contributes to the provision of equivalent assurance provided for comparable systems and fosters a level of trust across the DII user population.
- Mission Critical Categories
The categories are repeated below along with amplifying remarks.
- Mission Essential : Any information that is determined to be vital to the operational readiness or mission effectiveness of deployed and contingency forces in terms of both content and timeliness. The information must be absolutely accurate and available on demand.
- Mission Support : Information that is important to the support of deployed and contingency forces. It must be highly accurate, but can sustain minimal delay without seriously affecting operational readiness or mission effectiveness. DoD lexicons already include concepts for mission or combat support. The Mission Support category is not intended to be equivalent to "combat support." For example, logistics is considered a combat support function, however, logistics information may range from Administrative to Essential.
- Administrative : Information that is necessary for the conduct of the day-to-day business of the DoD, but does not materially affect support to the deployed forces or the readiness of contingency forces in the short term. Authentication and integrity of administrative information is more important in terms of fraud, waste, and abuse than in terms of its direct effect on the operational readiness or mission effectiveness of deployed or contingency forces.
Determining Levels of Assurance
- General Approach
LoAs are based upon risk, threat, vulnerability and system interconnectivity and specific assurance needs for Confidentiality, Integrity, Availability, Authenticity, and Nonrepudiation, as well as training, engineering and installation disciplines, and supporting critical infrastructures. The general approach envisioned is depicted in Exhibit F-3.
In the approach, Confidentiality, Integrity, Availability, Authentication, and Nonrepudiation are used in their classic (NSTISSI 4009) applications. Interconnectivity addresses the concept that interconnected systems and networks should be managed and operated at the same level of assurance. Mission criticality and interconnectivity may be dominant factors in determining LoA, while the majority of Confidentiality, Integrity, Availability, Authentication, and Nonrepudiation requirements may be addressed as Unique system requirements (Step 3 of the general approach).
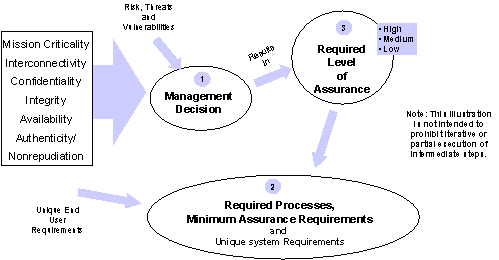
Exhibit F-3. General Approach for Determining Levels of Assurance
Each system and network will be designed, built, operated and maintained for its entire life cycle at one of the assurance levels." The assurance level determination requires a management decision based on risk, threat, vulnerability and system interconnectivity considerations and specific assurance needs (i.e., Confidentiality, Integrity, Availability, Authenticity, and Nonrepudiation). The decision authority should be a management official (someone in the operational chain of command) knowledgeable in the nature and use—the mission criticality—of the information. Due to the similarity in the requirements, this would likely be the Defense Sector Lead Agency. As a minimum, one would expect the decision authority to be at least one organizational level above the person responsible for ensuring the security of an information system, e.g., the Information Systems Security Officer (ISSO). Because of the technical considerations (threat, vulnerability, and interconnectivity) a technical advisor could provide valuable contributions to the decision process. This technical advisor might serve as the Certifying Authority for the system or as the Information Systems Security Manager (ISSM) for the Defense infrastructure.
- Required Processes
Figure F-4 is a conceptual depiction of the requirements and criteria that might be associated with each LoA. In the first box, the manager is depicted as having determined that the system should be managed and operated at a Medium level of assurance. Box 2 depicts two processes that may be associated with LoAs. The DITSCAP prescribes four Certification Levels. Level 4 requires the most rigorous certification effort, while Level 1 is the least rigorous. Box 2 postulates that DoD CIO guidance requires Medium Assurance systems to undergo a Level 3-certification process. It also postulates that, due to connectivity requirements, the system must undergo a Secret Internet Protocol Router Network (SIPRNET) Connection Approval Process (CAP).
Box 3 reflects the DoD CIO mandated requirements for technical, operational, and personnel assurance measures for Medium assurance systems and networks. Box 4 reflects the requirement that responsible managers determine what, if any, unique requirements the system may have for Confidentiality, Integrity, Availability, Authenticity, and Nonrepudiation. For example, a system may have a unique requirement for high availability. This may require additional assurances in the area of supporting infrastructures, engineering and installation. A typical example of unique requirements may be the confidentiality requirements afforded national security information.
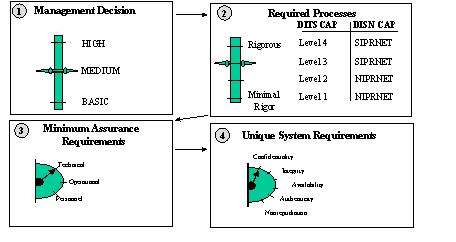
- One-to-one Correspondence.
- Relationship to Classified Information. LoAs should be assigned without regard for the national security classification of the information processed or transported. As noted in the Guiding Principles, requirements for the security of classified information are "additive" to the requirements of the LoA.
- Similar Processes. The DITSCAP uses Information Technology Security (ITSEC) Levels and Certification Levels to indicate the criticality of information systems and the rigor of the certification process. All DoD systems are required to be certified and accredited in accordance with the DITSCAP process [Department of Defense Instruction 5200.40 Dec 30, 1997]. Some consideration should be given "mapping" the LoAs and ITSEC Levels, thus minimizing the number of processes required of field activities. The evolving Common Criteria and associated Evaluation Assurance Levels (EAL) should also be monitored for future mapping or incorporation into LoAs.
Minimum Assurance Requirements
GENERAL
"Detailed assurance criteria for each level, and for interconnection between levels, will be specified by the DoD CIO." It is intended that the "detailed assurance criteria," will, in addition to providing a common implementation framework and process, establish minimum assurance requirements. These minimum assurance requirements are not intended to subvert the responsibilities of the Commanders-In-Chief/Services/Agencies (C/S/A). They will be infrastructure-centric, intended to protect the infrastructure—the DII backbone—and provide a level of trust and assurance for all users of the DII, that the assurance measures provided their applications, systems, and connected networks, will not be undermined by weaknesses and vulnerabilities of interconnected systems and networks.
The Table F-2 presents the guidance [IA Roadmap; MCEB Interim Guidance] approved by the Military Communications-Electronics Board (MCEB) in January, 1998, which contains minimum assurance requirements agreed to by the Joint Staff and Services.
TABLE F-4. Information Assurance Roadmap
|
INFORMATION ASSURANCE ROADMAP MCEB Interim Planning Guidance |
|||
|
NIPRNET |
SIPRNET |
DII - General |
|
|
Certification and Accreditation |
C/S/As should immediately implement the provisions of DoDD 5200.40, Defense Information Technology Security Certification and Accreditation Process (DITSCAP), 30 Dec 97. |
||
|
Connection Approval |
Connection approval requirements will be published by DISA and CJCS. |
Interim network connection requirements (DISA msg, 121713Z Dec 95. |
|
|
Data Labeling |
Components to develop implementing instructions for labeling new information when it is produced. |
||
|
|
|
Commercial firewall use based on NSA recommended security settings. NSA assistance recommended |
|
|
Foreign Connection |
Foreign connection only through approved (SABI Process) security devices (guards) |
||
|
Intrusion Detection |
Intrusion detection capabilities must be employed within the Local Subscriber Environment (LSE) and at the local subscriber connection to a non-DoD or Commercial network. C/S/A goal should be to meet network protection standards NLT FY 00. |
Intrusion detection capabilities must be employed within the LSE and at SABI connections on both low and high sides. C/S/A goal should be to meet network protection standards NLT FY 00. |
Intrusion detection in use includes Network Intrusion Detector (NID), Joint Intrusion Detector (JID) and Automated Security Incident Measurement (ASIM). No standard but JID is available at no cost. |
|
Labels & Marking |
Text markings on soft copies and fields in databases (for all new information as products) |
||
|
Operator Licensing |
All operators of systems connected to the NIPRNET will be licensed by Dec 00 |
All operators of systems connected to the SIPRNET will be licensed by Jan 99 |
|
|
Personnel Security Program |
All DoD systems and network SAs, regardless of sensitivity, will participate in a Personnel Reliability Program (PRP)-like program by Oct 2003. |
||
|
Public Key Infrastructure (PKI) |
|
|
A single DoD PKI will be developed. PKI functionality will be integrated into SIPRNET/DMS/GCCS/Classified and NIPRNET/GCSS. Services should program to provide digital signature and identity certificate capability NLT FY 03. |
|
Secret and Below Interoperability (SABI) |
All implementations must be approved (by end of FY 98) or be disconnected from the SIPRNET. |
Commercial firewalls should not be used as sole protection |
|
(page is intentionally blank)
Appendix G: Defense Infrastructure Sector Assurance Plans
Defense Sector Assurance Plans shall be submitted annually to the CIAO through the Director, Critical Infrastructure Protection for consolidation in the DoD Critical Infrastructure Protection Plan. The DoD Critical Infrastructure Protection Plan will be updated annually and submitted biennially to the National Coordinator for Security, Infrastructure Protection, and Counter-terrorism. Defense Sector Assurance Plans will address but are not limited to:
- Contact information for the Sector Assurance Office
- A description of the Defense Sector. Subsequent year Plans will focus on Sector changes
- Registration of Sector Critical Assets in CAAP, to include Sector National Defense Assets, e.g., Critical Industrial Assets as defined by DoDD 5160.54
- Sector assurance goals and a review of the previous year’s assurance goals and accomplishments
- A two-year projected schedule of assurance activities and resources
Assurance activities could include analysis and assessments, remediation, mitigation, monitoring and reporting, and reconstitution.
- A compendium of reportable incidents and associated guidelines for monitoring and reporting. Sector reportable incidents should include nationally defined reportable incidents, DoD defined reportable incidents, and Sector defined reportable incidents
Guidelines for monitoring and reporting should include for each reportable incident or class of reportable incidents: who is required to monitor; at what interval; how soon a report should be submitted; what information elements it should contain; how it should be routed; and what follow-up actions are required.
- A summary of previous year monitoring and reporting and planned or required improvements
- Research and development requirements
- Intelligence requirements (through appropriate channels)
- Interagency National Defense, Legal, Policy or Programming Issues
(page is intentionally blank)
|
ASD(C3I)
AT/FP |
Assistant Secretary of Defense for Command, Control, Communications, and Intelligence Antiterrorism Force Protection |
|
C3 |
Command, Control, and Communications |
|
CAAP |
Critical Asset Assurance Program |
|
CAP |
Connection Approval Process |
|
CIA |
Central Intelligence Agency |
|
CIAO |
Chief Infrastructure Assurance Officer |
|
CICG |
Critical Infrastructure Coordination Group |
|
CINCs |
Commander-in-Chiefs of the Unified Combatant Commands |
|
CIO |
Chief Information Officer |
|
CIP |
Critical Infrastructure Protection |
|
CIPP |
Critical Infrastructure Protection Plan |
|
JTF-CND |
Joint Task Force - Computer Network Defense |
|
COMPUSEC |
Computer Security |
|
COMSEC |
Communications Security |
|
COOP |
Continuity of Operations Plan |
|
COTS |
Commercial-off-the-shelf |
|
DASD |
Deputy Assistant Secretary of Defense |
|
DDR&E |
Director, Defense Research and Engineering |
|
DFAS |
Defense Finance and Accounting Service |
|
DFAS |
Defense Finance and Accounting Service |
|
DHRA |
Defense Human Resources Agency |
|
DI |
Defense Infrastructure |
|
DIA |
Defense Intelligence Agency |
|
DIAP |
Defense-wide Information Assurance Program |
|
DII |
Defense Information Infrastructure |
|
DIRNSA |
Director, National Security Agency |
|
DISA |
Defense Information Systems Agency |
|
DISN |
Defense Information System Network |
|
DITSCAP |
Department of Defense Information Technology Security Certification and Accreditation Process |
|
DLA |
Defense Logistics Agency |
|
DoD |
Department of Defense |
|
DoD(GC) |
Department of Defense General; Counsel |
|
DoJ |
Department of Justice |
|
DOMS |
Director of Military Support |
|
DoS |
Department of State |
|
EAL |
Evaluation Assurance Levels |
|
EO |
Executive Order |
|
FBI |
Federal Bureau of Investigation |
|
FEIT FP |
Functional Evaluation and Integration Team Force Protection |
|
FOC |
Full Operating Capability |
|
GCCS |
Global Command and Control System |
|
GCSS |
Global Combat Support System |
|
GIS |
Geographic Information System |
|
I & W |
Indications and Warning |
|
IA |
Information Assurance |
|
IAG |
Information Assurance Group |
|
IAP |
Infrastructure Assurance Program |
|
IAW |
In Accordance With |
|
IMS |
Information Management Systems |
|
INDI |
International Defense Infrastructure |
|
INFOSEC |
Information Systems Security |
|
IOC |
Initial Operating Capability |
|
IPL |
Integrated Priority List |
|
IPTF |
Infrastructure Protection Task Force |
|
ISAC |
Information Sharing and Analysis Center |
|
ISR |
Intelligence, Surveillance, and Reconnaissance |
|
ISSM |
Information Systems Security Manager |
|
ISSO |
Information Systems Security Officer |
|
IT |
Information Technology |
|
ITMRA |
Information Technology Management Reform Act |
|
ITSEC |
Information Technology Security |
|
IWG JSIVA |
Interagency Working Group JSIVA Joint Staff Integrated Vulnerability Assessment |
|
JPO-STC |
Joint Project Office for Special Technology Countermeasures |
|
JROC |
Joint Requirements Oversight Council |
|
LoA |
Level of Assurance |
|
MCEB |
Military Communications-Electronics Board |
|
NCA |
National Command Authorities |
|
NCS |
National Communications System |
|
NDI |
National Defense Infrastructure |
|
NDU |
National Defense University |
|
NIAC |
National Infrastructure Assurance Council |
|
NIAP |
National Infrastructure Assurance Plan |
|
NIMA |
National Imagery and Mapping Agency |
|
NIPC |
National Infrastructure Protection Center |
|
NIST |
National Institute of Standards and Technology |
|
NMCC |
National Military Command Center |
|
NMJIC |
National Military Joint Intelligence Center |
|
NPC |
National Plan Coordination |
|
NS/EP |
National Security/ Emergency Preparedness |
|
NSC |
National Security Council |
|
NSS |
National Security Systems |
|
NSTAC |
National Security Telecommunications Advisory Committee |
|
NSTC |
National Science and Technology Council |
|
NSTISSI |
National Security Telecommunications and Telecommunications and Information Systems Security Instruction |
|
OASD |
Office of the Assistant Secretary of Defense |
|
ODASD(S&IO) |
Office of the Assistant Secretary of Defense for Security and Information Operations |
|
OPSEC |
Operations Security |
|
OSD |
Office of the Secretary of Defense |
|
OSTP |
Office of Science and Technology Policy |
|
OUSD(C) |
Office of the Under Secretary of Defense (Comptroller) |
|
OUSD(P) |
Office of the Under Secretary of Defense for Policy |
|
PA&E |
Program Analysis and Evaluation |
|
PCCIP |
President’s Commission on Critical Infrastructure Protection |
|
PDD |
Presidential Decision Directive |
|
PDIT |
Program Development and Integration Team |
|
PIR |
Priority Intelligence Report |
|
POM |
Program Objective Management |
|
PPBS |
Program Planning and Budgeting System |
|
PSA |
Principal Staff Assistant |
|
R&D |
Research and Development |
|
RAL |
Registered Asset List |
|
SABI |
Secret and Below Interoperability |
|
SD |
Staff Director |
|
SECDEF |
Secretary of Defense |
|
SIPRNET |
Secret Internet Protocol Router Network |
|
TABI |
Top Secret and Below Interoperability |
|
US |
United States |
|
USACE |
US Army Corps of Engineers |
|
USACOM |
US Atlantic Command |
|
USSPACECOM |
US Space Command |
|
USTRANSCOM |
US Transportation Command |
|
WMD |
Weapons of Mass Destruction |
 [Presidential Decision Directives - PDD]
[Presidential Decision Directives - PDD]