
[Back]
|

[Index]
|

[Next]
| USAF INTELLIGENCE TARGETING GUIDE
AIR FORCE PAMPHLET 14- 210 Intelligence
1 FEBRUARY 1998
|
Chapter 11
TARGETING IN THE INFORMATION AGE
81
Page 82
83
82
Chapter 11
TARGETING IN THE INFORMATION AGE
11.1. Information Operations (IO) and Information Warfare . Information is central to the way the
U. S. wages war and will be critical to Air Force operations in the 21st Century. As Air Force doctrine
changes to recognize air and space operations, targeting will transition leaving behind the old paradigms
and institutionalizing info- oriented perspectives.
11.1.1. Department of Defense (DoD) Directive S- 3600.1 updates IO and IW policy, definition, and
responsibilities within the DoD. IW is a sub- set of Information Operations and is defined by the
directive as "Information's Operations conducted during time of crisis or conflict to achieve or pro-mote
specific objectives over a specific adversary or adversaries." Information Operations is defined
as "actions taken to affect adversary information and information systems while defending one's own
information, and information systems." The goal of IW is to achieve the Air Force core competency
of information superiority by successfully performing the missions of counter- information. Informa-tion
superiority is obtained over an adversary by controlling the information environment, exploiting
our advantage in information and information systems, and by using information to enhance our oper-ations.
IW employs a force- multiplier capability, enhancing and synergistically adding to other meth-ods
of warfighting.
11.1.2. Counter- information includes both defensive counterinformation (DCI) and offensive coun-terinformation
(OCI). DCI consists of security measures (information assurance and information
security), counterintelligence, counterdeception and counterpsychological operations (PSYOP). OCI
consists of PSYOP, electronic warfare (electronic attack, electronic protections, and electronic war-fare
support), military deception, physical attack and information attack. During times of crisis or
conflict (war), USAF IW activities must be integrated into the joint air and space operations plan and
air tasking order (ATO).
11.1.3. The Air Force leadership (CSAF and SECAF) views IW as an emerging concept of great sig-nificance,
as signified in the foreword of "Cornerstones of Information Warfare":
"As information systems permeate our military and civilian lives, we are crossing a new fron-tier
- the Information Age. It will define the 21st century and influence all we do as an air
force. Information Warfare has become central to the way nations fight wars, and will be crit-ical
to Air Force operations in the 21st century. This means, of course, that today we must
invest in our people, planning, equipment, and research so our ambitions can become reality.
We will involve every Air Force person in this effort, generating a wave of momentum that
will carry us into the next millennium."
"Information Warfare is not the exclusive domain of the Air Force, or any other service.
Information technology advances will make dramatic changes in how this nation fights wars
in the future. They will allow a commander's vision and view of the battlespace to be shared
at the lowest level. Because of this, every practitioner of the profession of arms has a respon-sibility
to understand the impact of information warfare on their service. From our unique
perspective as soldier, sailor, marine, or airman, we can then forge a common understanding
of how to use information warfare to enhance joint warfighting capabilities."
11.2. Objectives. "Cornerstones of Information Warfare" and "Air Force Doctrine Document (AFDD)
82
82
Page 83
84
83
2- 5, Information Operations" discuss the three objectives of IW:
Control the information realm so we can exploit it while protecting our own military information
functions from enemy action
Exploit control of information to employ information warfare against the enemy
Enhance overall force effectiveness by fully developing military information functions
11.3. Challenges. As the Air Force recognizes the significance of IW, its impact will be felt throughout
all aspects of Air Force intelligence. Unprecedented levels of detail, the identification of critical informa-tion
elements contained throughout the spectrum of the target categories, and compressed collection time-lines
are expected to characterize the general direction of change. Targeting support to IW is a challenge
and will require a collaborative effort across the operations, intelligence, and technical communities.
11.3.1. The ability to directly influence the information realm through Direct IW (Information
Attack) requires an entirely new direction of intelligence support. Methods of collecting and analyz-ing
the new types of intelligence necessary to plan and execute offensive and defensive aspects of this
mission will need to be incorporated. Targeting and combat assessment functions will become
increasingly complicated as they expand from their purely physical orientation to support warfare in
the information realm.
11.3.2. The Air Force views information as a separate realm, potent weapon, and lucrative target. In
looking at information as a distinctive realm, we are looking at expanding from the physical or mate-rial
level to what is described as the virtual level; a layer without geographical constraints. Within the
information battlespace, the means to achieve military objectives has now expanded. Not only can we
target traditional force elements with precision, but we can hold at risk the architecture that orches-trates
modern warfare. Information technologies will enable us to attack a significantly larger set of
targets using enhanced lethal and non lethal capabilities, greatly complicating weapon system alloca-tion
decisions.
11.4. Information Warfare and the Targeting Process. The impact of IW is addressed in detail across
the six phases of the targeting process: objectives and guidance; target development; weaponeering; force
application; execution planning; and combat assessment.
11.4.1. Objectives and Guidance Derivation . The development and dissemination of objectives
and guidance mark the first step in the targeting process and arguably the most critical. Targeting pro-fessionals
must comprehend National Command Authority (NCA) IW objectives and guidance as
passed to the Combatant Commanders. SECAF and JAG IW guidance must be followed and incorpo-rated
into IW actions. Targeteers should be intimately involved in the delineation of the cyberspace
equivalents of fire control measures, ( e. g., FSCL and Corps/ Division boundaries) to ensure deconflic-tion
and avoid fratricide. They also must become knowledgeable of Joint policy and doctrine for IW.
Targeting support to IW should be included not only in Air Force documents as this pamphlet but also
in joint documents such as Joint Pub 2- 0, Joint Doctrine for Intelligence Support to Operations and in
the forthcoming Joint Pub 2- 01.1, Joint Tactics, Techniques, and Procedures for Intelligence Support
to Targeting.
11.4.2. Target Development .
11.4.2.1. Intelligence must be readily accessible, timely, accurate and sufficiently detailed to sup-port
an array of DoD IO requirements, to include, research, development and acquisition and oper-
83
83
Page 84
85
84
ational support. Detailed intelligence on the information systems and the IO doctrine likely to be
employed by a wide range of adversaries must be provided. Essential Elements of Information
(EEIs) which support the prosecution of an IW strategy against individual targets and as part of an
overall campaign must be documented. Targeteers must work closely with the collection manage-ment
community to develop and modify EEIs for IW. The following sample IW EEI's (figure
11. 1) were developed in the Directorate of Research, Air Command and Staff College research
paper, "Information Warfare: An Opportunity for Modern Warfare":
Figure 11.1. Sample IW EEIs.
What is the IW Target description, location, significance?
What are its primary/ secondary functions?
What type of information is used/ processed/ communicated by the target? How is this information
received/ stored/ cataloged/ transmitted/ destroyed?
What physical attributes does the IW target possess?
Number of structures (physical description and locations of each)
Layout of each structure (size, entry/ exit points, room locations)
Construction and key components (materials, types of equipment)
Functional organization in each area (command, operations, maintenance, communications)
- What communications does the IW target use?
Type and parameters (telephone, TV, terrestrial radio, satellite, fiber, modulation type, waveform, fre-quency(
s) and power)
Country of origin, year manufactured, model, frequencies
Methods and procedures for securing communications
System manning and operating procedures
Number of each type of device and location
Signal allocation, controlling authority
Radio/ TV broadcast and newspaper (controlling agency, locations, operating procedures, political
affiliation, etc.)
Visual signs used (flags, panels, lights)
Noise signals used (klaxons, sirens)
84
84
Page 85
86
85
With whom does the target normally communicate?
Associated support facilities/ equipment and their locations
Number and location of personnel
Internal and external links
Switchboard, relay towers, rerouting centers
Type/ number/ location of antennas, cables, microwaves, local/ wide area networks, point- to- point,
etc.
What is the primary and alternate power supply?
Type, number, and locations
Associated facilities (transformers, relays, etc.)
Fuel supply (type, location)
Conduits (type, location)
What on- site security is employed?
Physical security (guards, fences, vaults, passive/ active detection systems, alarms etc.)
Location and type (guard posts, bunkers, trenches, etc.)
Physical description
Dimensions
Lighting (type, location, schedule)
Power source and location
Frequency/ schedule for patrols or security checks
Physical security procedures
Patrols (type, size, patrol routes, armament)
Detection systems (cameras, ground/ water/ air alarms, electromagnetic, etc.)
Barriers and obstacles (type, size, locations)
Entry and exit procedures (key, cipher, personnel recognition, code words, etc.)
What type of communications security and computer security are employed?
Type of security (cryptographic, physical access, hard wire, brevity codes, "sneaker" net)
Operating procedures
85
85
Page 86
87
86
11.4.2.2. IO are conducted across the full range of military operations. The focus of IO is on deci-sionmaking
and information- dependent systems, including weapons, infrastructure, command and
control, computer and associated network systems. Developing an IW targeting strategy requires
detailed intelligence and thorough analysis and planning to determine the best targets to achieve
desired effects efficiently and effectively. Critical elements must be developed for information
attack targets. Many target sets need to be reevaluated in light of the "information age" which has
automated many functions of modern day facilities. Target system category classifications must
be updated to facilitate analysis of IW considerations. DIA may need to update "Critical Elements
of Selected Generic Installations" (DDB- 2800- 2- 83 Chg 8, Aug 94) to identify critical informa-tion
elements and information attack options. This document currently identifies the critical ele-ments
of selected generic or typical installations appropriate for attack by air- delivered
conventional weapons and unconventional warfare (UW) operations; installations are identified
by the category codes of the DIA "Standard Coding Systems Functional Classification Hand-book"
(DIAM 65- 3- 1, Jul 95). Each listing begins with a brief general description of the installa-tion
summarizing its function and physical characteristics, followed by a table identifying the
critical elements and an estimated recuperation time for each critical element. A few examples
identifying information "critical elements" are taken from a paper on notional critical target sets
(figure 11.2) by Dr. Dan Kuehl from National Defense University, School of Information War-fare,
titled "Target Sets for Strategic Information Warfare in an Era of Comprehensive Situational
Awareness" and an Air University publication by Maj Steven M. Rinaldi, "Beyond the Industrial
Web, Economic Synergies and Targeting Methodologies."
Figure 11.2. Notional Critical Target Sets -- Strategic Information Warfare.
Cryptologic change schedule
Computer security
Type of security (physical, password, software monitoring)
Operating procedures
Infrastructure
Energy and power sources (both electric and POL)
Production centers
Transformer stations
Distribution nodes
Control centers for POL production and refining
Pumping stations
Backup systems
86
86
Page 87
88
87
Example: Use intrusive IW to seize control of the computer- controlled valve network in a major
POL refinery and shut down the flow of both unfinished and refined POL products. This would require
physical repairs such as valve replacement to offset the effects of the attack, and the plant would remain
hostage to a destructive attack using precision weaponry. This action would have impact ranging from mil-itary
effects (interdicting the supply of refined POL products) through economic and social effects. Maj
Rinaldi states "pipeline controls are electromechanical (relays) or solid state. The control network ties to-gether
all the elements of the pipeline system. Pipelines rely upon computerized supervisory control and
data acquisition (SCADA) system for control and management functions. SCADA systems are used to
control all operations and transmit information between dispatch control centers and remote terminal units
at pipeline facilities. Manual work arounds to loss of SCADA, electromechanical controls might be ex-tremely
difficult to carry out."
Information infrastructure
Telecommunications (radio & TV); public and secure switches
Radio relay facilities
Telephone exchanges
Fiber optic networks, nodes, and repeater stations
Microwave transmission networks and nodes
SATCOM links
Computer and data processing centers
National C3I centers
Example: use intrusive IW to override SATCOM dish controls and cause the dish to realign itself to
a useless/ unusable orientation. This would prevent our adversary from using its SATCOM capability with-out
requiring US forces to engage in destructive actions.
Political
Internal state police and control forces
Headquarters for internal control agencies (" secret police")
Intelligence collection systems (i. e. SIGINT intercept)
Databases supporting internal control systems
Example: Alter/ destroy via intrusive IW the enemy's computerized database of suspected internal
subversive elements. Follow up this action with an intensive PSYOPS effort aimed at dissident elements
in the population; this could seriously undermine a totalitarian state's control over segments of its popula-tion,
possibly threatening unrest or revolt.
Financial centers and networks
Institutions (banks, trading centers, etc.)
Currency controls and depositories
87
87
Page 88
89
88
11.4.2.3. Many organizations are developing decision aiding software applications that have the
ability to produce, as a final outcome, an installation (target) list. Examples include National Air
Intelligence Center's Interactive Country Studies and Links and Nodes Telecommunications
Databases; Air Force Information Warfare Center's SENSOR HARVEST; NSA's Adversary; and
some Joint Warfare Analysis Center's products. The final products of these various applications
must be able to interface with the targeting community's Rapid Application of Air Power
(RAAP), the USAF standard targeting application and the joint standard Air Tasking Order target-ing
application within the JFACC environment. RAAP is the interface between targeting planners
and the Advanced Planning System (APS) in CTAPS. This incorporation would enhance infor-mation
operations supporting C2W/ IW target system analysis and target list development. Auto-mated
target system analysis capabilities must be easily accessible by targeting personnel.
11.4.3. Weaponeering . Methodologies are needed to quantify the expected results from non lethal
weapons for IW attacks on specific types of targets, similar to JMEMs, which provides kill mecha-nisms
(blast, penetration, crater, fire), vulnerability data and damage criteria information for conven-tional
weapons. Candidate IW employment concepts include the following: (Research paper;
"Information Warfare: An Opportunity For Modern Warfare")
Corruption - The alteration of information content; the manipulation of data to make it either
nonsensical or inaccurate. Destroying existing knowledge.
Deception - A specific type of corruption; the alteration of, or adding to, information to por-tray
a situation different from reality. Creating false knowledge to include masquerading.
Delay - The reversible slowing of the flow of information through the system, and the slowing
of the acquisition and dissemination of new knowledge.
Denial - The reversible stopping of the flow of information for a period of time; although the
information may be transmitted and used within friendly territory, the adversary is denied
access to it. The prevention of the acquisition and dissemination of new knowledge.
Disruption - The reduction of the capacity to provide and/ or process information (reversible).
This is a combination of delay and corruption. The delay of the acquisition and dissemination
of new knowledge and the destruction of existing knowledge.
Degradation - The permanent reduction in the capacity to provide and/ or process information.
Destruction - The destruction of information before it can be transmitted; the permanent elim-ination
of the capacity to provide and/ or process information.
Each of the potential effects listed above have both desirable and undesirable attributes. While devel-oping
an IW strategy to employ these concepts, the planner must consider the potential impact of
these attributes on achieving the overall objective. These attributes include:
Persistency - How long will the IW strategy affect the target?
Speed - How long will it take to achieve the desired IW effect?
Latency - Can the IW tactic lie dormant within the target until needed?
Databases for financial management
Example: Electronically impose a UN- mandated quarantine of a rogue state's financial reserves;
could prevent arms purchases or the leader from looting the national treasury and fleeing.
88
88
Page 89
90
89
Reversibility - Is the IW effect reversible? Both reversible and irreversible effects can be
desirable.
Fratricide - Does the attack method cause unwanted effects on friendly systems?
Collateral Damage - Will attacking the target cause collateral damage in other systems
because of its linkage( s)? Will the method of attack cause unwanted effects on other systems?
Stealth - How easily can an enemy detect the friendly IW strategy? Exploitation and corrup-tion
of the enemy's information must be accomplished in a manner which is not readily detect-able.
The effectiveness of the attack is obviously degraded if the enemy gains knowledge of
it. (Note: In some cases, it may be beneficial to ensure the enemy knows the friendly infor-mation
operation capability).
Mutual Interference - Will attacking the target negate other information operations? If the
information employment concept is designed to create a false reality, then one must allow the
adversary to "see" or "hear" the false reality. Similarly, planners would not want to target a
critical node which can be exploited and serves to enhance information available to friendly
forces. This attribute, perhaps more than any other, affirms the need for a fully coordinated
and integrated IW strategy concept.
11.4.4. Force Application . Targeteers will need to become versed in lethal and non lethal methods
of attack available under IW, in addition to the more familiar conventional modes usually used. The
varied methods of attack and weapons will require strict deconfliction between planning and opera-tions
personnel. Targeting staffs which will be generating the ATO/ ITO will need to be responsible
for integrating the IW campaign effort (Table11.1.).HQ staff must push for appropriate levels of
participation commensurate with this responsibility.
Target development team members in the AOC for Information Warfare and Command and
Control Warfare (IW/ C2W) must be defined. The target development A3/ A2 members in the
AOC should be augmented as needed by members of the Air Force Space Support Teams
(AFSST), Information Warfare Support Teams (IWST), Joint C2W Center (JC2WC) Teams,
Land IW Activity (LIWA) and Naval IW Activity (NIWA)/ Fleet IW Center (FIWC). These
players can assist with IW/ C2W expertise for joint/ combined air campaign level targeting.
The A3/ A2 must determine the mix of augmentation and reachback needed to augment his
own IW/ C2W expertise and what the role, if any, of the 9AF IW Squadron and other IW's
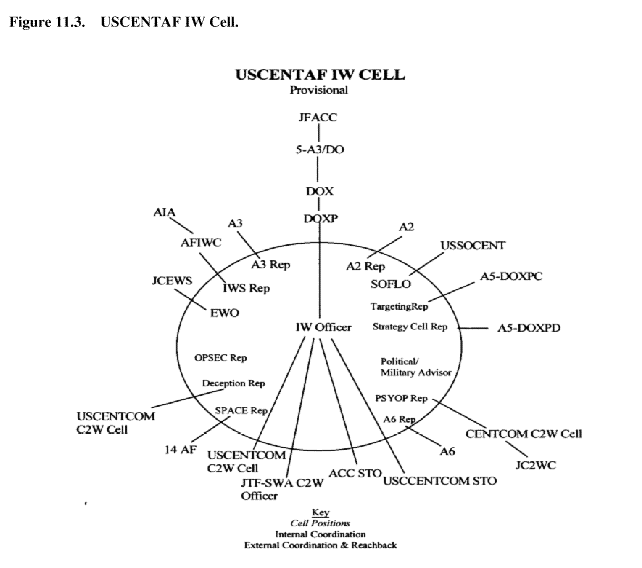
will be, once formed. Figure 11.3 illustrates the proposed USCENTAF IW Cell.
Table 11.1. Disabling Technologies and Kill Mechanisms.
MECHANISM
Combustion Chemistry
- Shut off/ overspeed engine
- Contaminate fuel
Polymer chemistry agents
- Damage vital components (e. g., Air filters)
- Polymerize fuel system
- Depolymerize plastics and electrical components
- Runway and roadway slippery/ stick
- Damage power grid (colloidal dust)
Antimateriel biological agents - Thicken fuels
- Dissolve electronics, plastics, solder, and other sub-stances
Superagents, acids, oxiders, and dissolving
agents
- Damage tires
- Disable mines
- Blind optical ports/ sensors
Computer viruses or worms
- Subvert communications, radar, satellite and com-puter
- signals control operations
Electro- magnetic pulse (EMP)
- Damage communication systems
- Explode ammo dumps
Blinding lasers
- Blind optics, dazzle operators, overload tracking
and targeting sensors
Neural inhibitors
- Short circuit human synoptic pathways
- Calmative agents Tranquilize personnel
- Infrasound Sound projection to disorient, sicken, or frighten
people from designated areas
Holographs
- PSYOPS to convince adversaries to act in desired
manner
89
89
Page 90
91
90 90
90
Page 91
92
91
Figure 11.3. USCENTAF IW Cell.
 11.4.5. Execution Planning . The existing ATO process used to provide mission targeting data is
tied to a 24- hour cycle of air combat operations. Incorporating IW techniques into an Integrated
Tasking Order (ITO) may require significant evolution of the process. Potential IW weapon systems
may be able to attack numerous targets within compressed time frames. In addition, generating addi-tional
information attacks from a particular weapon will not be tied to sortie turn rates and aircraft
maintenance capacities. An ITO process must be developed which will be able to fully exploit IW
capabilities as they become available. As IW capabilities are developed, the acquisition/ engineering
team should work with targeting personnel to ensure timelines for attack planning, generation, and
re- generation are known. These timelines should be taken into account and drive modifications to the
existing ATO process as necessary.
11.4.5. Execution Planning . The existing ATO process used to provide mission targeting data is
tied to a 24- hour cycle of air combat operations. Incorporating IW techniques into an Integrated
Tasking Order (ITO) may require significant evolution of the process. Potential IW weapon systems
may be able to attack numerous targets within compressed time frames. In addition, generating addi-tional
information attacks from a particular weapon will not be tied to sortie turn rates and aircraft
maintenance capacities. An ITO process must be developed which will be able to fully exploit IW
capabilities as they become available. As IW capabilities are developed, the acquisition/ engineering
team should work with targeting personnel to ensure timelines for attack planning, generation, and
re- generation are known. These timelines should be taken into account and drive modifications to the
existing ATO process as necessary.
11.4.5.1. Execution planning for IW will require target materials tailored to application of unique
weapons systems. Existing BTGs and other materials will not suffice for direct information attack
91
91
Page 92
93
92
techniques. Tools which aid selection of IW DMPI equivalents will be different from the standard
imagery and chart based target folders used today, and the requirement for a new line of IW target
materials needs to be considered. The particular requirements for mission planning and execution
will need to be taken into account in order to develop a product formatted to suit the needs of the
customer. One method of providing the vast amounts of data necessary for executing IW attacks
could be through "virtual" target folders. The particular information needed could be accessed
through an on- line or electronic product without deluging the operational planner with a huge hard
copy inventory.
11.4.6. Combat Assessment . The value of any targeting strategy is lost without an effective assess-ment
process. The AF must explore development of ways to measure non lethal battle damage to
allow for proper BDA. Planners must be able to provide probable effects of any given action to max-imize
the effectiveness of the IW strategy being developed, linking anticipated effects to desired
objectives. Using these probable effects, planners can then identify potential indicators that some-thing
has occurred as a result of our actions and develop an IW assessment plan to task collection
assets. Finally, analysts would conduct an IW reattack recommendation to evaluate the results of IW
actions taken. Current imagery based BDA methodology will not suffice for IW - there may be no
"smoking holes." The academic community should be tapped for technical research in this arena. The
Defense Intelligence Agency is responsible in DoDD S- 3600.1 "to provide the Chairman of the Joint
Chiefs of Staff and the Combatant Commands with the timely intelligence required for effective IW
post- strike analysis."
92

[Back]
|

[Index]
|

[Next]
| USAF INTELLIGENCE TARGETING GUIDE
AIR FORCE PAMPHLET 14- 210 Intelligence
1 FEBRUARY 1998
|









