Weapon Systems Intelligence Integration (WSII) Handbook; June 1999
Chapter 7.
Intelligence Requirements Development
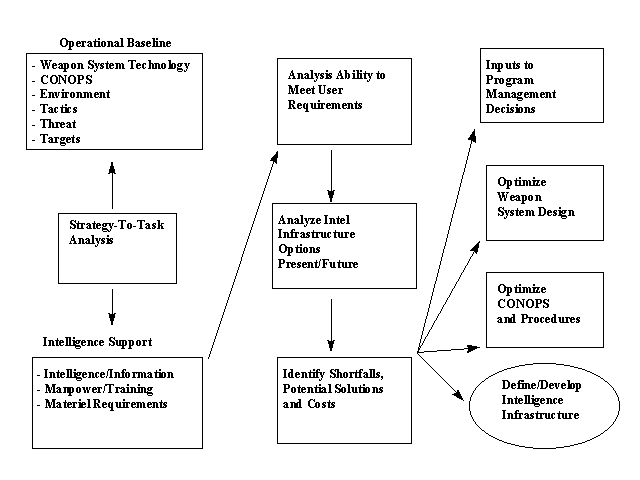
Once the Operational Requirements of a weapon system have been clearly defined, the intelligence requirements can then be derived and developed. Intelligence Support Requirements (ISRs) are derived from the operational baseline using the strategy-to-task methodology. The ISRs are then further developed using functional area checklists. Once the intelligence requirements have been developed in detail, the WSIIO can analyze the intelligence community’s ability to meet the new weapon system’s identified requirements. As depicted in the figure below, these shortfalls can be addressed by optimizing resources, revising the CONOPs, or potentially optimizing the weapon system design.

Figure 7.1 -- ISR Development
7.1. Operational Baselines/Operational Concepts. The operational baseline for a weapon system includes the combined technology, targets, tactics, concepts of operations, environment, employment options, and threats to the weapon system. Operational factors are those related concerns warfighters must consider as they evaluate, plan, and conduct a mission. While numerous and varied, they are generally derived from the techniques and timelines associated with the application of force. They may involve type of target, probability of kill, turn-around time, threat environment, self-protection needs, aircraft performance characteristics, weapon systems, communications and coordination requirements, terrain, weather, and countless other operations-oriented considerations. Operational imperatives are further refinements of the operational baseline (and related operational factors) and serve as a starting point for subsequent operations/intelligence infrastructure analysis. Deriving operational imperatives from the operational baseline provides a greater focus on the user’s specific intelligence requirements. Expressed in terms of accuracy, precision, timeliness, interoperability, and data formats, these operational imperatives define the basic characteristics of the intelligence support required to make a weapon system effective.
7.2. Strategy-to-Task (STT) Methodology. STT is a methodology for requirements analysis that is used by both MAJCOMs as they determine Mission Needs, as well as the ISWG as they derive intelligence support requirements. STT is one tool that enables analysts to derive and trace linkages from high-level military objectives down through individual tasks and the resources that support them. Two components of the STT analysis include a top-down (vertical) component, and an end-to-end (horizontal) component.
7.2.1. STT’s Vertical Component. The vertical component can be a high level STT, used to establish or develop a mission need statement; or a task/sub-task STT, used to develop a concept of operation (CONOP) or high level intelligence requirements. In Figure 7.2 below, STT was used to show links between Mission Areas and National Strategy/Policy. In Figure 7.3, STT was used to tie operational tasks back to the Overall Mission.
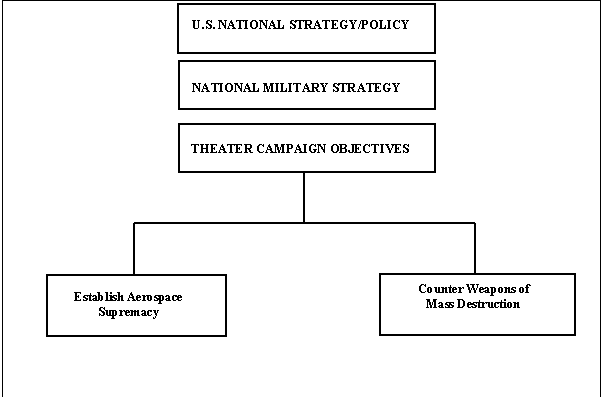
Figure 7.2 -- High-level STT framework
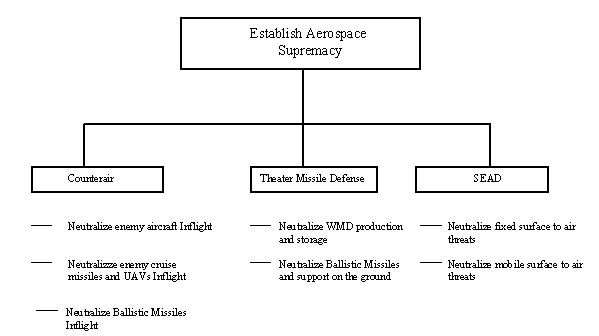
Figure 7.3 -- Task/Sub-task framework
7.2.2 STT’s Horizontal Component. The end-to-end (horizontal) component of STT can be considered system oriented, and is a useful tool to derive intelligence requirements for a particular weapon system. Often depicted graphically or in tables, STT shows a framework that may depict operational goals, system relationships, and requirements at several levels. In the context of the ISP, STT is the term used to describe the horizontal component (weapon-system specific) requirements generation process. Simply put, the Horizontal STT component is the analysis behind getting from Chapter 2 (Operational Considerations) to Chapter 3 (Derived Intelligence Requirements). Often, the most challenging aspect of STT is determining how to best depict the operational considerations. Two approaches to the horizontal STT are explained below.
7.2.2.1. "Weapon System" Centric. This is a systems engineering analysis approach to determining the operational considerations and intelligence requirements which result. This approach involves analyzing the functions you want the system to accomplish, the data and information needed to feed the system (input), the products, data or information output from the system, the customers of the output, as well as the interfaces to other systems. The analysis can then be applied for each mission/role and operational task that the system is expected to perform. Using this approach, the Intelligence support solutions can be described using nodal analysis. Weapon systems that are good candidates for this kind of analysis are surveillance and info/intel providers (i.e., AFMSS, UAVs, SBIRS).
7.2.2.2. Employment Centric. The second approach to the horizontal STT includes tracing the weapon systems’ operational "to-do’s" through all phases of employment
• Pre-deployment
• Deployment
• Employment
• Sustainment
• Re-deployment
These "to-do’s" can be developed by examining the weapon system’s "roles and missions" cycle. The JDAM STT, for example, used a combination of the force applications and targeting cycle. This provided a strawman that could be "filled-in" using the CONOP. Weapon systems that are good candidates for this kind of analysis are aircraft (fighters/bombers), precision guided munitions, and missiles. In any case, regardless of the approach used, STT should be validated with operators before presenting it to the ISWG for review.
7.2.3. Picking an approach to the STT. The following questions can help you determine the best approach and get the WSIIO started on a sound STT analysis.
• Does my system have an employment cycle?
• How is my system tasked?
• What associated systems are also tasked?
• What is this system supposed to do?
• Where/How will it be employed?
• How does my system operate?
• What is a typical day/mission?
• What are the system "volumetrics?"
• How many weapon systems are being purchased?
• How many will be employed (and therefore need to be supported) under different employment scenarios (e.g., wartime, contingency, peacekeeping ops)
7.3. Defining the Operational Baseline. Ideally, the operational baseline for a weapon system would be clearly outlined for the WSIIO. Realistically, the WSIIOs are left to propose a strawman for the ops community and ISWG to review. The operational baseline will flow from the following questions. If no formal written CONOPs is available, answering these questions will provide the WSIIO with a starting point for the operational consideration (left hand side of the strategy to task analysis).
• What operational steps must be taken in the use of this system through all phases of employment? From pre-wartime planning through employment and re-deployment?
• How will the system be designed? Does the technology used drive specific support requirements. What information to weapon system developers need to optimize their weapon system design? What data (based upon the design) does the weapon system need to meet the operational requirements?
• How will the system be employed? In what environments, under what conditions?
7.4 Key Sources for Answers.
|
Functional Area Experts |
Weapon System Developers |
|
ORD |
Program/Design Reviews |
|
SAMP |
STAR/TED |
|
TEMP |
AoA Studies and Analyses |
|
CONOPs |
7.5. Deriving the ISRs. Once you have identified the operational baseline, the ISWG or WSIIO can begin to determine whether each of those factors described above drives any intelligence support requirement. Asking your operational counterparts the question "do you need intelligence or information to do that?", will lead you to identifying what is needed at a macro level. An example of this analysis is represented in Table 8-1 below.
|
Mission Execution: |
||||
|
Function includes final mission preparation, mission flying, target "acquisition," attacking with JDAM, and returning delivery aircraft to base. (The ISR column is the Intel Requirement location in Chap 3) |
||||
|
Operational Consideration |
Intelligence Requirement |
ISR |
||
|
? |
Load mission planning data via |
|
|
|
|
? |
Confirm Mission |
|
|
|
|
? |
Download GPS data to weapon |
|
|
|
|
? |
Fly mission |
? |
Provide Indications and Warning |
|
|
? |
Receive flex targeting update |
? |
Provide target coordinate updates |
MP-P1-0100 |
|
? |
Derive target coordinates from on-board sensors or third party |
? |
Provide third party coordinates |
OP-P1-0100 |
|
? |
Release weapons |
? |
Process in-flight report (INFLTRP) |
OP-P1-0102 |
|
|
? |
Collect combat assessment data |
|
|
|
? |
Recover aircraft |
|
|
|
Table 7-1 -- STT Functions and Intelligence Subtasks
7.6. Developing ISRs. Further analysis of each ISR against the existing and planned infrastructure will determine whether or not they are potential shortfalls to weapon system supportability. The following guidelines apply to conducting this assessment and ISRs are split into two groups: Category 1 ISRs and Category 2 ISRs. All Category 2 ISRs can then be further defined (developed) using the functional area checklists.
Category 1 -- The requirement can be satisfied by today’s intelligence infrastructure with no changes to existing systems, processes, and/or procedures; i.e., the required information, product, or data exist today. Category 1 requirements are not ordinarily documented in Chapter 3 of the ISP since they do not represent a potential shortfall with a weapon system’s supportability. In the context of intelligence support plan (ISP), category 1 requirements may or may not have a validated production requirement in place. Where applicable, these category 1 requirements should be assessed to determine if a production requirement (PR) is needed.
Category 2 -- The requirement cannot be satisfied by today’s intelligence infrastructure without changes to existing systems, processes, procedures, or major capability upgrades. These are identified in the far right column of Table 8-1 as having an ISR shortfall. The listed code identifies where the ISR is discussed in Chapter 3 of the ISP.
7.7. Functional Area Checklists. This section contains a consolidated series of checklists to help you conduct a systematic, comprehensive, and standardized assessment of intelligence support requirements for a weapon system. These checklists will help you fully, completely, and thoroughly describe all the criteria that make up a requirement. This information is used to determine the satisfaction criteria and associated elements of satisfaction that describe the ISRs in Chapter 3. The material in these consolidated checklists cover eleven subject areas:
• Imagery Intelligence (IMINT)
• Signals Intelligence (SIGINT)
• Human Source Intelligence (HUMINT)
• Scientific and Technical Intelligence (S&TI)
• Measurement and Signature Intelligence (MASINT)
• Geospatial Information and Services (GI&S)
• Airborne Reconnaissance
• Intelligence Data Handling Systems (IDHS)
• Manpower and Training
• General Military Intelligence (GMI) Production
• Development and Intelligence Infrastructure Issues
While these checklists are quite comprehensive, they will not cover all the questions you need to ask; neither are they properly tailored to meet the unique aspects of each specific weapon system program. They should provide a solid starting point, however, as you begin to further develop the intelligence support requirements.
7.7.1. The Checklist Format. To permit maximum commonality and integration of these checklists, a standard format has been followed to the fullest extent possible. This is particularly true for the IMINT, SIGINT, HUMINT, S&TI, MASINT, and GI&S areas; the detailed explanations of specific items below apply primarily to these checklists. However, you will also find a good degree of commonality in the airborne reconnaissance, intelligence data handling systems, and manpower and training questions. Essentially, two basic sets of issues are included in each checklist:
7.7.1.1. The first set of issues helps answer questions related to what specific kinds of intelligence support will be required throughout the life cycle of the weapon system. Your task is to work with appropriate functional managers and use each checklist in this chapter to ensure a structured, rigorous, comprehensive assessment of the intelligence requirements of each weapon system, based on the system’s operational imperatives.
Items 1 and 2 are designed to ensure a common definition of basic requirements and identification of the primary customers, whether they be involved in acquisition, support, testing, or training activities related to the weapon system.
Item 1 is straightforward: Is a particular type of intelligence information, product, or support required? To answer this question, however, you must begin with a hard look at the operational imperatives for the weapon system, followed by discussions with operators, acquisition personnel, and intelligence managers.
Item 2 helps you focus immediately on the bottom line: Who is your customer? Answer this question not only in relation to the particular end user(s); also keep in mind intermediate recipients who must process and distribute the intelligence, as well as the automated tools and communications systems that will eventually receive this intelligence. You must answer this question precisely if you are to properly respond to the questions that follow.
Items 3 through 18 outline specific components of the support to be provided. These questions will appear to be overlapping and redundant at times, but they are designed to force you to look at intelligence requirements from varying perspectives. They will also help you focus on the operational imperatives for the weapon system, and add rigor and structure to your discussions with operations and acquisition counterparts and fellow WSIIOs.
Item 3 requires that you define the subcategories within a particular intelligence functional area. You must describe exactly what type of intelligence is needed, and what is not needed. The latter information is as important as the former, because it will save much wasted effort and expense, and it will force all concerned to think hard about what is really required.
Item 4 addresses essential elements of information. What substantive information is required for the weapon system to be successful? What specific targets, areas, activities must be known? The answers will vary according to the CONOPs and the particular theater and enemy, among other variables.
Item 5 identifies specific geolocation accuracy requirements, including both coordinates and elevation. This requirement may be described in terms of feet, meters, degrees, etc. There may be different sets of accuracy requirements for a given weapon system, depending upon the CONOPs. For example, the aircrew on an aircraft firing laser-guided munitions may need target location accuracy within a several meters; the same crew launching cruise missiles with terminal homing capabilities will not have such stringent target geolocational accuracy requirements.
Item 6 gives you an opportunity to define the exact level of detail required. For IMINT and target materials, it might be the resolution and scale of the image; for MASINT, specific parametric information needs can be identified in this section.
Item 7 applies only to imagery and graphic products and provides the opportunity to define the size of the area to be covered in each product. For example, the requirement may be for coverage of point targets only; alternatively, the requirement may be for a series of images, from broad area coverage down to weapon aim points at a particular installation.
Item 8, age. What is the acceptable elapsed time since the item of interest was last noted or assessed by intelligence?
Item 9, timeliness. What is the acceptable elapsed time from user identification of need for the information, to delivery of the data or product to the customer? Also, what is the latest time the data or product is useful?
Item 10, security classification restrictions. What is the preferred classification level for the intelligence? This may vary according to the particular mission; for example, coalition operations may generate demands for a lower classification or dual sets of data. There will be instances when this issue will lead you to an analysis of possible tradeoffs on security issues. Identify them early, because resolution of such questions can take a considerable period of time and have a major impact on construction of databases, facilities, etc.
Item 11, format. What is the acceptable format and manner in which the intelligence must be provided to the user? The same information may have to be provided in a number of different formats to meet the needs of different users. You will have to balance individual user preferences with the cost and difficulty associated with multiple formats.
Item 12, database structure. What are the data elements required? Is the data dictionary known and acceptable to all concerned? Is the database management system agreed upon, feasible, and cost-effective?
Items 13, 14, 15, 16, and 17. These items relate to imagery and GI&S products and information. They will help you define hard-copy and soft-copy imagery requirements, seasonal coverage needs, and in what instances non-imagery graphics and imagery-derived reporting will suffice.
Item 18. This item relates to airborne recce operational issues that will help the WSIIO identify solutions more easily.
7.7.1.2. The second set of issues relates to how the intelligence community infrastructure will provide the intelligence support required. Essentially, answering the questions in this category will help you conduct the analytical tasks described in the bottom half of Figure 3-2. You will note that there are basically ten lines available for each aspect of the intelligence cycle. This will allow you to be very specific and cover various scenarios if necessary. For example, logistical factors may dictate that a number of these functions be performed differently in different regions of the world, or in the early versus late stages of deployment to an overseas location.
Items 20 through 29 allow you to address requirements management. How will user requirements be articulated, received, recorded, tasked, and monitored for satisfaction? What is the feed-back loop for status updates to the requester?
Items 30 through 39 address collection issues and resources. What INTs and sensors are required to collect the information required? What platforms are capable/available to ensure coverage of the target area? You will need to address survivability and classification issues, as well as the ability of selected sensor suites to provide timely data links or broadcasts to key customers.
Items 40 through 49 address processing issues and resources. How much on-board processing will occur? Where will processing be accomplished? What correlation and fusion is required prior to analysis and dissemination? How will processing affect the format of the data and its suitability for entry into selected databases?
Items 50 through 59 address analysis issues and resources. Is raw data or analyzed intelligence needed? Where will the analysis occur? What are the required outcomes of the analysis?
Items 60 through 69 address production issues and resources. What types of product(s) are most useful to the users? How much production is required? Where will the production occur?
Items 70 through 79 address dissemination issues and resources. What are the timeliness requirements and how can they be met? Which products can be delivered electronically, and which must be sent by land, sea, air? What data link and broadcast options are available?
Items 80 through 89 address application issues and resources. What intelligence will be used directly by the operator? What intelligence will be interpreted and applied by intelligence specialists at operational units before being provided to the aircrew. What tools are available to help both groups apply the intelligence provided?
7.7.2. As a result of this checklist commonality, you and your counterparts can conduct a series of cross-requirements analyses to obtain a consolidated view of specific intelligence infrastructure requirements. For example, it is possible to assess the full range of accuracy requirements for a specific weapon system by calling up Item 5 from each checklist. Similarly, if you need to fully understand classification requirements and restrictions, you can call up Item 10 from each checklist.
7.7.3. The other advantage of this cross-referencing capability is that it allows you to get a consolidated view of bottom-line issues related to intelligence resources. For example, you can quickly summarize intelligence dissemination requirements and resource issues related to a specific weapon system or a number of weapon systems. This will help you articulate the need for additional intelligence dissemination resources, or prioritize or assign existing resources and capabilities to tasks identified by other portions of these checklists.
7.7.4. The eleven checklists follow, each beginning on a new page. Remember that your task as a WSIIO is to work with appropriate functional managers and use each checklist provided to ensure a structured, rigorous, comprehensive assessment of the intelligence requirements of your weapon system. Air Staff functional managers can help you contact National Agency functional managers, if required, or work issues with National issues on your behalf. Your assessment will be based largely on the operational imperatives of the system.
Functional Area Checklist #1
For
Imagery Intelligence (IMINT)
|
I.1 |
Is imagery required? |
|
I.2 |
Who is the customer and where is the intelligence to be delivered? |
|
I.3 |
Type of imagery required (Optical, RADAR, IR, MSI) |
|
I.4 |
Essential Elements of Information: What specific information must be derived from the imagery? |
|
I.5 |
Accuracy: coordinates and elevation (feet, meters, seconds) |
|
I.6 |
Resolution (inches, feet, meters.) |
|
I.7 |
Area size: point targets, area coverage, LOCs. |
|
I.8 |
Age: How recent must the imagery be or what amount of change can be accommodated (i.e., bomb damage)? |
|
I.9 |
Timeliness: What is the latest time the imagery will be useful? |
|
I.10 |
What are the security classification restrictions? |
|
I.11 |
Are primary (raw) or secondary (annotated) images required? |
|
I.12 |
What databases will be used to store and retrieve the IMINT? |
|
I.13 |
Hard copy: size of print, DP, ON, annotations. |
|
I.14 |
Soft copy: magnetic tape, optical disk, NITF, BIT level. |
|
I.15 |
Is seasonal coverage required? |
|
I.16 |
Will detailed, non-imagery graphics suffice? |
|
I.17 |
Will imagery reports suffice? |
|
I.18 |
Will imagery support data be required? |
|
I.20 |
Intelligence infrastructure: IMINT requirements management |
|
I.30 |
Intelligence infrastructure: IMINT collection requirements |
|
I.40 |
Intelligence infrastructure: IMINT processing requirements |
|
I.50 |
Intelligence infrastructure: IMINT analysis requirements |
|
I.60 |
Intelligence infrastructure: IMINT production requirements |
|
I.70 |
Intelligence infrastructure: IMINT dissemination requirements |
|
I.80 |
Intelligence infrastructure: IMINT application requirements |
Functional Area Checklist #2
For
Signals Intelligence (SIGINT)
|
S.1 |
Is SIGINT required? |
|
S.2 |
Who is the customer and where is the intelligence to be delivered? |
|
S.3 |
Type (COMINT, ELINT, PROFORMA) |
|
S.4 |
Essential Elements of Information: What specific information must be derived from SIGINT? |
|
S.5 |
Accuracy: How precisely must SIGINT sensors geolocate electromagnetic emissions for situational awareness and targeting purposes? |
|
S.6 |
Level of detail: For example, is certain SIGINT reporting required on enemy activity down to regiment, squadron, or flight level? What level of parametric detail is needed on selected radars? |
|
S.8 |
Age: How recent must the SIGINT information be? |
|
S.9 |
Timeliness: What is the latest time the SIGINT will be useful? |
|
S.10 |
What are the security classification restrictions? |
|
S.11 |
What reporting format is desired? |
|
S.12 |
What databases will be used to store and retrieve the SIGINT? |
|
S.20 |
Intelligence infrastructure: SIGINT requirements management |
|
S.30 |
Intelligence infrastructure: SIGINT collection requirements |
|
S.40 |
Intelligence infrastructure: SIGINT processing requirements |
|
S.50 |
Intelligence infrastructure: SIGINT analysis requirements |
|
S.60 |
Intelligence infrastructure: SIGINT production requirements |
|
S.70 |
Intelligence infrastructure: SIGINT dissemination requirements |
|
S.80 |
Intelligence infrastructure: SIGINT application requirements |
Functional Area Checklist #3
For
Human Source Intelligence (HUMINT)
|
H.1 |
Is HUMINT required? |
|
|
H.2 |
Who is the customer and where is the intelligence to be delivered? |
|
|
H.4 |
What are the Essential Elements of Information?: |
|
|
• |
Enemy intentions, plans, and doctrine |
|
|
H.6 |
What level of detail is required? |
|
|
H.8 |
Age of information: How recent must the information be? |
|
|
H.9 |
Timeliness: When is the latest time the information will be useful? |
|
|
H.10 |
What are the security classification restrictions? |
|
|
H.11 |
What reporting format is desired? |
|
|
H.12 |
What databases will be used to store and retrieve the HUMINT? |
|
|
H.20 |
Intelligence infrastructure: HUMINT requirements management |
|
|
H.30 |
Intelligence infrastructure: HUMINT collection requirements |
|
|
H.40 |
Intelligence infrastructure: HUMINT processing requirements |
|
|
H.50 |
Intelligence infrastructure: HUMINT analysis requirements |
|
|
H.60 |
Intelligence infrastructure: HUMINT production requirements |
|
|
H.70 |
Intelligence infrastructure: HUMINT dissemination requirements |
|
|
H.80 |
Intelligence infrastructure: HUMINT application requirements |
|
Functional Area Checklist #4
For
Scientific And Technical Intelligence (S&TI)
|
ST.1 |
Is S&TI required? |
|
ST.2 |
Who is the customer and where is the intelligence to be delivered? |
|
ST.4 |
Essential Elements of Information: What specific knowledge must be derived from S&TI? |
|
ST.6 |
Level of detail: What precision is required for various EEIs? Some technical decisions to be made by your operations and acquisition counterparts demand greater detail about enemy technology than others. Make sure you understand the difference. |
|
ST.8 |
Age of information: How recent must the data be? |
|
ST.9 |
Timeliness: When is the latest time the information will be useful? |
|
ST.10 |
What are the security classification restrictions? |
|
ST.11 |
What reporting format is desired? |
|
ST.12 |
What databases will be used to store and retrieve this information? |
|
ST.20 |
Intelligence infrastructure: S&TI requirements management |
|
ST.30 |
Intelligence infrastructure: S&TI collection requirements |
|
ST.40 |
Intelligence infrastructure: S&TI processing requirements |
|
ST.50 |
Intelligence infrastructure: S&TI analysis requirements |
|
ST.60 |
Intelligence infrastructure: S&TI production requirements |
|
ST.70 |
Intelligence infrastructure: S&TI dissemination requirements |
|
ST.80 |
Intelligence infrastructure: S&TI application requirements |
Functional Area Checklist #5
For
Measurement And Signature Intelligence (Masint)
|
M.1 |
Is MASINT required? |
|
|
M.2 |
Who is the customer and where is the intelligence to be delivered? |
|
|
M.3 |
Type |
|
|
• |
Acoustic: ACOUSTINT, ACINT, SEISMIC |
|
|
• |
Electro-optical: IRINT, OPTINT |
|
|
• |
RADAR Intelligence |
|
|
• |
RF/EMP Intelligence |
|
|
• |
Effluent/debris collection |
|
|
• |
Laser Intelligence (LASINT) |
|
|
• |
Nuclear Intelligence (NUCINT) |
|
|
• |
Unintentional Radiation Intelligence (RINT) |
|
|
M.4 |
Essential Elements of Information: What measurements/signatures of enemy systems are required? |
|
|
M.5 |
What level of accuracy is required? |
|
|
M.6 |
Level of Detail: What are the specific parameter requirements needed to support the weapon system navigation and targeting systems, and to help the weapon system survive enemy defenses? |
|
|
M.8 |
Age: How recent must the information be or how much change can be accommodated (i.e., bomb damage)?? |
|
|
M.9 |
Timeliness: When is the latest time the information will be useful? |
|
|
M.10 |
What are the security classification restrictions? |
|
|
M.11 |
What reporting format is desired? |
|
|
M.12 |
What databases will be used to store and retrieve this information? |
|
|
M.20 |
Intelligence infrastructure: MASINT requirements management |
|
|
M.30 |
Intelligence infrastructure: MASINT collection requirements |
|
|
M.40 |
Intelligence infrastructure: MASINT processing requirements |
|
|
M.50 |
Intelligence infrastructure: MASINT analysis requirements |
|
|
M.60 |
Intelligence infrastructure: MASINT production requirements |
|
|
M.70 |
Intelligence infrastructure: MASINT dissemination requirements |
|
|
M.80 |
Intelligence infrastructure: MASINT application requirements |
|
Functional Area Checklist #6
For
Geospatial Information And Services/Target Materials
|
MT.1 |
Are GI&S and/or target materials required? |
|
MT.2 |
Who is the customer and where is the intelligence to be delivered? |
|
MT.3 |
What types of materials are required? |
|
MT.4 |
Essential elements of information (EEIs): What specific information must be derived from the GI&S data? |
|
MT.5 |
What are the accuracy requirements? |
|
MT.6 |
What level of detail (scale, etc.) is required? |
|
MT.7 |
Are there area coverage requirements? |
|
MT.8 |
Age: How recent must the data be or what amount of change can be accommodated (i.e., bomb damage)? |
|
MT.9 |
Timeliness: When is the latest time these data will be useful? |
|
MT.10 |
What are the security classification restrictions? |
|
MT.11 |
What reporting/product formats are desired? |
|
MT.12 |
What databases will be used to store and retrieve this information? |
|
MT.13 |
Hard copy: number and size of prints, annotations |
|
MT.14 |
Soft copy: magnetic tape, opt disk, NITF, BIT level |
|
MT.15 |
Is seasonal coverage required? |
|
MT.16 |
Will detailed, non-imagery graphics suffice? |
|
MT.17 |
Will imagery reports suffice in some instances? |
|
MT.20 |
Intelligence infrastructure: GI&S/TM requirements management |
|
MT.30 |
Intelligence infrastructure: GI&S/TM collection requirements |
|
MT.40 |
Intelligence infrastructure: GI&S/TM processing requirements |
|
MT.50 |
Intelligence infrastructure: GI&S/TM analysis requirements |
|
MT.60 |
Intelligence infrastructure: GI&S/TM production requirements |
|
MT.70 |
Intelligence infrastructure: GI&S/TM dissemination requirements |
|
MT.80 |
Intelligence infrastructure: GI&S/TM application requirements |
Functional Area Checklist #7
For
Airborne Reconnaissance
|
AR.1 |
Is airborne recce required/appropriate/feasible? |
|
|
AR.2 |
Who is the customer and where is the information to be delivered? |
|
|
AR.3 |
Type (IMINT, SIGINT, RADINT, MASINT.) |
|
|
AR.4 |
Essential Elements of information: What specific information can best be provided by airborne recce? |
|
|
AR.5 |
What is the level of accuracy required? |
|
|
AR.6 |
What resolution is required? |
|
|
AR.7 |
Are there area coverage requirements? |
|
|
AR.8 |
Age: How recent must the data be or what amount of change can be accommodated (i.e., bomb damage)? |
|
|
AR.9 |
Timeliness: When is the latest time the data will be useful? |
|
|
AR.10 |
What are the security classification restrictions? |
|
|
AR.11 |
What reporting/product format is desirable? |
|
|
AR.12 |
What databases will be used to store and retrieve the information? |
|
|
AR.13 |
Hard copy: size and number of prints, annotations |
|
|
AR.14 |
Soft copy: Magnetic tape, optical disk, NITF, BIT level |
|
|
AR.17 |
Is fused data/cross cueing required? |
|
|
AR.18 |
Operational issues |
|
|
• |
Multi-sensor platform |
|
|
• |
Basing options |
|
|
• |
Tether vs. extended tether |
|
|
• |
Overflight vs. standoff |
|
|
• |
Enemy defenses |
|
|
• |
Can allied resources be used? |
|
|
AR.20 |
Airborne recce requirements management |
|
Functional Area Checklist #8
For
Intelligence Data Handling Systems
|
IDHS.1 |
Are IDHS required? |
|
IDHS.2 |
Who is the customer and where is the product/service to be delivered? |
|
IDHS.3 |
Is automated intelligence data (electric or magnetic media) required for direct input into the weapon system or its associated mission planning system? |
|
IDHS.4 |
What is the target system? |
|
IDHS.5 |
What transmission media are needed? |
|
IDHS.6 |
Is there a known product currently available to meet the requirement? If so, what is it and who is the producer? |
|
IDHS.7 |
What data format is desired? |
|
IDHS.8 |
How time-sensitive is the required data? |
|
IDHS.9 |
How frequently is the data needed? |
|
IDHS.10 |
Is update by full-file replacement or report-by-exception preferred? |
|
IDHS.11 |
Is the requirement for raw intelligence or a fused product? |
|
IDHS.12 |
Will IDHS send a regular predefined product or is there need to respond to ad hoc tasking/query? |
|
IDHS.13 |
If ad hoc response is required, will the tasking/query be automated or will it flow through an external (to the system) route? |
|
IDHS.14 |
What is the highest classification of the target computer system? |
|
IDHS.15 |
What is the planned classification of any product produced by the target system? |
|
IDHS.16 |
Where, geographically, is the intelligence information to be delivered? |
|
IDHS.17 |
Are there already adequate communications in place to support any direct connection required? |
|
IDHS.18 |
Are there alternate methods for data dissemination (CD-ROMs, 8mm tapes)? |
|
IDHS.19 |
Does the target system exist or is it still in development? |
Functional Area Checklist #9
For
Force Management: Manpower And Training
|
FM.1 |
Are intelligence personnel needed to operate or support the system? |
|
FM.2 |
What type(s) of personnel are needed? |
|
FM.3 |
How compatible is the new system with systems currently in use? |
|
FM.4 |
How easy/difficult will the system be to operate/support? |
|
FM.5 |
What is the operator/system interface? |
|
FM.6 |
What tasks are required to operate the system (TASA or LSA)? (Include tasks, skills, and knowledge) |
|
FM.7 |
How many people will need training? |
|
FM.8 |
How soon will people need to be trained on the system? |
|
FM.9 |
Will the training be standard regardless of method used? (i.e., in-residence, exportable, OJT, or mobile training team) |
|
FM.10 |
Can the system incorporate imbedded training? |
|
FM.11 |
Is hardware common to other fielded systems? |
|
FM.12 |
Are operator tasks common to other fielded systems? |
|
FM.13 |
What are post-deployment training needs? |
Functional Area Checklist #10
For
General Military Intelligence Production (GMI)
|
GMI.1 |
Is GMI required? |
|
GMI.2 |
Who is the customer and where is the product to be delivered? |
|
GMI.3 |
What types of products are required? |
|
GMI.4 |
Essential elements of information (EEIs): What specific information must be derived from GMI? |
|
GMI.8 |
Age: How recent must the information be or how much change can be accommodated (i.e., bomb damage)?? |
|
GMI.9 |
Timeliness: When is the latest time the information will be useful? |
|
GMI.10 |
What are the security classification requirements and restrictions? |
|
GMI.12 |
What databases will be used to store and retrieve this information? |
|
GMI.13 |
What are the hard-copy requirements? |
|
GMI.14 |
What are the soft-copy requirements? |
|
GMI.60 |
Can requirement be satisfied through existing production? |
|
GMI.61 |
If existing products do not suffice, determine satisfaction through scheduled products. |
|
GMI.62 |
Assess the risk of not having the required intelligence for mission execution. |
|
GMI.63 |
Assess priority of this requirement in context of all outstanding requirements and the ISP. |
|
GMI.64 |
If no products (existing or scheduled) suffice, begin request/validation of requirement IAW DIAM 57-1. |
Functional Area Checklist #11
For
Development And Intelligence Infrastructure Issues
|
DI.20 |
Does the intelligence needed currently exist? |
|
DI.21 |
If not, can it be collected with current assets? |
|
DI.30 |
Are new collection management procedures needed? |
|
DI.31 |
Is there a product currently available to meet the need? In the proper format? |
|
DI.32 |
Can a current product be modified to meet the requirement? |
|
DI.33 |
Is a new product needed? How soon? |
|
DI.34 |
Is current intelligence adequate to support research, development and testing? |
|
DI.X |
Are there any unique intelligence requirements or support needs? (i.e., special modeling or simulation needs, SCIF space, SSO support?) |
7.8 Summary. By combining a weapon system’s operational imperatives with elements of the end-to-end, or horizontal, STT analysis, details such as where and how quickly information must be collected, analyzed, transmitted, stored, and processed can be assessed more realistically. Additionally, applying the functional area checklists allows related operational intelligence requirements to be identified more easily. These resulting requirements are then assessed against the existing intelligence infrastructure to identify shortfalls that could preclude mission accomplishment. Because they result from STT analysis and related operational imperatives, the resulting intelligence requirements are described in similar terms with associated satisfaction criteria such as the degree of geolocation accuracy or information timeliness.