
[Back]

[Index]

[Next]
AIR FORCE PAMPHLET 14- 210 Intelligence
1 FEBRUARY 1998
 [Back] |
 [Index] |
 [Next] | USAF INTELLIGENCE TARGETING GUIDE AIR FORCE PAMPHLET 14- 210 Intelligence 1 FEBRUARY 1998 |
41
5.1.1. There are no absolutes to conducting target development. The six targeting functions identi-fied as separate entities in a graphical representation are in fact intertwined. This is never more evi-dent than in target development where the targeteer goes "back" to help refine objectives and guidance and "forward" to weaponeering feasibility, force application, and combat assessment.
5.1.2. Evolution of the Target Development Concept . Targeteers have continually refined the concept of target development. There have been some fundamental problems that may seem obscure to the novice targeteer, but are important to our place in warfighting. Since Intelligence producers have "analyzed" the enemy, what then did targeteers do? Clarification came with the term "target development". We develop targets and inherent to this process is the analysis of targets, the analysis of target systems, and associated activities; but with an operational underpinning. This is the true art of the targeteer-- developing targets and bridging the areas (not gaps) of planners and operators.
5.2. Target Analysis. This is an examination of potential targets to determine military importance, prior-ity, and weapons required to obtain a desired level of damage or casualties. It is an open ended analysis of potential enemies. This pamphlet does not attempt to teach analysis, but gives some methods (see Attachment 5)proven useful for target intelligence in the past. They are useful for the real world only if they are appropriate to the environment in which they are used. The best analysis is reasoned thought with facts and conclusions, not a checklist. Target analysis is not the sole responsibility of targeteers. Most analysis is produced through the normal intelligence production process based on national and the-ater validated requirements. Targeteers concentrate on turning those products into target sets. Target analysis can be an iterative process with planners since objectives and guidance will never be finalized before the start of target analysis. Two broad approaches, critical node analysis and target system analysis are described below.
Foot Stomper Box
If targeteers don't provide full targeting service, then other well meaning but under trained and ill- experi-enced
groups will step in and attempt to provide that which is perceived to be missing.
41
42
5.2.2. Target System Analysis . Target system analysis is a systematic approach to determine enemy vulnerabilities and exploitable weaknesses. It determines what effects will likely be achieved against target systems and their associated activities. A targeteer must review the functions and inter-actions between components and elements of a target system to determine how the system works. The analysis provides the understanding for determining what effects are likely to be achieved by attack-ing the system, where the system must be attacked, and how long the attack will disrupt enemy plans or operations. By reviewing probabilities of damage and arrival for a weapon system, targeteers can evaluate the effects of attacks on different components and isolate relevant elements to plan the dis-ruption or neutralization of an entire target system.
5.2.3. There are three broad steps to target analysis.
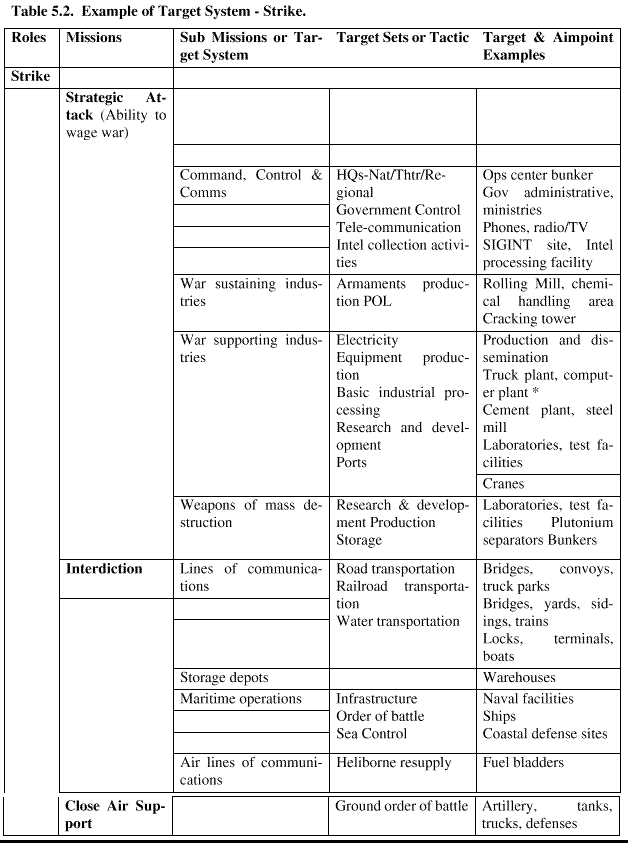
5.2.3.1. Target System Identification. The first step is to identify the target system( s) that sup-port the enemy activity to be affected. Air Force doctrine is a good guide for this task. We stress the following target sets are not the only answer nor are we suggesting these are the best answers. They are a good place to begin. Therefore, the best place to start is looking at the roles and mis-sions assigned. Table5.1.and Table5.2.show some generic representative target systems for various roles andmissionsof theAirForcefor use by targeteers. Again, we stress this is not a checklist but a good example of where airpower was used to advantage in many past conflicts and with a view to the future.
Tables 5.1 and 5.2. Generic Target Sets by Mission. The first step is to identify the target sys-tems supporting the enemy activity to be affected. There are several general categories of enemy target systems. Each is often associated with executing a standard Air Force strike or attack mis-sion:
Foot Stomper Box
Target analysis is a core competency within the targeting process. Don't just think
about target systems, but think through the analysis. DIA has produced a solid document in Critical Ele-ments
of Selected Generic Installations. Just remember it is generic and not every power plant, etc., is built
the same. Not every objective has a corresponding set of critical elements. Doctrine has generally accept-ed
a common term for the product of target analysis, "center( s) of gravity". These concepts need to be fur-ther
developed from the analysis of the enemy in their geo- political situation. The use of "centers of
gravity" allow discussions on broad goals when specifics are not required.
42
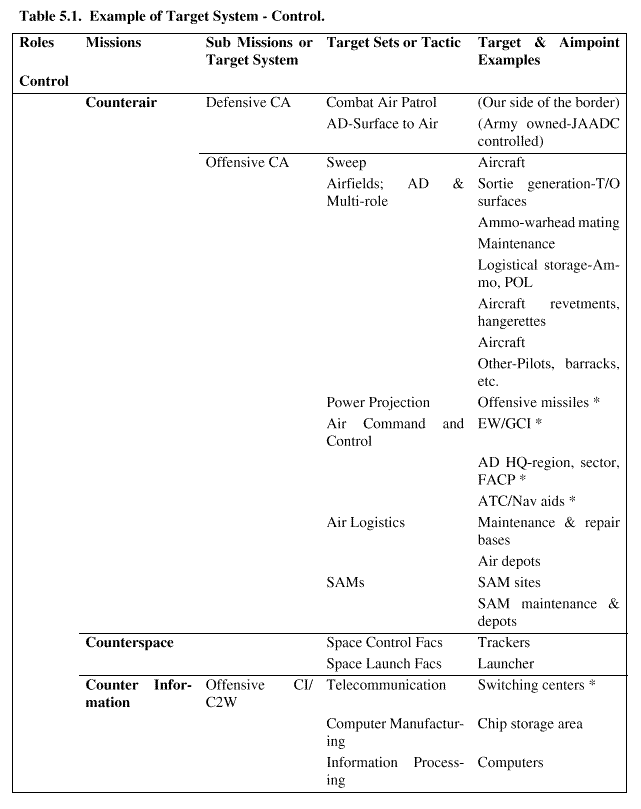
5.2.3.1.1. Control. Control includes counterair, counterspace, and counter information opera-tions. Targeteers are especially involved in offensive counterair and offensive counter infor-mation operations. Offensive counterair targets include aircraft, SAM and antiaircraft artillery (AAA) sites, air bases, air control systems, aviation POL stores, and other elements. Counter information targets include information via attack on facilities, hardware, software, or data.
5.2.3.1.1.1. Counterair Operations. Counterair operations aim to defeat or neutralize the enemy's air and missile forces.
5.2.3.1.1.2. Counterspace. Counterspace objectives include gaining and maintaining control of activities conducted in or through the space environment.
5.2.3.1.1.3. Counter Information. Counter information seeks to establish information superiority through control.
5.2.3.1.2. Strike. Strike includes strategic attack, interdiction, and close air support opera-tions.
5.2.3.1.2.1. Strategic Attack. This system includes the vital military and economic tar-gets that constitute a nation's war making capability and those targets essential to postwar recovery. Targets in this system include nuclear and conventional military capabilities, as well as political and economic resources.
5.2.3.1.2.2. Interdiction. Air interdiction (AI) operations are conducted to destroy, neu-tralize, or delay the enemy's military potential before it can be brought to bear effectively against friendly forces. Interdiction is conducted at such distance from friendly forces that detailed integration of each air mission with the fire and movement of friendly forces is not required. Some examples of target system components include: bridges, roads, railroads and classification yards, supply depots, maintenance and port facilities, waterways, petro-leum storage areas, petroleum pipelines and logistics facilities, aircraft, ships, and vehi-cles.
5.2.3.1.2.3. Close Air Support. Air support by fixed or rotary wing aircraft against hos-tile targets that are in close proximity to friendly forces, with deconfliction of each air mis-sion with the fire and movement of the friendly forces. Components of this type of target system include enemy troops, armor, artillery, and support elements.
5.2.3.1.3. Exceptions to the Rule. There are many examples of targets not apparently con-nected to the objective. The destruction of electric power generation normally is associated with the strategic attack mission but, if a country has electrified rail, it could also be consid-ered an interdiction mission. The destruction of an Iraqi railroad repair factory (strategic attack) during the Gulf War might have prevented the Iraqis from quickly moving two Repub-lican Guards divisions on railcars south (interdiction) toward Kuwait in October of 1994. Keep in mind each enemy's infrastructure is different.
Close Air Sup-port Ground order of battle Artillery, tanks, trucks, defenses 45
5.2.3.2.1. Potential targets may be located in various installation lists by category. An instal-lation list is a compendium of objects or areas used primarily for reference purposes. An example is the MIDB, which contains worldwide installation lists related to orders of battle. MIDB has been designated the migration system for the production and use of general military intelligence data. It is being designed to incorporate several programs into a single set of com-mon core database structures and analytical applications. MIDB will refocus the Integrated Data Base (IDB) toward the intelligence data user through a series of user interface upgrades that allow a friendlier operating environment. It will also improve the "tools" available to the user and include: look- up tables, help features, standard query tables, a graphical display capa-bility, and improved data output through a broader reports capability.
5.2.3. 2. 2. It is important to include all potential targets in the analysis. Although intuition, past experience, rules of engagement, and judgment may favor the exclusion of a given target, complete analysis may yield unanticipated results. All analysis should be as thorough as cir-cumstances, time, and resources allow.
5.2.3.2.3. After the target system is understood and individual targets identified for analysis, the target analyst should gather intelligence describing the characteristics of each one. Collec-tion requirements, RFIs, and production requests (PR) are input during system analysis. This is normally where collection managers are brought in to help refine requirements for intelli-gence production. Products such as intelligence dossiers, folders, and/ or automated files have been produced for many installations and target systems. These files provide historical infor-
Foot Stomper Box
Although many targeteers began their careers as imagery interpreters or in SIGINT,
it is not necessary to be an expert in those skills to be effective in target system analysis. First, much work
has already been published on generic industries and utilities. These generic critical components, such as
those found in DIA's Critical Elements of Selected Generic Installations, are also documented in other,
more specific Intelligence publication. But don't stop there. On the Air Force Targeting Homepage on
INTELINK you will find links to many potential sources.
46
5.2.3.3. Selection of Analysis Method . The analysis method selected should be appropriate not only to the target system but also understood by the people doing the analysis. All analysis tools have their strengths and weaknesses. If the targeteer does not understand the meaning behind the final answer then they do not have a good answer. Several methods of analysis follow, beginning with a traditional method of building a target system model and developing utility measurements.
5.2.3.3.1. Traditional target system analysis consisted of building a model. In broad terms, a model is a representation of a complex system (usually smaller than the system). By building a model, the relationship between components of the system can be portrayed using textual descriptions, flow charts, graphical depiction's, or mathematical models.
5.2.3.3.2. An element in modeling is the establishment of utility measures, which are numeri-cal ratings or weights assigned to system components to help the analyst compare targets and determine which has a higher importance than another. The numbers do not have to be real or represent any specific characteristics but are used only to show relationships between compo-nents. Promising potential targets can be determined and a measure of worth or value attached to each, reflecting its importance or contribution to the system to be affected or modified. Val-ues may be based on a purely functional determination or based on value to the enemy.
5.2.3.3.3. Target Value Analysis. Any target evaluation system must simplify a complex environment into a relatively small number of measurements that can be used to determine whether a proposed attack plan will have significant impact in terms of a specified goal. To be worthwhile, the system must be broad enough to include all relevant types of measurements and indicators. It must be structured into an orderly and systematic framework that will enable replication from situation to situation. It must also be flexible enough to be useful in a wide range of situations. In short, the system must strike a balance between too little and too much analysis.
5.2.3.3.3. 1. Target value analysis uses both qualitative and quantitative analysis. While the basis of target value analysis is qualitative decision- making (choosing among values), the techniques are quantitative. People and computers are both necessary for high quality target value analysis. In deciding the best way to attack a target system, the best decision shaping computer is an experienced targeteer. The problem is not merely one of develop-ing a computational process for decision shaping, but of making effective use of knowl-edge, training, and experience in the process. Some tasks are best accomplished by humans and others by machines, and the best qualities of each must be used in the deci-sion- shaping process. The machine can call forth and structure the information stored and available to targeting personnel, presenting accurate and complete data rapidly. The human participant can provide initial data, assign values to materials, and make decisions based on the data presentations. One of the most difficult and most important input is the measure of target value or utility.
5.2.3.3.3.2. The key concept in target value analysis is the need to analyze targets in terms of their comparative or relative worth. Central to this effort is the concept of "measurabil-ity." If a target cannot be measured in terms of its worth relative to another, then no 47
5.2.3.3.3.3. Certain considerations are important for all targets systems when determining which elements are appropriate for attack. Though many are not specifically quantifiable, the targeting planner should think about the following characteristics when attempting to assign a rank order to the various components of a system:
5.2.3.3.3.3. 1. Importance and Significance . Importance is a rough classification of the value to enemy military operations derived from all types of equipment, supplies, installations, and personnel used by enemy forces. Significance is the measure of con-cern for an activity or resources in excess of the value which would be assigned because of its normal performance (its importance). The measure may reflect military, economic, political, psychosocial, or geographic significance. Special significance assigned to a system may not reflect rational thought processes by the enemy and may be very difficult to assess. It is important to note that the concept of Importance and Significance is more than a semantic argument. It shapes decision making and adds validity to the targeting decision. An example of the difference follows. Tikrit, Iraq, is a medium size town with few war supporting and war sustaining functions. It is of medium- to- low importance to Iraqi war making capabilities. Tikrit is significant as the home of Saddam Hussein's family and personal power base.
5.2.3.3.3.3. 2. Depth . Depth is a measure of the time required before disruption of a component's activity affects the system output. Average depth is a time concept designed to measure the average interval between the time the production of an item begins and the time the finished product appears in use by a tactical unit. If dispersion is ignored and the average depth is considered an actual constant depth, then the depth of item X is the interval between the time production of X stops and the time the short-ages of X (or of times requiring X for their production) appear in tactical units in com-bat. In general, depth computation is important to measure the time available to the enemy to organize substitute consumption, alternate production, or alternate procure-ment before he suffers military damage.
5.2.3.3.3.3. 3. Reserves . Reserves are the quantity of stored resources the enemy may use when the normal supply of the resource is disrupted or when an excess demand is made on a component for its products or services. Assessment of reserves depends upon the estimation of the system use or flow rate. The measure of reserves is the per-centage of the products used versus the total products available. To guard against any loss of war- making ability, reserves must be readily available for use, and the quantity must be enough to last until normal supplies again become available. In an ideal situ-ation, the enemy should be forced to consume more of its reserves than it can replace.
5.2.3.3.3.3. 4. Cushion . Cushion is a quantity that prevents sudden shocks by absorb-ing impact. It is a measure of the extent to which a single target component or system 48
5.2.3.3.3.3. 4.1. Process and Equipment Substitutes . Unused capacity in a spe-cific industry can often be modified for use elsewhere in the economy, to replace destroyed capacity. Thus, the kilns used in annealing grinding wheels might be destroyed, yet similar kilns used for producing various kinds of ceramic wares could be adapted to the grinding wheel industry.
5.2.3.3.3.3. 4.2. Product or Service Substitutes . This includes saving remaining production of the attacked industry for the most vital military uses and using sub-stitute products for less important purposes. Thus, aluminum can be used for cop-per in high tension wires to save copper for signal equipment. There is a time dimension that is critical in the substitution process. That is, how rapidly and for how long can the substitute be produced or provided? The impact of costs of sub-stitution (in resources and in inferior performance) in military worth must also be considered.
5. 2. 3.3.3.3. 4. 3. Availability of Substitute Supplies and Services from Others . Even if the product has great military importance and there are no acceptable sub-stitutes, the industry or activity producing or providing it may be rejected as a tar-get if the enemy can obtain adequate supplies from sources other than domestic production such as from imports, reserves, repair, salvage, etc.
5.2.3.3.3.3. 5. Capacity . Capacity may be evaluated as either current output or maxi-mum output. Current output represents plant production based on the present labor force, economy of the country, current demand for the product, and demonstrated pro-duction over the past two or three years. Maximum output represents full capacity pro-duction based upon existing equipment and continuous operation over a 24- hour day.
5.2.3.3.3.3. 6. Product or Service Economic Value . This is the estimated cost to the enemy of producing or providing a product or service based on the cost of skilled workers, production plant, support facilities, equipment, supplies, etc. Target systems are grouped into one of three broad categories: sophisticated, costly (expensive) prod-uct; mechanized, moderately costly product; and nonmechanized, inexpensive product.
5.2.3.3.3.3. 7. Vulnerability . Vulnerability refers to the physical vulnerability of an installation or facility. Size, shape, and hardness all determine how susceptible a target is to damage. Vulnerability affects the size of force required to damage a target, as 49
5.2.3.3.3.3. 8. Reconstitution or Recuperability . This is a measurement of the time and cost required for a system to regain the ability to function after being disrupted. By assigning each type of target a reconstitution or recuperation time factor, such as days required to rebuild the facility or perform the original function again, the amount of target value that can be restored each day can be estimated using the reciprocal of the time factor. The target analyst can then forecast the stages of repair and replace-ment and determine the timing or necessity for a restrike. These factors depend on the type of installation, availability of repair materials, similarity and interchangeability of the damaged parts, and the importance of the installation to the enemy.
5.2.3.3.3.3. 8.1. Type of Installation . Both the function and complexity of instal-lation construction bear heavily on the time and capital required for replacement.
5.2.3.3.3.3. 8.2. Availability of Repair Materials . Depending on the installation, repair materials may or may not be stockpiled or even available within the country.
5.2.3.3.3.3. 8.3. Similarity and Interchangeability of Parts . This is allied to the availability of repair materials. Special parts can sometimes be obtained from a less important facility. However, often similar facilities by function cannot inter-change parts. Such situations are lucrative for exploitation, but require in- depth target analysis.
5.2.3.3.3.3. 8.4. Importance and Significance to the Enemy . Iraq chose not to rebuild some of its infrastructure after the Gulf War. The propaganda significance of these damaged functions to the Iraqi leadership outweighed the importance to the Iraqi people. Given this hindsight, was the military effort worth the results?
5.2.3.3.3.3. 9. Geographic Location . Targets may be selected or rejected based on their location. Before weapon systems attained global capability, range was the pri-mary targeting consideration in relation to location, and the capability of tactical forces to reach a target still remains an important factor. However, for systems analysts, the location of an installation in relation to the target system may be a valuable clue to the significance of the installation. For example, if a power plant is located near key mili-tary and industrial facilities, it is probably more important than a similar one located to serve only consumer needs. Also, if the target is too far removed from the battlefield, it may not have a direct impact on the battle.
5.2.3. 3.3.3. 9.1. Target location in relation to cultural features is also important since political factors influence target selection. If an attack on a target is consid-ered politically unfeasible because of possible damage to a nearby installation or population center, the target may not receive strike approval.
5.2.3.3.3.3. 10. Concentration or Dispersal. This is the geographic distribution of the installations in a target system or of target elements within a target complex. The types of weapons and forces required to neutralize the objective depend on the distribution of elements. Dispersal has a direct bearing on target vulnerability, and an installation with a large number of dispersed elements presents a more difficult targeting problem 50
5.2.3.3.3.3. 11. Mobility . This is a measure of the time required to shift a component activity from one location to another. Mobility affects both the perishability of the information about the location of the enemy system and friendly systems' ability to detect, locate, identify, and strike the target component.
5.2.3.3.3.3. 12. Countermeasures . This is a measure of enemy ability to counteract the potential disruptive activity of the friendly system through active and passive means. Effective use of terrain, camouflage, emission controls, passive defenses (caves, hangarettes, etc. ), and active defenses could negate the ability of the friendly system to exert an influence upon enemy component activity. This constitutes another aspect of target vulnerability.
5.3. Target Validation. Target validation ensures all nominated targets meet the objectives and criteria outlined in the expanded guidance. Targets are validated by evaluating and approving recommended tar-gets; validation should occur as early in the strike or attack cycle as appropriate. Certain questions should be considered during this portion of the target development process:
5.3.1. No- Fire Lists/ Prohibited Target Lists/ Protect Lists. In some situations, the highest- level decision making authorities may require that each potential target be evaluated in light of the rules of engagement, LOAC, or other restrictions and limitations. Potential targets may be withheld and approved for inclusion on a list of targets which may not be struck or attacked. Targets may be sub-mitted for no- hit protection based on their intelligence, operational, or political value, or deconfliction with other ongoing operations such as special operations, deception, or PSYOP. Targets may also be protected based on cultural, religious, or historic value (figure 5.1). 51
"To help strike planners, CENTCOM target intelligence analysts, in close coordination with the national intelligence agencies and the State Department, produced a joint no- fire target list. This list was a com-pilation of historical, archeological, economic, religious and politically sensitive installations in Iraq and Kuwait that could not be targeted. Additionally, target intelligence analysts were tasked to look in a six- mile area around each master attack target for schools, hospitals, and mosques to identify targets where extreme care was required in planning."Final Report to Congress, Conduct of the Persian Gulf War Title V Report
5.3.3. Risk of Collateral Damage. Collateral damage is generally defined as unintentional or inci-dental damage that occurs as a result of an attack but affects facilities, equipment, or personnel that are not militarily acceptable targets. Since this kind of damage is often the focal point for national and international scrutiny, the type and level of force applied against a target must be carefully selected to avoid excessive collateral damage. International law does not prohibit attacks against military objec-tives even though they may cause collateral damage since incidental damage is inevitable during armed conflict; but this damage should not be excessive in relation to the military advantage antici-pated.
5.3.4. Deconfliction. Proposed targets must be coordinated with appropriate agencies in a process called "deconfliction". Deconfliction is a checklist function. This checklist should be developed in the planning process and be appropriate to the organization. The many offices involved must be coor-dinated with to prevent incidents of friendly fire or propaganda for the enemy. Some examples where deconfliction take place are:
5.4. Documentation. Though administrative in nature, this fifth step is important. Documentation includes preparing a list of potential targets, dossiers of information on each potential target, and a file of validation request and approval messages. Figure 5.2 is one example of a format and content useful for collecting, organizing, and recording data for target analysis.
52
5.4.2. The target dossier on each potential target should include the following: at least six elements of target identification (BE number or unit ID, functional classification code, name, country code, coor-dinates with reference datum, and significance statement); available images, target materials, and amplifying text.
5.4.3. Target imagery research through local files is now supplemented through INTELINK and other electronic means including the Image Product Archives (IPA). This is a standardized library function supporting the retrieval of unexploited (raw) and exploited (finished) imagery derived products. These products are available to users at the national, theater, component and unit levels throughout the world. Users have two methods of accessing IPA, either through INTELINK, using network informa-tion discovery and retrieval tools (browsers) such as Mosaic or Netscape, or with the IPA- client tool.
5.4.4. Units may be required to produce target folders. The format of Combat Mission Folders can be found in MCR 55- 125, Preparation of Mission Planning Materials.
Figure 5.2. Example Targeting Worksheet.
DPI/ DGZ/ DMPI DATA (Use a separate sheet for each DPI/ DGZ/ DMPI) a. BE NUMBER b. CATEGORY CODE c. INSTALLATION NAME d. INSTALLATION COORDINATES (UTM AND GEOGRAPHIC) e. COUNTRY CODE f. GRAPHIC REFERENCE g. GRAPHIC DATE h. DPI/ DGZ/ DMPI DESIGNATION/ LOCATION (ACCURACY) i. DPI/ DGZ/ DMPI DESCRIPTION/ SIZE/ ORIENTATION/ AXIS OF ATTACK j. FUZING/ HEIGHT OF BURST k. CRITICALITY STATEMENT53PLANNING DATA a. DAMAGE CRITERIA (K- KILL, PTO, etc.) & LEVEL OF DAMAGE b. ACFT/ WPN/ MUNITIONS CEP c. SSPD/ FC d. PROBABILITY OF ARRIVAL e. DAMAGE EXPECTANCY/ COMPOUND DE f. UTILITY VALUE g. MARGINAL OUTPUT h. MARGINAL PRODUCT
5.5.1. Responsive Target Set. Target sets are built to respond specifically to objectives and guid-ance, assigned missions, options, and priorities. Such guidance may dictate that target sets be grouped geographically or be based on specific functional categories. Targets also may be grouped according to unique weapon system requirements. Another grouping may include restricted targets. Specialty target sets may include those selected for the employment of information operations or special opera-tions forces. During the objectives and guidance stage, predetermined percentages for destruction for each target set may have been laid out by the commander.
5.5.2. Target Lists. The recommended target list supports the target nomination briefing to the JFC. Target recommendations may be phased and grouped by mission, operation plan, option, or priority depending on the purpose and audience. They also may be grouped according to recommended weap-ons, e. g., mines or precision- guided munitions. Furthermore, they may be grouped according to weapon system recommendations, e. g., B- 52s or Tomahawk Land Attack Missiles (TLAMs). Target-ing personnel should be prepared to provide the full range of information to the operations staff in support of force application. Targeteers and operations planners continue to work together to adjust the recommendations.
5.5.2. 1. The targeteer provides the commander or his designated target approval representative with a prioritized list of specific validated targets. This list provides planners with the name, BE number( s), coordinates, function, description, possible aimpoints, effects desired on the target, and tentative weaponeering solutions. The targeteer includes a statement on the significance of the target in light of the commander's objectives. Often, other analyst comments are includes, par-ticularly if the target can be affected through non lethal means. The list may also include addi-tional information such as the requesting service and even a recommendation as to which service should be responsible for attacking that target. A word of caution at this point, the target list has not been finalized-- it is a working list that requires more evaluation before specific tasking can begin.
5.5.2.2. Target List Approval Importance . Target lists are important because they drive force employment, as well as production of intelligence for aircrews and missileers. Production of tar-get materials in sufficient quantities and detail for all possible users is a complex and time con-suming process that imposes severe demands on scarce resources. Also, the production cannot be quickly expanded in quantity, only focused on subject. This is the reason operations plans'
54
55
5.5.2.2.1. The newer targeting tools (i. e., Rapid Application of Airpower) should assist in this process by checking such database items as the category code of the target nomination or its location. Also, a new graphical presentation application on RAAP can help the approval pro-cess.
5. 5. 2.2.2. The target list is then sent up the chain of command to, eventually, the theater CINC. This is most often done via briefing at each level. A Joint Target Coordination Board (JTCB) often is designated to formalize the nomination process.
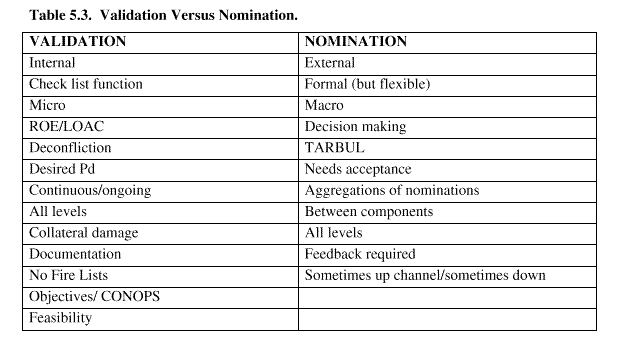
5.5.3. Where Validation and Nomination Occur. While validation or nomination will occur in all phases of the target process, there are certain characteristics that tend to make the majority of nomina-tions fall within force selection/ application or within the target development phase. Table5.3.lists their characteristics to distinguish the functions.
Table 5.3. Validation Versus Nomination.
5.6. Establishing Collection and Exploitation Requirements. The last step in target development is to establish collection and exploitation requirements for each potential target. These requirements must be articulated early in the targeting process to support target development and eventually combat assessment. A good knowledge of the types and sources of intelligence as related in Chapter 2 and Attachment 3 will help the targeteer write better Requests for Information (RFI) and Production Requests (PR). One natural area for consolidation of AOC Target Branch collection management inputs is the Combat Assessment Cell where a single POC (per shift) can interface with the Collection Management Branch.
 [Back] |
 [Index] |
 [Next] | USAF INTELLIGENCE TARGETING GUIDE AIR FORCE PAMPHLET 14- 210 Intelligence 1 FEBRUARY 1998 |