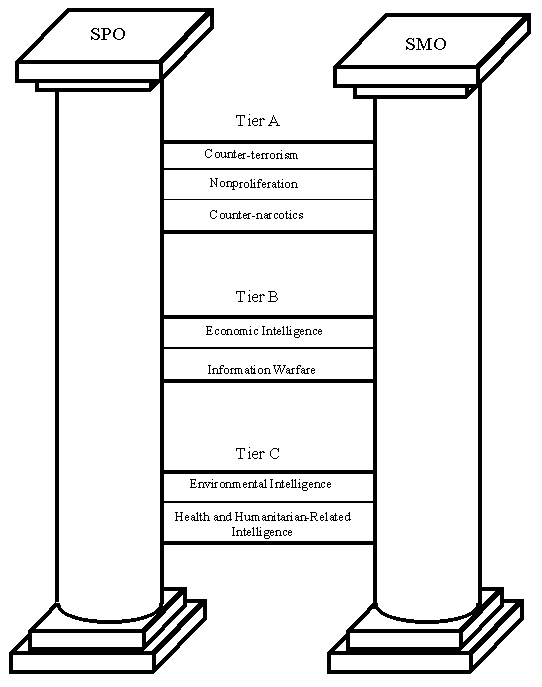
Chapter 3: The Three Tiers of the PCW Framework and Their Relationship to the Pillars

The PCW framework has three tiers which help prioritize the various IC missions. Although each tier represents a different priority level, they all make a contribution to the two pillars of SPO and SMO, and together they create an integrated IC structure. Expounding on each of the tiers and their principal missions will help flesh out the PCW framework, as well as provide insight into specific reforms for particular missions. Amongst the many reform issues, a few recommendations will surface repeatedly. These common threads to intelligence reform will be further discussed in Chapter 4.
3.1 Tier A: High Priority Missions
Missions are placed in Tier A only if they present critical and imminent concerns to national security and deserve IC attention. Under normal circumstances, Tier A missions are natural and important extensions of the two pillars, SPO and SMO, and thus supersede missions of other tiers. Notably, the three Tier A missions examined in this section are transnational in nature: nonproliferation, counterterrorism, and global organized crime and counternarcotics.
3.1.1 Nuclear Nonproliferation
With the collapse of the Soviet Union, the proliferation of weapons of mass destruction has emerged as the single most dangerous threat to the national security of the United States. Indeed, in this era of uncertainty and emerging threats, the importance of maintaining a strong, coordinated approach to managing US nonproliferation intelligence is greater now than it has been ever before.
Through the creation of the Nonproliferation Center (NPC) in the CIA, reorganization of the Department of Energy's (DoE's) intelligence management, and expanded interaction between the intelligence and policy communities, the United States has worked to improve nonproliferation intelligence capabilities. However, to insure that the IC is well prepared to face future challenges, reform efforts must improve governmental accountability and strengthen inter-agency coordination in the nonproliferation arena.
Strengthen the authority of the National Nonproliferation Coordinator and the National Security Council Committee on Nonproliferation to coordinate US Nonproliferation efforts.
The National Defense Authorization Act for Fiscal Year 1997 creates a national coordinator on nonproliferation whose responsibility is to advise the President on nonproliferation and related threats, including terrorism (Section 3.1.2) and international organized crime (Section 3.1.3), which are also Tier A missions. In addition, the provision establishes a committee on nonproliferation. This committee is to be chaired by the coordinator and composed of members of the Executive branch who have responsibilities for crisis and consequence management, nonproliferation, and related issues.(7)
While President Clinton is selecting this coordinator and appointing the members of the new NSC nonproliferation committee, it is absolutely critical that this national coordinator be incorporated into the formal NSC structure and be given the budgetary and personnel authority necessary for directing US nonproliferation activities. The coordinator must be accountable to the National Security Advisor and must have the means to mobilize the offices of the NSC. Also, the NSC Nonproliferation committee should assist the coordinator and should include the following members, or their designated appointees: 1) DCI, 2) Secretary of Defense, 3) Secretary of State, 4) Secretary of Energy, 5) Secretary of Commerce, 6) Secretary of Treasury, 7) Attorney General, 8) Director of the Arms Control and Disarmament Agency (ACDA), and 9) Director of the Federal Emergency Management Agency (FEMA).
The national coordinator must be given strong authority with the support of the NSC and the IC to ensure that the United States maintains a fully coordinated nonproliferation apparatus. (Currently, the Director of the NSC's Office of Nonproliferation and Export Controls does not have the time, nor the authority, to adequately coordinate the government's nonproliferation efforts.) Furthermore, the NSC Nonproliferation committee must be composed of the high-level officials to insure full inter-agency cooperation throughout the Executive Branch.
Include a greater number of non-CIA analysts in the Nonproliferation Center (NPC).
Although the NPC has increased the financial and human resources devoted to nonproliferation monitoring, it has not been as effective in improving coordination among the agencies of the IC. The NPC has had trouble attracting employees from outside the CIA, and is unfortunately viewed by many experts as a creature of the CIA.(8)
Greater efforts must be made to increase the number of analysts from Energy, Defense (especially from the Defense Intelligence Agency (DIA), National Security Agency (NSA), and the National Reconnaissance Office (NRO)), State (e.g. ACDA), Commerce, Treasury, Justice (especially FBI). The NPC should also include a representative from the Arms Control Intelligence Staff (ACIS). Each of these departments and agencies should have several senior analysts working at the NPC to ensure that the NPC fulfills its primary function as an intelligence coordination mechanism.
Develop a new position of "National Intelligence Officer for Nonproliferation" on the National Intelligence Council (NIC) to centralize the drafting of nonproliferation national intelligence estimates.
Nonproliferation estimates on the NIC are currently divided among three different National Intelligence Officers (NIOs). As a result, no single individual in the IC can really be identified as the expert on nonproliferation issues.(9)
By centralizing nonproliferation estimates around the new NIO for Nonproliferation, the IC can better focus its attention, help coordination, and increase accountability.
Improve the quality of finished intelligence products relating to nonproliferation.
Since nonproliferation is such a technical field, seamless coordination between CIA analysts and the nuclear experts at Department of Energy (DoE) laboratories is essential when drafting reports for the policy community. Without input from DoE, CIA reports may tend to lack technical depth, and without input from CIA analysts, DoE reports may tend to be dated. Unfortunately, this interaction between experts is not as strong as it needs to be. According to Gary Samore, the President's Senior Director for Nonproliferation and Export Controls "there has been friction between the CIA as an institution and the DOE as an institution and there have not been good cross-currents between the two agencies -- which means that the product is not as good as it should be."(10)
The IC must make greater efforts to improve DoE and CIA coordination to ensure that policy-makers get the best possible products.
Increase the role of HUMINT in gathering nonproliferation intelligence.
As Section 4.2 will further discuss, post-Cold War threats, especially the transnational ones from Tier A, require additional HUMINT support. The technological reconnaissance that was so successful tracking the Soviet nuclear arsenal is not as effective monitoring nuclear smuggling, determining the security of fissile material, or assessing whether or not nuclear scientists are earning a decent living (in which case they may sell their technical expertise).(11)
With its unique ability to gain human perspectives by infiltrating criminal organizations and foreign governments, HUMINT is an essential tool in a world of hidden transnational threats. While there are greater intelligence risks involved in HUMINT, the post-Cold War era requires intelligence officers to ask questions that really cannot be answered by technical means. HUMINT, supplemented by technical intelligence (TECHINT), is the only way to paint a complete picture.
Develop a comprehensive information service for nuclear nonproliferation intelligence.
The CIA must develop a system through which policy makers can regularly keep abreast of all the reports and information produced by the IC. Perhaps the best way to provide this information would be through a computer-based, information network like INTELINK and others used to facilitate coordination later recommended in Section 4.3. This secure version of the Internet would only be used by intelligence professionals and policy makers. Had such a system been in place in 1991, the United States (and the rest of the world community) might have entirely avoided the intelligence failure regarding Iraq's nuclear program.
Improve information analysis of open-source materials relating to nuclear nonproliferation issues.
Although technology and clandestine intelligence collection activities are still the most effective means of evaluating the nuclear capabilities of other nations, the "transparency agreements" binding on the US and the former Soviet Union have created an explosion of information from the academic and scientific communities. Many American professors, scientists, and NGOs work right along side Russians and can often produce information that is just as detailed and useful to the national security community as clandestine intelligence material. A greater effort needs to be placed on processing all of the information that is pouring out of Russia, and the intelligence community needs to include a greater emphasis on open-source information in its security calculus. This emphasis can be facilitated by implementing the Civilian Intelligence Reserve Corps recommended in Section 4.3 and increasing rotational assignments with academia, industry, NGOs as in Section 4.4.
Continue to increase informal US intelligence support of IAEA efforts
Currently, the International Atomic Energy Agency (IAEA) has great difficulty collecting information on foreign clandestine development of nuclear weapons; the agency has virtually no intelligence production tools of its own and must rely solely on the good will of international intelligence agencies and Nuclear Nonproliferation Treaty member nations. If the IAEA is going to inspect and enforce nuclear safeguards effectively, it must have the information to track the development of nuclear programs. With the approval from the State Department, the United States should provide intelligence support to the IAEA to the greatest possible extent without compromising American intelligence methods or upsetting the delicate international balance of the IAEA.
Charge the new Congressional Nonproliferation Commission to focus on:
i) Studying how to improve coordination among the agencies in the IC
ii) Improving cooperation between intelligence and the FBI
iii) Studying the effectiveness of International Export Controls
vi) Monitoring the security of Fissile Material Located Outside of the Russian Military Complex
The Intelligence Authorization Act of 1997 established a Congressional Commission to Assess the Organization and Structure of the Government for Combating Proliferation.(12)
This Commission needs to insure that under the current intelligence structure, US policy makers are fully briefed on how well US nonproliferation efforts are coordinated. Also, the Congressional Commission must seriously focus on how to better monitor international export controls and secure weapons grade material. Tracking the movement and security of nuclear materials is extremely difficult to monitor and is one of the weakest aspects of US intelligence monitoring. The Commission should consider creating a specialized office in the NPC to coordinate export control information and to monitor supply routes for weapons grade material.
3.1.2 Counterterrorism
Whether for political gain or in the name of some religious ideology, terrorist groups continue to disrupt global security in the post-Cold War era by inflicting casualties, causing economic damage, and destabilizing countries. "Traditional" terrorist actions over the past decade have sadly included the bombing of Pan Am Flight 103 over Scotland, the bombing of a US military base in Saudi Arabia, the bombing of the World Trade Center, and the hostage-taking incident (initially involving US diplomats) at the Japanese Embassy in Peru. Unfortunately, in the technology-based post-Cold War world, terrorist groups have shown no signs of cessation, and the US must now additionally guard against new types of terrorism, including those which attack infrastructures and economies.
As part of its responsibilities to the two main pillars, SPO and SMO, the IC has taken an active role in combatting terrorism. Thus far, US policy against terrorism has required the IC to monitor sanctions against terrorist sponsoring countries, to track terrorist movements, to wiretap suspected organizations abroad, and to infiltrate groups to gain advance warnings of attacks. In addition, the IC has shared counterterrorism information, technology, and techniques with foreign governments like Israel as part of its overall coordination efforts. With such broad IC involvement in US counterterrorism policy, a few modest reforms can generate substantial efficiency gains for the IC.
Recommendations
Diversify HUMINT sources to increase the infiltration rate of terrorist groups
The IC in its counterterrorism efforts has recently experienced difficulties with HUMINT (Section 4.2) due to the questionable reliability of sources and the difficulty of recruiting diverse agents for infiltrating terrorist groups. Consistent with the more general examination of HUMINT in Section 4.2, the IC should strengthen the ethnic diversity of its officers and analysts. Greater diversity would facilitate the IC's global presence, and would allow for better, more effective placement of case officers. Efforts to improve the counterterrorism expertise and cultural knowledge of HUMINT officers would also aid in the successful infiltration of terrorist groups when needed.
Improve the relationship between the IC and the FBI
While the IC and law enforcement have various ongoing liaison programs to increase coordination, they continue to experience cooperation problems related to sharing counterterrorism information and sources. Recommendations improving information sharing between the two agencies are detailed in Section 4.3.1, which specifically deals with IC coordination with law enforcement, and Section 3.1.3 below, which focuses on another Tier A threat, Global Organized Crime.
3.0.1 Global Organized Crime and Counternarcotics
In recent years, global organized crime groups have dramatically increased the scope of their activities by taking advantage of many post-Cold War opportunities such as the lowering of economic and political barriers and fragile new governments. They have also increased their international connections to other organized crime groups, their technical sophistication, their participation in drug trafficking, and their ability to affect global political and economic stability.
The IC and law enforcement agencies during the Clinton Administration have worked to create a strong national response to global organized crime. However, just as mentioned in the previous section on counterterrorism (3.1.2), some problems remain in coordinating resources and strategies between IC and law enforcement. Overlapping responsibilities, the lack of a clear hierarchy for coordination, different community missions, and different concerns over risks have led to problems in implementing a coordinated national strategy.
Fortunately, coordination has been improved through efforts such as joint Intelligence-Law Enforcement working groups and the Committee on Transnational Threats of the National Security Council which was recently created under the Intelligence Authorization Act for Fiscal Year 1997 (IAA97). The new Committee is chaired by the Assistant to the President for National Security Affairs, but as Section 4.1 will recommend, the DCI may be a more appropriate chair.
The current system is not "broken." However, the threat itself is growing in terms of its scale and complexity at a faster rate than US efforts to prevent it. Therefore, this section will specifically recommend ways in which the effort against global organized crime can be improved. However, the more general effort to improve IC coordination with law enforcement will be saved for the discussion in Section 4.3.1.
Recommendations:
Include the Secretary of the Treasury in Transnational Threat Committee meetings.
Currently, the Transnational Threat Committee consists of the Assistant to the President for National Security Affairs, the DCI, the Secretary of Defense, and the Secretary of State. However, the Committee should include the Secretary of Treasury when addressing such issues as money laundering, smuggling, and the economic impact of organized crime.
A counterargument to inviting the Secretary of Treasury might be that the Attorney General is already representing law enforcement in the Committee. Nevertheless, there are some situations where the Committee and its national strategy could benefit from a more relevant Treasury perspective. This reasoning is consistent with the recommendation found later in Section 4.3.1 against having the Attorney General as the sole spokesperson for law enforcement.
Remember to look for unique opportunities to leverage against global organized crime.
Because crime networks have vulnerabilities which differ from other transnational threats, an effective global organized strategy may or may not coincide (or even be consistent) with strategies for other threats. Thus, while the main purpose of the Transnational Threats Committee is to find and leverage commonalities among transnational threats (to improve efficiency, coordination, etc.), it should be mindful and vigilant of unique opportunities to fight global organized crime. Indeed, a specific and separate global organized crime strategy might be justified under particular circumstances when a unique global crime vulnerability is discovered.
Create more liaison programs between intelligence and law enforcement specifically dealing with global organized crime.
As mentioned under other transnational Tier A missions, intelligence and law enforcement have used liaison programs to increase personal contacts and to facilitate coordination. Since the benefits of these programs have been significant, the Transnational Threats Committee should encourage their further development in the fight against global organized crime.
The cost of adding these joint projects is relatively small when compared with the benefits of greater intelligence gathering, more successful investigations and prosecutions, and the cost efficiencies gained by sharing resources and technology between the two communities.
Increase the use of HUMINT against global organized crime.
Consistent with the recurring theme requesting more HUMINT throughout this Tier A transnational threat section, further use of HUMINT is needed to deal with global organized crime. Similar to the cases of nuclear proliferating states (3.1.1) and terrorist groups (3.1.2), only human sources can penetrate underground networks and learn about their complexities and vulnerabilities. Expensive satellite imagery, though helpful in collecting information on large military sites, is significantly less effective in collecting information on global organized crime.
The Snyder Commission's HUMINT proposals are further elaborated in
Section 4.1.2.
3.2 Tier B: Medium Priority Missions
Tier B missions are not immediate needs for national security, but instead are developing rather rapidly and could be important in the near future. As this section will discuss, the Tier B missions, economic intelligence and information warfare, have only truly emerged as players during the post-Cold War with the globalization of the world economy and the advent of new telecommunications. However, although they are relatively new, the missions are quite serious, and thus the IC should continue its vigilance over Tier B.
3.2.1 Economic Intelligence
In today's technologically-based and global trade society, national security is increasingly seen more in terms of economic strength and vitality than in terms of pure military capability.(13)
Unfortunately however, threats to US economic well-being abound because the national economy is no longer an isolated entity. In the "global economy," economic troubles abroad can easily have grave effects on domestic markets. For example, the devaluation of the Mexican Peso in late 1994 sent United States financial markets into disarray.
Another area of economic concern is industrial espionage, which along with other forms of economic crime and corruption drain an estimated $260 billion a year out of U.S. based companies.(14)
Right now, 23 countries engage in industrial espionage against American targets.(15)
These countries steal technologies and trade secrets and give them (or sell them) to their own domestic companies, giving these firms a competitive advantage. The three chief offenders are Russia, who according to the Defense Intelligence Agency (DIA) is preparing an economic spying blitz; Japan, who basically stole the United States market share in the microchip industry in the early 1980's; and France, whose aggressive espionage effort has used agents to search the briefcases of US businessmen.(16)
The number of industrial espionage cases currently under investigation is about 800, twice the number in 1994.(17)
The threats posed to the US economy by future worldwide economic shocks and industrial espionage suggest that the IC should expand its economic intelligence capabilities in the post-Cold War era, both on the offensive side and the defensive side.
Recommendations
Develop a more aggressive macro-level economic intelligence capability for offensive purposes.
Clandestinely obtained economic intelligence through HUMINT (Section 4.2) and other special sources can aid policy-makers in negotiating trade agreements.(18)
Also, analysis of both clandestine and open source economic information can help the US identify emerging markets, an important intelligence function that helps policy-makers reduce trade deficits.
Do not change current US policy regarding the IC's use of industrial espionage.
Current US policy forbids the IC from engaging in offensive industrial espionage, and this policy should be maintained. No substantial gain would come about from conducting industrial espionage, since the US already has the most advanced technologies. In addition, such actions would involve serious diplomatic risks, and would only encourage foreign governments to continue stealing American trade secrets.
Counter industrial espionage with counterintelligence and diplomatic efforts.
On the defensive side, the intelligence community (IC) should continue its efforts to improve counterintelligence methods and its ability to alert the FBI to cases of trade secret spying. The recently signed Economic Espionage Act of 1996 is a step in the right direction.
In addition, US policy-makers should also continue their diplomatic efforts to level the economic playing field. One particularly effective method is to publicly expose the unfair bidding practices of foreign firms, which often results in a partial contract award to an American firm.
Change the language of the Economic Espionage Act of 1996.
The Economic Espionage Act of 1996, which for the first time makes trade secret theft punishable by law, is a misnomer, and should be renamed the Industrial Espionage Act. Industrial espionage is the stealing of trade secrets and corporate data practiced by foreign governments. Economic espionage, in contrast, involves the collection of macro-level economic data, and is an established and accepted function of the IC. The blurring of these terms is misleading and should be avoided.
Use open and clandestine economic intelligence sources complementarily.
In its final report, the Brown Commission expressed concern that the IC duplicates economic intelligence which is already available from open sources. To avoid this duplication, the IC should effectively utilize open sources by building relationships with academia and industry. The Civilian Intelligence Reserve Corps recommended in Section 4.3.4 and the increased use of rotational assignments recommended in Section 4.4 would facilitate these relationships.
However, open sources cannot stand alone, and they are not replacements for clandestine intelligence. Clandestine intelligence should continue to serve as a "second engine," confirming and disclaiming information and providing new insights.
3.2.2 Information Warfare
The unbridled growth of information technologies and systems during the past few years has rapidly improved productivity and efficiency in the United States. However, as more information and communication processes become electronic, the nation's infrastructure will become increasingly reliant on these technologies and thus vulnerable to information warfare (IW) attack. As testimony at Senate computer security hearings(19)
shows, the military complex, the Internet, telephone system, power grid, and air traffic control are all potential avenues for rogue actors and hackers to cause widespread havoc. Thus, IC solutions for defending against an IW attack are imperative, since IW poses an immediate incalculable threat to national security. In addition, an examination of offensive information warfare might be instructive, since it could be used as a potent foreign policy tool in the future.
Recommendations
Develop an offensive information warfare capability as a viable foreign policy tool.
The report on the information infrastructure mandated by the Intelligence Authorization Act of 1997 should include an assessment of using information warfare as an offensive measure to achieve foreign policy goals.(20)
Electronically disabling parts of an enemy's infrastructure can be quite effective and coercive, and relative to other covert or military actions, it has the potential ethical advantage of causing little or no loss of innocent human life. In addition, many of the new Tier A transnational threats discussed in Section 3.1 depend on information technologies to function. For example, computer networks allow greater international collusion and organization between drug traffickers and organized crime groups. Disrupting these systems through offensive IW could be a potent weapon against transnational threats.
Like other covert actions, offensive information warfare conducted by the IC would require a proper Presidential finding.
Implement a six part strategy for defending against information warfare.
Due to this country's significant dependence on the national information infrastructure (NII) and the NII's vulnerability to attack, the IC should implement a six part strategy to prepare for an IW attack.
(i) Do not panic about a "Digital Pearl Harbor."
The development of effective defenses against information warfare need not result in the next Manhattan Project. While IW does pose a risk to national security, other risks (such as proliferation) are even more dangerous. Thus, the IC should address IW, but resources should continue to be allocated according to its Tier B position in the PCW framework or in combination to fight Tier A threats.
(ii) Review current encryption laws.
By preventing unauthorized access to information and computer systems, encryption can be an effective and reliable method of self-protection for the private sector against information warfare attacks. If a hacker cannot decipher the data on a computer screen, he cannot crash or steal information from a system. However, current export restrictions hinder the commercial implementation of 'strong' (very secure) encryption schemes. Consequently, only 'weak' encryption has found widespread use, and it can be quickly cracked by a concentrated attack.(21)
The encryption debate has raged on in recent years, but policy-makers have reached a virtual stalemate with Congress demanding a slackening of export controls(22)
and the Clinton Administration firmly opposing it. To end this stalemate, which wastes precious time, the current encryption laws should be reviewed by a joint commission comprised of members from industry, law enforcement, academia, the IC, and other areas of government. To make it far more powerful and influential than the recent National Research Council study,(23)
it should also be bipartisan, and have senior members of Congress and presidential appointees. This commission's task would be to arrive at a compromise for a new national encryption framework, which would raise encryption strengths to secure levels and could be passed into law.
(iii) Prepare for an information warfare attack against the armed forces.
As part of its SMO pillar, the IC must help the military guard against an information warfare attack against US conventional and strategic forces. As a recent Senate hearing showed,(24)
the military is extremely dependent on the national information infrastructure, and thus in accordance with the dynamics of the PCW framework, IW should be moved to Tier A under special circumstances.
(iv) Think about voluntary computer security standards.
Although the private sector holds the responsibility for protecting its own networks, government standards from the National Institute of Standards and Technology (NIST) can help set minimal security objectives and expectations. These standards would provide a rallying point for industry efforts in computer security, and would give direction to future software and hardware development. In addition, they will also increase public and industry awareness of the information warfare threat, leading to safer computing practices.
(v) Provide the computing public with an unclassified version of the NII Threat Assessment Report.
The IC is currently performing an NII Threat Assessment to ascertain vulnerabilities in the infrastructure. Although most of this report will be classified, non-sensitive sections should be released to key industry groups and software developers in accordance with DCI Directive 1/7 (further discussed in Section 4.5). In order to better defend its computer systems, industry must know where its vulnerabilities lie; keeping the information entirely secret aids no one. While specifics should not be released (for fear of telling computer criminals about vulnerabilities), releasing general computer security recommendations could be a first step to implementing this recommendation.
(vi) Continue developing relationships with industry and academia in the computer security field.
The IC should develop ties with industry and academia for two reasons.
First, IC is no longer the most technically advanced organization in some computing areas, especially those which have just recently arisen (World Wide Web, etc.).(25)
Second, even if the IC designed a perfect security apparatus for the computing public, that product needs to be marketed through industry to find widespread use. The Civilian Intelligence Reserve Corps (Section 4.3.3) and the expansion of rotational assignments outside the IC (Section 4.4) can be a vehicle for creating these relationships with industry and academia.
3.3 Tier C: Low Priority Missions
Tier C consists of low priority areas such as environmental intelligence and health and humanitarian-related intelligence. These missions pose no immediate dangers to national security, and can frequently be supported through open-source collection. However, in accordance with the PCW framework, the IC should not neglect Tier C unless high priority missions demand it. Tier C capabilities are worth maintaining because those missions occasionally make significant contributions to the two pillars, SPO and SMO, and other tiers. For example, health intelligence, though normally low-priority, becomes SMO when American soldiers are deployed in humanitarian operations to disease stricken regions of the world.
3.3.1 Environmental Intelligence
In the past, collection and analysis of most environmental data were typically handled by civilian government agencies, nongovernmental organizations (NGOs), and academia. The intelligence community (IC) was only involved in environmental collection related to supporting the military, tracking world-wide natural resource levels, monitoring compliance with environmental accords, and forecasting crop yields.(26)
However, with the end of the Cold War, portions of the IC's technologically advanced and occasionally unused image intelligence (IMINT) capability could be retasked for environmental research. In addition, old and outdated IMINT archives could be declassified to support new non-traditional environmental roles. These new roles for the IC in environmental intelligence include dealing with natural disasters and tracking trends like global warming, ozone depletion, deforestation, and oceanic degradation.(27)
The CIA recently established a Disaster Response Team capable of rapidly disseminating unclassified products to help civilian government agencies monitor natural disasters.(28)
However, the biggest move by the IC towards disseminating environmental intelligence was the establishment of MEDEA, a group of 60-70 academic scientists cleared for access to top secret documents. Its goal was to ascertain how the IC's technical assets and products could be productively used by the scientific community to study environmental problems.(29)
MEDEA found many environmental applications for IMINT technology and products. For example, "changes in vegetative and desert boundaries, which may be sensitive indicators to global climate change, [can] be tracked over time by satellite systems."(30)
Also, the Defense Support System, which is designed to detect the flare-up of intercontinental ballistic missiles (ICBMs) coming out of silos, can be employed to identify outbreaks of forest fires.(31)
While the applications for environmental intelligence abound, previous reform papers (including Hedley, Brown, and the Council on Foreign Relations)(32) emphasize that environmental intelligence is a peripheral issue, and that IC involvement with the environment should be limited. In short, the IC can neither competently nor cost-effectively function as a general information service. Although the IC can help occasionally, environmental researchers must continue to primarily rely on available open source information and await the declassification of government archives. (See Section 4.5)
Recommendations
Although it is important, remember that environmental intelligence is a Tier C mission.
As expressed by the various commissions, environmental intelligence is only a peripheral mission. More immediate concerns like SMO and nuclear nonproliferation clearly take priority and should demand most of the IC's resources. The use of intelligence technologies to "spy on the environment" should be pursued only if it requires no significant expenditures and if the risk of exposing collection techniques is minimal.
Use prudence in declassifying imagery relevant to scientific research.
Because of the risk of revealing IMINT capabilities and techniques, wholesale declassification of CIA's entire IMINT archives is undesirable. However, older images, which pose a minimal possibility of disclosing current technologies and techniques, are still useful to scientists and should be declassified. Executive Order #12951 provides for the release of images from 1960-1972(33)
and is a good start.
More recent imagery can be declassified by repackaging them in unclassified form.(34)
For example, the IC might omit the exact location of a satellite image or the time at which it was taken, or the IC might even blur the image. These omissions or alterations will diminish the scientific research value of the data, but at least some of the data will be used for scientific research. Section 4.5 discusses the "repackaging" of IMINT for declassification in greater detail.
Encourage joint ventures in environmental intelligence to reduce costs.
Domestically, Congress should encourage joint ventures between the IC and civilian agencies like the ones established in the Oceanographic Community. These programs can be facilitated by earmarking a certain portion of agency budgets specifically for joint ventures.
International projects should also be encouraged to reduce costs for the US in producing intelligence that also benefits other nations.
Do not formalize the tasking relationship between the IC and environmental intelligence consumers.
Consistent with the Tier C classification of environmental intelligence, the current informal process by which an agency like the Federal Emergency Management Administration (FEMA) requests intelligence products and assistance from the IC should not be formalized. If the IC is able to comply with a request for environmental intelligence, it has the responsibility to do so. However, if compliance were formalized and mandatory, the number of requests would probably rise, and the IC's human and financial resources would be diverted from higher priority goals. Besides, FEMA is currently quite satisfied with the status quo arrangement.
3.3.2 Health and Humanitarian-related Intelligence
In the post-Cold War era, four major health and humanitarian fields have become significant concerns for the IC. These potential problem areas, biological warfare, VIP health, regional instability, and humanitarian operations, affect US foreign policy and national security, warranting IC involvement:
1) Biological Warfare (BW): Although the global threat posed by weapons bearing fatal disease agents is not new, the rise of rogue states and terrorist groups has made BW a serious and immediate concern in the post-Cold War world. In fact, this concern can be referenced as a Tier A threat to nonproliferation efforts found in Section 3.1.1.
2) VIP Health: The health, or ill-health, of international leaders can drastically affect summits, negotiations, and foreign political and military stability. VIP health monitoring provides ongoing support to the SPO and SMO pillars, and can help the US predict and prepare for future events.
3) Regional Stability: Infectious disease epidemics and poor health abroad can lead to situations inimical to US interests: unstable populations, large-scale mobility, civil disorder, and war.
4) Humanitarian Operations: According to the US Training and Document Command, 68% of military operations from 1989-1993, involved humanitarian, peacekeeping, evacuation, and disaster relief. Humanitarian emergencies often require intelligence on the exact nature (location, extent, type, likelihood, and severity) of need, usually based on the analysis of maps, charts, and photographs. Policy-makers and relief operators have often specifically criticized IC deficiencies in this area, and some have even suggested establishing a Humanitarian Assistance Intelligence Center.(35)
Many non-IC organizations currently address these health and humanitarian issues: the Centers for Disease Control (CDC) monitors the spread of infectious disease; the United Nations (UN) facilitates humanitarian assistance efforts, and the World Health Organization (WHO) monitors global health and regional stability. However, these organizations are too global in scope to assist US policy-makers, who often need specific pieces of information to make decisions. The IC is well-positioned to specifically monitor and analyze the effects of disease or humanitarian emergencies on US foreign policy. In addition, it can validate incoming health and humanitarian information from international agencies.
Recommendations
Give health and humanitarian related intelligence missions a definite priority.
So far, reform efforts and legislation have failed to definitively mention the scope or priority of health and humanitarian intelligence, leaving the field with little direction. This area of intelligence should be explicitly defined and prioritized in future bills or directives.
Although health and humanitarian relief operations should remain at Tier C, below higher priority threats like counterterrorism and nonproliferation, the IC should neither neglect nor ignore them. Intelligence for health issues and humanitarian efforts clearly serves both pillars, SPO and SMO, making it an important mission.
Develop relationships with civilian international organizations, NGOs, and academia operating in the health and humanitarian arena.
Health and humanitarian intelligence offers a valuable opportunity for cooperative efforts with NGOs, academia, and other organizations like the CDC, UN, and the National Science Foundation (NSF). Sharing information and capabilities with these groups might help defray costs for all parties. The IC would receive information from these groups to meet its needs, while sharing some of its own capabilities to support their efforts.
The IC could use the Civilian Intelligence Reserve Corps program discussed in Section 4.3.4 to develop these relationships. In addition, to accomplish these collaborative efforts, reports regarding global health threats and relief efforts would have to be available in an unclassified form suitable for dissemination. As will be mentioned in Section 4.5, maintaining an appendix for classified information would allow for efficient extraction of unclassified material.
One significant obstacle to meaningful coordination may be a distrust between the outside health organizations and the IC. This obstacle might be overcome through careful bureaucratic arrangements early on and later through the establishment of personal and informal contacts.
Create a Health Intelligence Task Force within the Office of Transnational Security and Technology Issues at CIA.
Within the Office of Transnational Security and Technology Issues (TSTI) at CIA, a small task force should be created composed of analysts whose sole concerns are health-related issues. These issues would include the effects of global disease patterns on US interests, VIP health, and the effects of health-related problems (such as food, medical care, & water supply) on population stability.
Such a task force should collect and analyze the volumes of health-related intelligence arising from the collaborative efforts with outside organizations outlined in the previous recommendation. It should then disseminate it to the appropriate geographic analytical centers within the Directorate of Intelligence (DI).
Use the Armed Forces Medical Intelligence Center to identify health threats to US forces and government-sponsored relief efforts.
The Armed Forces Medical Intelligence Center (AFMIC) within the Defense Intelligence Agency (DIA) should continue to pursue its mission to identify medical and health threats to US military forces, a recommendation which supports the IC's SMO pillar. However, this mission should be further extended to include US government-sponsored humanitarian workers (military or civilian). Towards this goal, AFMIC officers have recently welcomed collaborative efforts with the National Military Intelligence Production Center (NMIPC) to produce comprehensive intelligence for humanitarian and relief operations.(36)
7. House of Representatives, 104th Congress, National Defense Authorization Act for Fiscal Year 1997, H.R. 3230, Public Law 104-201, September 23, 1996, p. 821.
8. Zachary Davis, International Nuclear Policy Expert at the Congressional Research Service, Former Nuclear Policy Advisor to Senator Sam Nunn, interviewed by Jeff Siegel, Washington DC, January 2, 1997.
9. Gary Samore, Special Assistant to the President and Senior Director for Nonproliferation and Export Controls, The White House, interviewed by Jeff Siegel, Washington DC, January 2, 1997.
10. Ibid.
11. Frank von Hippel, "Working in the White House on Nuclear Proliferation and Arms Control: A Personal Report," Journal of the Federation of American Scientists, Vol. 48, No. 2, March/April 1995, pp. 7-8.
12. US Congress, "Conference Report," Intelligence Authorization Act for Fiscal Year 1997, 104th Congress, 2nd Session, September 14, 1996, p. 11.
13. William T. Warner, "International Technology Transfer and Economic Espionage," International Journal of Intelligence and Counterintelligence, Volume 7, No. 2, Summer 1994, p. 155.
14. Sam Perry, "Economic Espionage: The Corporate Threat," found at http://emporium.turnpike.net/%EIntInt/econ.html, p. 1.
15. John J. Fialka, "Stealing the Spark: Why Economic Espionage Works in America," Washington Quarterly Vol. 19, No. 4, Fall 1996, p. 178.
16. Bill Gertz, "Russians Spy on U.S. Business Using Listening Post in Cuba," The Washington Times, October 7, 1996.
Garth Hancock "U.S. Economic Intelligence Policy and Global Competition, Monterey Review Vol XVI. (Spring 1996), found at http://www.miis.edu/mreview/spring96/hancockart, p.12.
Peter Schweizer, Friendly Spies: How America's Allies Are Using Economic Espionage to Steal Our Secrets. New York: The Atlantic Monthly Press, 1993, p. 99.
17. Fialka, pp. 178-179.
18. Samuel D. Porteus, "Looking Out for Economic Interests: An Increased Role for Intelligence," Washington Quarterly Vol 19, No. 4 (Fall 1996), p. 192.
19. Senate Permanent Committee on Governmental Affairs, Subcommittee on Investigations, Hearings on Computer Security, 104th Congress, June/July 1996.
20. US Congress, Intelligence Authorization Act for Fiscal year 1997, Title III, Sec. 310.
21. Matt Blaze, et al., "Minimal Key Lengths for Symmetric Ciphers to Provide Adequate Commercial Security," Business Software Alliance, January 1996.
22. United States Senate, 104th Congress, S. 1726: Promotion of Commerce On-Line in the Digital Era (Pro-CODE) Act of 1996.
23. Elizabeth Corcoran, "Easing of Encryption Technology Curbs Backed," Washington Post, May 31, 1996.
24. Eric Sterner, "Digital Pearl Harbor: National Security in the Information Age," National Security Studies Quarterly, Washington DC, Georgetown School of Foreign Service, Summer 1996. Over 95% of military communication uses the NII.
25. For example, the IC could develop a working relationship with the Princeton University Internet Security Group, which has found a number of major security flaws on the World Wide Web.
26. John Deutch, DCI Speech at the World Affairs Council in Los Angeles, "The Environment on the Intelligence Agenda," July 25, 1996.
27. Ibid.
28 Ibid.
29. Ibid.
30. Robert Dreyfuss, "Spying on the Environment," ISSN:1046-8021, Vol. 6, No.1, p. 28, (Earth Action Network Inc., February 1995).
31. Ibid.
32. John Hedley, Checklist for the Future of Intelligence; Aspin-Brown Commission, Preparing for the 21st Century: An Appraisal of US Intelligence; Council on Foreign Relations, Making Intelligence Smarter.
33. Kevin C. Ruffner, "Declassification's Great Leap Forward: CORONA and the Intelligence Community," http://www.npr.gov/NPR/Reports/intel.html.
34. Ibid.
35. G. Ted Constantine, Intelligence Support to Humanitarian-Disaster Relief Operations: An Intelligence Monograph, Center for the Study of Intelligence, Central Intelligence Agency, December 1995, p.15.
36.
Ibid., p.12