Naval INFOSEC Universe Description Report
(IUDR)
Space and Naval Warfare Systems Command
Information Systems Security Office (SPAWAR PD 51)
18 January 1994
1.0 INTRODUCTION
1.1 Background
As demonstrated in Operations Desert Shield and Desert Storm, information is an
essential ingredient of modern Naval operations for both war fighting and
peacetime situations. The security of that information and the associated
information processing resources is critical to the success of military
missions. However, the unprecedented development of information system
technology and the proliferation of wide area networks have exposed new
vulnerabilities of the Navy's information systems. The mission criticality of
information coupled with these new vulnerabilities introduces special
requirements for the security of information systems that drives the need for
an Information Systems Security (INFOSEC) program. Although security tools and
products are available to address some of the new vulnerabilities, there is a
need to focus security resources within the Department of the Navy (DoN) and to
implement a top-
down
systems engineering approach to the development and fielding of INFOSEC, both
to achieve economies and timeliness in system acquisition and to achieve the
effectiveness required of fielded secure information systems.
On 27 December 1992, the SPAWAR Information Systems Security Office (initially
SPAWAR ;00I, recently renamed SPAWAR ;PD 51) was established as the focal point
for implementing DoN INFOSEC policy. SPAWAR PD 51 is organized into three
primary divisions: PD 51E, Chief Engineer, PD 51C, Customer Service, and PD
51M, Program Manager. PD ;51 is supported by PD ;50L, Integrated Logistics
Support, PD ;50I, Foreign Military Sales, and PD ;50P4, Financial Management.
PD 51E is responsible for developing Naval INFOSEC architectures, standards,
and tools; for developing INFOSEC investment strategies; for focusing the Naval
INFOSEC technology base; for developing and promoting INFOSEC interoperability
strategies; and for identifying and coordinating resource requirements to
support the Operational Users and program managers of Naval INFOSEC systems.
PD 51C is responsible for identifying Operational User requirements for INFOSEC
products, technologies, systems, and services and for providing INFOSEC
engineering services to the PMs and Operational Users. PD 51M is responsible
for managing the development and implementation of INFOSEC products and systems
for operational use in Naval information systems, and potentially Joint Service
or Allied information systems for which the Navy is the lead Service for all or
at least the INFOSEC portions of the system. The Appendix provides a summary
of the interactions among these primary divisions of SPAWAR ;PD ;51 and the
interactions of each with the remainder of the INFOSEC Universe. These are
derived from the interactions developed later in this report from the most
recent organization statements for PD ;51.
1.2 Purpose
The Naval INFOSEC Universe (NIU) is that portion of the total universe of
systems with INFOSEC requirements and organizations with INFOSEC
responsibilities (i.e., the total INFOSEC Universe) that is subject to Naval
INFOSEC policy. The purpose of this document, the Naval INFOSEC Universe
Description Report (IUDR), is the following:
- To establish what are the systems and organizations that lie inside and
outside the NIU.
- To define and describe the important INFOSEC attributes of these systems
and the INFOSEC roles of these organizations.
- To provide a vehicle for achieving agreement within the Naval INFOSEC
Community on the boundary and content of the NIU.
- To define the INFOSEC-
related
interactions of Operational Users, Program Managers, and SPAWAR ;PD 51 in this
universe.
- To describe the general interactions of SPAWAR ;PD 51 with other
organizations in the INFOSEC Universe and to lay the groundwork for a detailed
blueprint of the interactions required of the SPAWAR PD 51 organization to
effectively implement its charter as the Naval focal point for INFOSEC.
- To provide the basis for more detailed analyses that will address
formulation of a Naval INFOSEC investment strategy in a systematic manner. The
INFOSEC investment areas that will be addressed are: the technology base,
processes, tools, standards, products, and resources.
1.3 Scope
This document concentrates on the role of SPAWAR PD ;51 as the Navy's INFOSEC
focal point for information systems that are subject to Naval INFOSEC policy.
This INFOSEC role is accomplished through systems engineering, customer
support, program management, and mutual interactions among the following major
participants in the INFOSEC Universe:
- SPAWAR PD ;51.
- Program managers of information systems requiring INFOSEC.
- Operational Users of these information systems.
Also important to the
INFOSEC role are the essential INFOSEC-
related
interactions between these three participants and the remaining government
organizations in the INFOSEC Universe. (It is assumed that contractor
organizations will support and occasionally act for their government
organization principals.) Discussion of the interaction among these remaining
organizations is outside the scope of this document.
The information systems that are subject to Naval INFOSEC policy, and are thus
members of the INFOSEC Universe, have the following uses:
- Command, control, communications, computers, and intelligence (C4I).
- Mission support.
- Training.
These systems are employed during peacetime, wartime,
training exercises, or test evaluations. They are used by organizations that
are part of the DoN, by organizations that are provided INFOSEC support by the
DoN, and by organizations for which the Navy is the lead service for
development of the information system. These user organizations are the
following:
- U.S. Navy.
- U.S. Marine Corps.
- Maritime Sealift Command.
- U.S. Coast Guard.
- Joint Services.
- North Atlantic Treaty Organization (NATO).
2.0 DERIVATION OF NAVAL INFOSEC ATTRIBUTES
INFOSEC is defined in National Security Telecommunications and Information
Systems Security Instruction (NSTISSI) 4009 as "the protection of information
systems against unauthorized access to, or modification of information, whether
in storage, processing, or transit and against the denial of service to
authorized users, or the provision of service to unauthorized users, including
those measures necessary to detect, document, and counter such threats."
Previously, separate security policies and doctrines addressed protection of
computer systems (COMPUSEC), information transfer systems (COMSEC), and
emanations (TEMPEST). With today's proliferation of information processing
networks, the separate implementation of these related disciplines for
information protection is no longer technically or fiscally feasible.
Information systems security (INFOSEC) is the modern discipline that provides
an integrated and systematic approach to the security of all aspects of
information systems. The term "secure information system" is used throughout
this document to mean any information storage, processing, or transfer system
that requires or uses INFOSEC features and/or components.
The focus of this section is the description of the security-
relevant
characteristics, termed "attributes," of information systems in the context of
the NIU. These attributes will be used to define the interactions among the
key players necessary to field and support secure information systems that will
contribute to the successful prosecution of Naval missions. Naval INFOSEC
attributes must, therefore, be derived from an understanding of Naval missions,
information value, and threat scenarios. The platforms, information systems,
and organizations that implement these attributes in the NIU, and their
interactions among the key NIU organizations in support of these attributes,
are described in Section 3.
2.1 Naval INFOSEC Threat Scenarios
Naval information systems store, process, and communicate large quantities of
information. Much of this information is critical to satisfying the Naval war
fighting and support missions. Recent advances in communications and
information processing technology that increase the distribution and exposure
of this information also increase the vulnerability of Naval systems to
exploitation both by accidental and malicious threat agents. Modern
information systems may be vulnerable to any or all of the following threats:
- Unauthorized disclosure of classified data or unclassified but sensitive
data.
- Denied access to information or use of the system.
- Modification of data processed by the system or modification of the system
itself.
- Spoofing or fooling the system or its users to take unauthorized or
incorrect actions.
Threats can exploit system vulnerabilities when
adversaries have the intent and adequate resources. Appropriate security
mechanisms must be incorporated in Naval information systems to protect system
vulnerabilities from exploitation.
2.2 INFOSEC Attributes of Naval Information Systems
This section summarizes the INFOSEC attributes of Naval information systems.
These attributes were derived from a detailed analysis of Naval information
systems based on Naval missions (spanning peacetime to wartime), information
value, and threat scenarios. The criticality of information to these missions
has raised its protection through INFOSEC engineering to the same level of
importance in the systems engineering process as, for example, fault tolerance,
real-
time
operation, and interoperability. Correct INFOSEC engineering to achieve the
correct INFOSEC attributes demands strict adherence to security policy, formal
validation and verification of security designs, absolute traceability of
design to requirements, and acceptance (by signature and with legal
implications) of residual security risks by the Operational Users and
information owners. The INFOSEC attributes summarized in this section form the
basis for the roles of and required interactions among the three primary
participants in the NIU and their required interactions with the remaining
INFOSEC Universe organizations.
2.2.1 Security Features
2.2.1.1 Confidentiality
The confidentiality attribute is defined by the extent of the protection
afforded by the security service from disclosure of information to unauthorized
entities (e.g., individuals, organizations, equipment, processes). Examples of
protected information include user and operational information, administrative
information, security parameters (e.g., cryptographic key material), system
characteristics (e.g., operational capabilities, location, or vulnerabilities).
At a more detailed level, confidentiality may be divided into four subordinate
services: information confidentiality, traffic flow
confidentiality, emanations security, and signals security.
Security mechanisms that implement the confidentiality attribute include
access control, object reuse, encryption, TEMPEST techniques, physical
isolation, and administrative procedures.
2.2.1.2 Integrity
The integrity attribute is defined by the extent of the protection
afforded by the security service from information or resources being created,
inserted, modified, or deleted by entities not authorized for these actions.
Examples of integrity protection include the prevention or detection from these
actions, and may also provide capabilities to recover from successful attacks
on the integrity of a system. At the next lower level of detail, the
Integrity attribute may be divided into system integrity, equipment
and software integrity, and information integrity. The
integrity attribute also includes authenticity, the means for
proving the identity of the source of an action taken on the system, and non-
repudiation,
the ability to protect against an entity's falsely denying sending information
or falsely denying receipt of information. Security mechanisms that implement
the integrity attribute include cryptographic checksums, error detection
and correction techniques, message authentication codes, and digital signatures.
2.2.1.3 Availability
The availability attribute is defined by the extent to which the
security services ensure that a system's capabilities are accessible and/or
operational and information is obtainable by authorized entities. Availability
services allow the system and/or individual components of the system to meet
user-
specified
requirements for unobstructed operation and allow the system to make
information accessible to users when needed. Failure of availability results
in denial of service conditions. For the NIU, availability is limited to
services that protect the system when threatened by malicious threat agents.
Security mechanisms that implement the availability attribute include robust
routing algorithms, duplication of critical system functions, security audit
and alarm procedures, and system resource usage controls.
2.2.2 Strength of Security Features
The strength of security is defined by the extent to which a hostile entity
must expend resources to defeat the security feature. The items listed in
Section 2.3.1 are the primary security features to be provided. These features
may be implemented by a number of security mechanisms. In addition to the
"what" that is to be implemented to provide the security services, the question
of "how much" security is adequate must also be described. For example, longer
key lengths generally provide additional protection of encrypted information
from threats of eavesdropping and cryptanalysis. The known threat environment
for a system in the context of its mission and operational environment should
drive the required strength of security features. Generally, stronger security
features involve additional costs; therefore, a goal of the security
engineering process is to provide "enough" security, as described in 3.3, but
not more than can be afforded.
2.2.3 Assurance of Security Features
The assurance attribute is the level of confidence that a system's
security approach is suitable for countering identified threats (effectiveness)
and that security components used within the system are capable of performing
their security functions correctly (correctness). Assurance is provided
through top-
down
policy-
driven
security design and implementation, through analyses of the implemented
security mechanisms, and validation through the formal Certification and
Accreditation processes that requirements are met. In addition, assurance is
provided for operational systems by on-
line
monitoring of the security status of the system and feedback of this status to
the system operator or to the system or security administrator. For fielded
systems, reaccreditation is invoked frequently for increased assurance,
especially when system security features are modified.
2.2.4 Operability
Operability is the extent to which the integration of INFOSEC into an
information system affects system performance. Factors that influence
operability include security-
relevant
information overhead (e.g., security management information exchanges,
cryptographic synchronization preambles)and security interoperability of the
information systems.
2.2.5 Useability
Useability defines the extent to which integration of INFOSEC features
into the information system affects the system operators. Important mechanisms
for useability include end-
user
transparency, menu-
driven
operator interface, built-
in
training, support of user and device mobility, support of single logon, ease of
maintenance, on-
line
accountability, and visible security/risk indicators.
2.2.6 Affordability
The affordability attribute is the extent to which INFOSEC features are
cost effective (for both recurring and non-
recurring
costs). Affordability of INFOSEC features can be supported by incorporation of
commercial off-
the-
shelf
(COTS) and/or government off-
the-
shelf
(GOTS) products where possible, modularity of INFOSEC design, life cycle
logistics supportability (e.g., vendor support for upgrades), reuse of
software, components, and certification documentation and evidence, and
conservative use of security mechanisms to avoid over-
design.
2.2.7 Timeliness
The timeliness attribute for INFOSEC system development and fielding is
the extent to which the information system's schedule is met for implementation
of the system's INFOSEC features. Mechanisms for achieving timeliness include
rapid prototyping; reuse of relevant designs, security documentation, and
certification evidence; advance planning for INFOSEC products to ensure time
for certification/evaluation; use of open systems standards; and use of COTS
and/or GOTS products.
2.2.8 Criticality
The criticality attribute is the degree of importance associated with an
information system's mission, operational scenario, threat environment, and
consequences of system failure or subversion. The criticality attribute
supports prioritization of INFOSEC system engineering activities. The
operational scenario includes peacetime, wartime, training, and test and
evaluation (T&E). The consequences of system failure or subversion include
mission failure, loss of physical resources, loss of national economic status,
loss of national security, and loss of life.
3.0 THE NAVAL INFOSEC UNIVERSE
3.1 Definition and Boundaries
The NIU is defined as the set of all organizations and secure information
systems that are subject to Naval INFOSEC policy and the platforms on which
they reside. The NIU is a subset of the larger INFOSEC Universe that
encompasses all systems, activities, and organizations with INFOSEC content.
In the characterization adopted in the IUDR, systems and organizations that may
affect Naval INFOSEC but which are not subject to Naval INFOSEC policy occupy
positions outside the NIU boundary. There are some systems (e.g., Joint C4I
systems) that are partially subject to Naval INFOSEC policy and partially
outside its influence. These occupy positions on the NIU boundary.
3.2 Platforms in the NIU
The platforms in the NIU provide the environment for personnel and systems to
implement their assigned missions. Platforms in the NIU include:
- U.S Navy platforms (e.g., surface ships, submarines, unmanned platforms
including satellites, and shore installations).
- Marine Corps platforms (e.g., manpacks, tanks, Armored Personnel Carriers
(APCs), High Mobility Multi-
terrain
Wheeled Vehicles (HMMWVs), aircraft, and river patrol boats).
- Coast Guard platforms (e.g., surface ships, aircraft, and shore
stations).
- Maritime Sealift Command platforms (e.g., surface ships).
Each of
these platforms has specific INFOSEC implications, particularly with respect to
physical, personnel, and procedural security characteristics.
3.3 NIU and Interfacing Information Systems
Figure 1 summarizes the systems of the INFOSEC Universe. The portion of the
INFOSEC Universe subject to Naval policy (i.e., the NIU) includes the
information storage, processing, and transfer systems resident on NIU platforms
that allow personnel to implement assigned missions. These systems are divided
into the following categories:
- C4I systems are all of the computer and telecommunications systems
used on NIU afloat, airborne, and ashore platforms to command, control,
monitor, and manage war fighting efforts. Any local or wide area networks used
with these platforms are also included in this category.
- Naval combat direction systems include all computer and display
systems used by warfare commanders to analyze real-
time
threat information and deploy combat forces.
- Naval weapons control systems include all automated weapons control
computer systems, including weapons control microprocessors
- Naval process control systems include computers or microprocessors
used to control the operation of the platform. Usually, the correct operation
of these processors is critical to the correct operation of the platform.
- Naval telemetry systems include data communications links from
sensors or other remote sources
- Naval sensor systems include transducers that sense acoustic,
electromagnetic, or other energy and transform it into a form for transmission
to information systems.
- Mission support systems include all non-tactical computer and
telecommunications systems and networks at NIU facilities, including navigation
systems, identification friend or foe (IFF) systems, weather reporting systems,
threat warning systems, and maintenance systems as well as payroll, medical,
repair records, entertainment and morale systems.
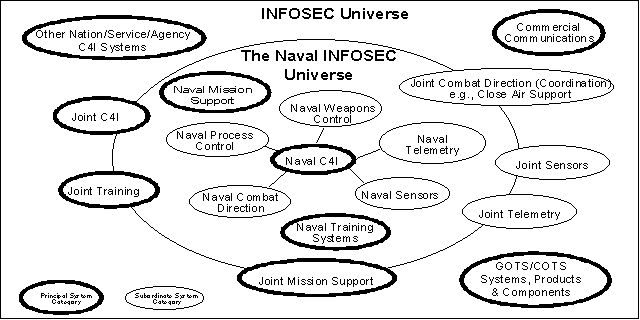
Figure 1. Systems of the INFOSEC Universe
-
-
- Training systems are dedicated to the training of military
personnel in various aspects of war fighting. These systems are not used
during operational war fighting missions; the threats against these systems and
their INFOSEC requirements often differ from systems used for war
fighting.
External to the NIU (but maintaining important interfaces to it)
are the following
- Other Nation/Service/Agency C4I systems.
- Commercial communications systems.
- GOTS/COTS systems/products/components.
On the boundary (i.e., subject
in part to Naval policy) are the following:
- Joint C4I systems.
- Joint combat direction systems.
- Joint sensor systems.
- Joint telemetry systems
- Joint mission support systems
- Joint training systems.
3.4 Organizations of the INFOSEC Universe
Figure 2 summarizes the organizational structure of the NIU and depicts its
relationship with the larger INFOSEC Universe. As with the systems of the
INFOSEC Universe, organizations subject to Naval policy are shown inside the
NIU boundary, and organizations that have important INFOSEC roles but are not
subject to Naval policy are shown outside the boundary.
3.4.1 Roles of Organizations Inside the NIU
The security-
relevant
roles of the organizations inside the NIU are the following:
- The Office of the Secretary of the Navy (SECNAV) interprets
National and DoD security policies and provides Naval INFOSEC policy and
guidance to the NIU.
- The Naval Investigative Service Command (NIS) prepares security
policy for TEMPEST, physical, and personnel security.
- The Naval Information Systems Management Center (NISMC)
prepares security policy for signature out of SECNAV.
- The Office of the Chief of Naval Operations (OPNAV) defines Naval
missions and requirements and sponsors the development and operational test of
Naval systems.
- The Office of Naval Intelligence (ONI) sponsors the system
engineering and development of special compartmented information (SCI)
information systems.
- The Naval Security Group (NSG) is the Office of Primary
Responsibility (OPR) for signals intelligence (SIGINT) systems. The NSG also
provides vulnerability analysis and testing from a signals analysis point of
view.
- The Naval Intelligence Command (NIC) prepares tailored intelligence
reports and prepares security policies for SCI systems.
- The Naval Maritime Intelligence Command (NAVMIC) interprets
National threat assessments for Naval systems.
- Operational Test and Evaluation Forces (OPTEVFOR) perform
operational test and evaluation of DoD systems (including operational security
testing for some systems).
- System Commands/Program Executive Officers (PEOs) manage the
acquisition of information systems for warfare platforms.
- Program Managers (PMs) plan, program, budget, and execute
programs to develop, acquire, and provide life cycle support for specific
information systems.
- Warfare Centers develop information systems for assigned warfare
areas (e.g., Air Warfare, Undersea Warfare, Surface Warfare).
- Operational Users operate and maintain information systems. They
also provide feedback on system operation and identify requirements for new
information systems and for upgrades to existing systems.
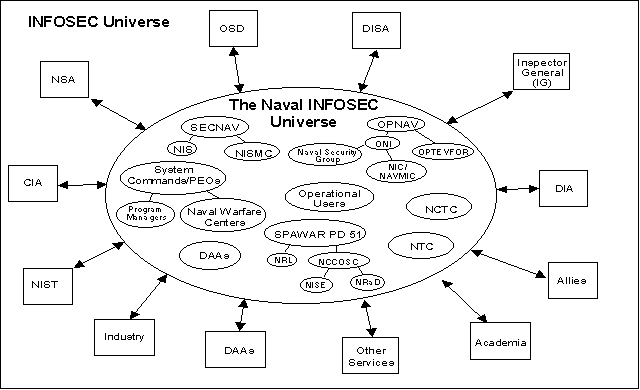
Figure 2. Organizations of the NIU.
- The Naval Computer and Telecommunications Command (NCTC) generates
and distributes Naval cryptographic keying material, develops strategic
information systems and networks, and provides security training.
- Designated Approval Authorities (DAAs) accredit secure
information systems for operation and assume responsibility for the residual
risk in their operation. Depending on the type of information involved, the
role of DAA could be performed by a variety of organizations, both inside and
outside the NIU.
- SPAWAR PD 51 responds to and interprets National, DoD, and DoN
INFOSEC policy; acts as focal point for providing and coordinating INFOSEC
services for DoN; coordinates INFOSEC requirements and solutions with other
Services, DISA, NSA, other Agencies, and industry; and acts as PM for those
information security systems and components for which the Navy is
responsible.
- The Naval Research Laboratory (NRL) provides technical resources to
support SPAWAR PD 51; performs INFOSEC research; develops INFOSEC technology,
system prototypes, processes, and methodologies; and conducts security
certification, test, and evaluation.
- The Naval Command, Control and Ocean Surveillance Center (NCCOSC)
including its components NCCOSC In-
Service
Engineering East (NISE), The Naval Research and Development Laboratory
(NRaD), and The Naval Electronics System Security Engineering Center
(NESSEC) provides technical resources to support SPAWAR PD 51; develops
secure information technology and system prototypes; provides security
engineering services to fielded secure information systems; and conducts
TEMPEST testing.
- The Naval Training Center (NTC) provides training in COMSEC
techniques, COMSEC equipment operations and repair, and Cryptologic Materiel
System (CMS) custodian duties.
3.4.2 Roles of Organizations Outside the NIU
The roles of the organizations that play a role in Naval INFOSEC but are
outside the NIU boundary are the following:
- The Office of the Secretary of Defense (OSD)
interprets national INFOSEC policy for DoD.
- The Defense Information Systems Agency (DISA) develops
architectures and standards for Joint Service interoperability and maintains a
database of approved INFOSEC products for Service use.
- The Inspector General (IG) inspects secure information systems for
compliance with the system security policy and, periodically during the life of
the system, for secure operation.
- The Defense Intelligence Agency (DIA) performs vulnerability
analyses of DoD intelligence information systems; serves as DAA for DoD and/or
DoN intelligence systems.
- Other Services/Allies coordinate with DoN to ensure INFOSEC
interoperability.
- Academia performs research on, or proofs of concept for, secure
systems and technology.
- DAA's accredit secure information systems for operation and assume
responsibility for the residual risk in system operation. DAAs may be either
inside the NIU or outside it.
- Industry develops and provides INFOSEC products and secure
information systems.
- The National Institute of Standards and Technology (NIST) develops
systems and standards for protection of unclassified but sensitive
information.
- The Central Intelligence Agency (CIA) provides INFOSEC
threat assessments for all DoD intelligence systems.
- The National Security Agency (NSA) provides detailed
security requirements for DoD information systems and products; evaluates and
certifies selected secure information systems; develops cryptographic
algorithms, modules, and systems; and provides centralized key management
services.
3.5 Interactions in the NIU
The interactions described in this section are those required to ensure that
the INFOSEC attributes set out in Section 2 are an integral part of Naval
information systems in the future. Figure 3 summarizes the principal
interactions of the Operational Users in the NIU; these interactions are
described in more detail in Section 3.5.1. The interactions of the Program
Managers of information systems with INFOSEC requirements are summarized in
Figure 4 and described in more detail in Section 3.5.2. Section 3.5.3
describes the interactions of SPAWAR PD 51 in the INFOSEC Universe more fully.
In each figure, the information flows for two-
way
interactions are grouped so that the information items closest to an arrowhead
flow in the direction of the arrowhead.
3.5.1 Operational Users
One of SPAWAR ;PD 51's important roles is to reduce the burden on Operational
Users for interpreting security policies, obtaining and operating secure
information systems, and acquiring life cycle support for security
capabilities. Figure 3 illustrates (using dotted lines) how SPAWAR ;PD 51
fulfills this role in the NIU through coordination of the interactions between
the Operational Users and the other INFOSEC-
related
organizations so that the Operational User has available one central point of
contact for all security-
relevant
issues and activities. The Operational User need interact directly only with
OPNAV, SPAWAR ;PD 51, and the information system.
The direct and indirect interactions (via SPAWAR PD 51) of Naval Operational
Users with other organizations in the INFOSEC Universe (summarized in Figure 3)
are the following:
- SPAWAR PD 51 coordinates the INFOSEC interactions of Operational
Users with other organizations in the NIU. It directly provides in-
service
engineering, life-
cycle
and implementation support for standalone and embedded INFOSEC products,
develops and procures INFOSEC products for the Fleet, and provides inputs to
operational documents. Operational Users provide feedback on the effectiveness
of INFOSEC attributes for their systems and may choose to request INFOSEC
support from SPAWAR PD 51 through their "800" number.
- SECNAV develops and disseminates INFOSEC policy.
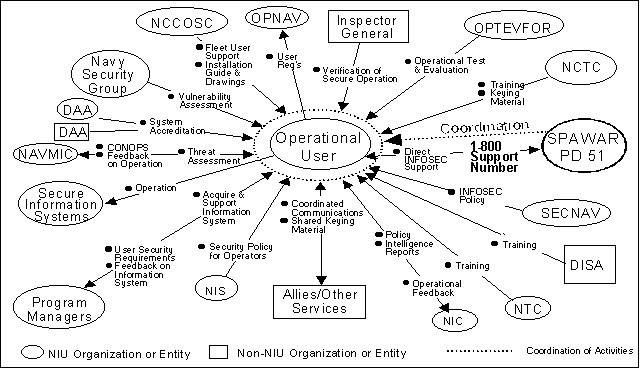
Figure 3. Principal Interactions of the Operational User in the INFOSEC
Universe
- DISA provides training materials and classes in INFOSEC awareness
and concepts for Operational Users.
- NTC provides INFOSEC training materials and curricula in INFOSEC
equipment maintenance and operations to Operational Users.
- NIC prepares tailored intelligence reports and policy for operation
of intelligence systems. The Operational User provides NIC feedback and
relevant operational information.
- Other Services/Allies share coordinated secure communications and
keying material with Operational Users.
- NIS sets, and monitors compliance with, security policies for
TEMPEST, physical, and personnel security measures.
- Program Managers (PMs) develop and procure secure information
systems for Operational Users. The Operational User provides the PM with
security requirements for new or improved information systems and feedback on
secure information system operation. (In some instances, PD 51 may be the
PM.)
- Secure Information Systems are operated and maintained by
Operational Users. Operational Users provide documentation such as user's
manuals and facility manuals.
- NAVMIC conducts threat assessments of operational information
systems and provides corrective information. The Operational User provides
operational concept documentation and operational feedback to NAVMIC.
- DAA accredits secure information systems for operation. The DAA
may be from the operational fleet, an OPR (e.g., SPAWAR, NSG, NCTC), or an
organization outside of the NIU (e.g., DIA, CIA, NSA).
- Naval Security Group assesses the vulnerability of operational
systems with respect to signals emissions and provides liaison with NSA when
NSA owns information handled by the operational system.
- NCCOSC provides system installations, upgrades, and repairs and
receives from the Operational Users trouble reports and feedback on secure
information system effectiveness. NESSEC (under NCCOSC) provides security and
certification testing of some operational systems.
- OPNAV receives operational requirements from Operational Users to
formulate Operational Requirements Documents (ORDs), Mission Need Statements
(MNSs), etc.
- The IG provides a report to the Operational User identifying
whether the operational system meets the security and operates correctly.
- OPTEVFOR provides operational T&E reports to Operational Users.
Testing may include operational INFOSEC features or assessing the effect of
INFOSEC on the system's operation.
- NCTC provides training and cryptographic keying material to
Operational Users to support security features.
3.5.2 Program Managers
Another of SPAWAR PD 51's roles is to assist Program Managers responsible for
developing new information systems with security requirements to effectively
integrate INFOSEC into their systems. Figure 4 illustrates that PD 51, as an
integral member of the PM's system engineering/integration team, interprets and
applies INFOSEC policies and doctrine, acquires and develops standard and
supportable products, integrates INFOSEC throughout the system's life cycle,
and interacts with DISA, NSA, and the Joint Service Community. This allows the
PM to focus on working with the Operational User and the DAA to develop a
secure, operational information system. SPAWAR PD ;51 uses its knowledge base,
on-
going
NIU interactions (described in Section 3.5.3), and lessons learned from related
efforts to accomplish the security engineering objectives. Program Managers of
information systems with INFOSEC requirements have the following direct and
indirect (via PD 51) interactions with the other organizations in the INFOSEC
Universe:
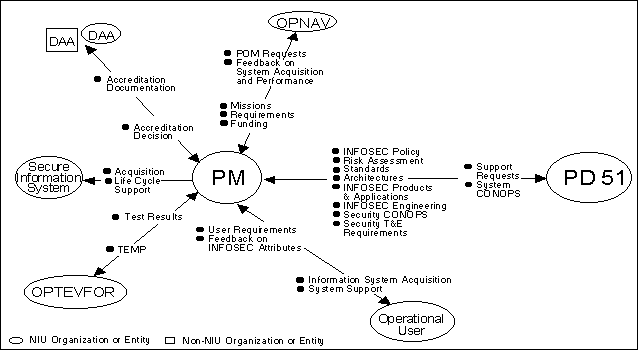
Figure 4. Principal Interactions of the Program Manager in the INFOSEC
Universe
-
-
- OPNAV provides the PM Naval mission definition, system requirements
and funding. The PM requests funding from OPNAV through the POM process and
provides feedback on acquisition and system performance.
- SPAWAR PD 51 as a member of the PM's system engineering team
provides and integrates INFOSEC policy, risk assessments, security standards
and architectures, INFOSEC engineering, security concepts of operation
(CONOPS), security T&E requirements, and certification and accreditation
support. To accomplish this, PD 51 interfaces with the organizations in the
INFOSEC Universe that are concerned with security policy, INFOSEC products,
applications, standards, architectures, and technology. PD ;51 develops and
procures standalone and embedded INFOSEC products for use by PMs. The PM
requests INFOSEC systems engineering support from PD ;51 and provides the
information system CONOPS to PD ;51.
- Operational Users provide feedback on system operation and on
requirements to the PM for new or improved information systems. The PM
provides the Operational User with the secure information system and its
support.
- OPTEVFOR performs T&E on the information system on the basis of
the Test and Evaluation Master Plan (TEMP) provided by the PM and provides the
results of the T&E to the PM.
- The Secure Information System is acquired and supported
throughout its life cycle by the PM.
- The DAA uses information supplied by the PM (Security CONOPS,
Security Policy, Security Accreditation Plan, certification results, etc.) to
make the accreditation decision. The DAA provides the accreditation decision
to the PM.
3.5.3 SPAWAR PD 51
This section describes the interactions of SPAWAR PD 51 with the NIU and the
broader INFOSEC Universe that support its roles described in the previous
sections and its long term role as the focal point for Naval INFOSEC. In this
latter role, SPAWAR ;PD 51 uses lessons learned from the operational community
and other PMs to coordinate and influence security policies, architectures,
standards, protocols, secure products and applications, technology R&D and
insertion efforts to ensure that Naval information systems possess the INFOSEC
attributes identified in Section 2.3. Figure 5 summarizes these
interactions.
- SECNAV provides Naval INFOSEC policy and guidance (prepared
for SECNAV's signature by NISMC) to SPAWAR PD 51. SPAWAR PD 51 provides SECNAV
feedback on Naval INFOSEC and lessons learned.
- OPNAV provides INFOSEC funding and the definition of Naval INFOSEC
missions and requirements to SPAWAR PD 51. In turn, SPAWAR ;PD 51 submits POM
requests to OPNAV for INFOSEC funding. PD ;51 also submits plans for product
solutions to OPNAV and identifies systems for support or development.
- DISA provides SPAWAR ;PD 51 Joint INFOSEC architectures and
standards for Joint INFOSEC interoperability and an approved products list.
SPAWAR ;PD 51 provides DISA information about Navy-
unique
INFOSEC requirements.
- The DAA may receive from SPAWAR PD 51, in supporting the PM, some
of the information required to accredit the system. SPAWAR ;PD 51 provides
guidance for system certification and accreditation (C&A) to the DAA. The
DAA provides lessons learned and operational considerations to SPAWAR PD ;51 to
ensure that INFOSEC C&A documentation is adequate.
- NRL provides technical INFOSEC studies and analyses, conducts
INFOSEC research, and develops INFOSEC prototypes for SPAWAR ;PD 51 and its
customers. SPAWAR ;PD 51 provides funding and tasking to NRL.
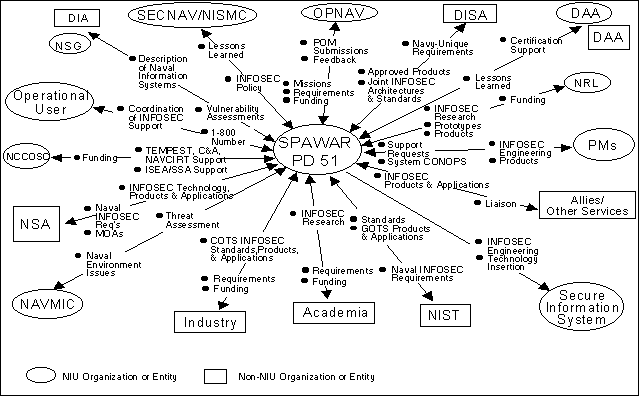
Figure 5. Principal Interactions of SPAWAR PD 51 in the INFOSEC Universe
-
-
- PMs request INFOSEC systems engineering support from SPAWAR ;PD 51
and provide the information system CONOPS to PD ;51. SPAWAR PD ;51, as a
member of the PM's systems engineering team, provides and integrates INFOSEC
policy, CONOPS, risk assessments, standards, architectures, technology
insertion, products, engineering, T&E requirements, and C&A support.
To do this, PD ;51 interfaces with organizations in the INFOSEC Universe that
are concerned with policy, products, applications, standards, architectures,
and technology. PD ;51 develops and procures standalone and embedded INFOSEC
products for use by the PMs.
- Allies/Other Services provide SPAWAR PD 51 INFOSEC products and
services for possible application to Naval INFOSEC systems. PD 51 provides
consultation and liaison to Other Services and Allies to foster INFOSEC
interoperability.
- The Secure Information System receives INFOSEC engineering and
technology from SPAWAR ;PD 51 either through the PM or with SPAWAR ;PD 51 as
the PM for some INFOSEC products and systems.
- NIST provides SPAWAR ;PD 51 INFOSEC standards, products, and
applications appropriate for the protection of unclassified but sensitive
information. SPAWAR ;PD 51 provides NIST information on Naval INFOSEC
requirements.
- Academia provides SPAWAR ;PD 51 the results of its research into
security systems and techniques. SPAWAR ;PD 51 provides academia information
about Naval INFOSEC requirements and support (e.g., funding) for its research
activities.
- Industry provides SPAWAR ;PD 51 COTS INFOSEC products and
applications for use in Naval systems. SPAWAR ;PD 51 provides industry
information about Naval INFOSEC requirements and support (e.g., funding) for
its development activities.
- NAVMIC provides National INFOSEC threat assessment results based on
Naval environmental issues from PD ;51 to guide SPAWAR ;PD 51 threat
assessments for specific systems. SPAWAR ;PD 51 also uses this information to
support its system planning and budgeting.
- NSA provides SPAWAR ;PD 51 INFOSEC technology, evaluated and
endorsed products, profiles, C&A strategies, and applications appropriate
for the protection of classified information. SPAWAR ;PD 51 provides NSA
information about Naval INFOSEC requirements. NSA and PD 51 establish
memorandums of agreement (MOAs) for NSA support to PD 51 and to other Navy
PMs.
- NCCOSC receives requests for In-
Service
Engineering Agent (ISEA) or Software Support Agent (SSA) activities from SPAWAR
;PD 51. NCCOSC provides this support for INFOSEC products developed or
procured by SPAWAR ;PD 51. NCCOSC (NESSEC) is funded and tasked to perform
TEMPEST, C&A, and Naval Computer Incident Response Team (NAVCIRT)
support.
- Operational Users provide feedback on the effectiveness of INFOSEC
attributes for their systems and may choose to request INFOSEC support from
SPAWAR PD ;51 through the "800" number. PD ;51 coordinates the INFOSEC
interactions of the Operational Users, provides in-service engineering,
life-cycle and implementation support for standalone and embedded INFOSEC
products, develops and procures INFOSEC products for the Fleet, and provides
inputs to operational documents.
- DIA provides vulnerability assessments of Naval intelligence
information systems to SPAWAR ;PD 51. SPAWAR ;PD 51 gives DIA information on
its information systems, missions, and scenarios as input to DIA's
vulnerability assessment process.
- NSG provides general Naval INFOSEC vulnerability results to guide
SPAWAR ;PD 51 INFOSEC engineering efforts. SPAWAR ;PD 51 also uses this
information to support its planning, programming, and budgeting.
GLOSSARY
-
-
- AIS
- automated information system
- APC
- armored personnel carrier
- ASN
- Assistant Secretary of the Navy
-
- C&A
- certification and accreditation
- C3I
- command, control, communication, and intelligence
- C4I
- command, control, communication, computers, and intelligence
- CIA
- Central Intelligence Agency
- CMS
- Cryptologic Materiel System
- COMINT
- communications intelligence
- COMPUSEC
- computer security
- COMSEC
- communications security
- CONOPS
- concept of operations
- COTS
- commercial-off-the-shelf
- CT&E
- certification test and evaluation
-
- DAA
- designated approval authority
- DIA
- Defense Intelligence Agency
- DISA
- Defense Information Systems Agency
- DoD
- Department of Defense
- DoN
- Department of the Navy
-
- EMSEC
- emissions security
-
- GOTS
- government-off-the-shelf
-
- HMMWV
- high mobility multi-
terrain
wheeled vehicle
-
- IED
- INFOSEC Engineering Division
- IFF
- identification friend or foe
- IG
- Inspector General
- IU
- INFOSEC Universe
- ILS
- integrated logistics support
- INFOSEC
- information systems security
- ISEA
- In-Service Engineering Activity
- IUDR
- INFOSEC Universe Description Report
-
- MCCR
- mission critical computer resources
- MNS
- Mission Need Statement
- MOA
- memorandum of agreement
- MSC
- Maritime Sealift Command
-
- NATO
- North Atlantic Treaty Organization
- NAVCIRT
- Naval Computer Incident Response Team
- NAVSECGRU
- Naval Security Group
- NAVMIC
- Naval Maritime Intelligence Command
- NCCOSC
- Naval Command, Control and Ocean Surveillance Center
- NCTC
- Naval Computer and Telecommunications Command
- NESSEC
- Naval Electronics System Security Engineering Center
- NIC
- Naval Intelligence Command
- NIS
- Naval Investigative Service Command
- NISE
- NCCOSC In-
Service
Engineering East
- NISMC
- Naval Information Systems Management Center
- NIST
- National Institute of Standards and Technology
- NIU
- Naval INFOSEC Universe
- NKDS
- Naval Key Distribution System
- NRaD
- Naval Research and Development
- NRL
- Naval Research Laboratory
- NSA
- National Security Agency
- NSG
- Naval Security Group
- NSTISSI
- National Security Telecommunications and Information Systems Security
Instruction
- NTC
- Naval Training Center
-
- ONI
- Office of Naval Intelligence
- OPNAV
- Office of the Chief of Naval Operations
- OPR
- Office of Primary Responsibility
- OPTEVFOR
- Operational Test and Evaluation Forces
- ORD
- Operational Requirements Document
- OSD
- Office of the Secretary of Defense
-
- PEO
- Program Executive Officer
- PM
- program manager
- POM
- Program Objectives Memorandum
-
- R&D
- research and development
- ROC
- Required Operational Capability
-
- SCI
- special compartmented information
- SECNAV
- Secretary of the Navy
- SFUG
- Security Features Users Guide
- SIGINT
- signals intelligence
- SPAWAR
- Space and Naval Warfare Systems Command
- SPAWAR 00I
- SPAWAR Information Systems Security Office (original title)
- SPAWAR PD 51
- SPAWAR Information Systems Security Office (new title)
- SPAWAR PD 51C
- SPAWAR Information Systems Security Office, Customer Service Division
- SPAWAR PD 51E
- SPAWAR Information Systems Security Office, Systems Engineering Division
- SPAWAR PD 51M
- SPAWAR Information Systems Security Office, Program Management Division
- SSA
- software support activity
- ST&E
- security test and evaluation
-
- T&E
- test and evaluation
- TEMP
- test and evaluation master plan
- TFM
- Trusted Facilities Manual
APPENDIX
SUMMARIES OF THE INTERACTIONS OF SPAWAR PD 51C, PD 51E, PD 51M AMONG THEMSELVES
AND WITH THE REST OF THE INFOSEC UNIVERSE
1. INFORMATION EXCHANGES AMONG 51E, 51C, AND 51M
The functions performed by each component of PD 51 complement the other
components' functions in an overall integrated process. The information
generated by each for use by the others is summarized in Table A 1 in the form
of a 3x3 matrix, each row and column being titled by a component. The matrix
diagonal in bold type contains the functions performed by each component. Each
row presents the information passed from the component in bold type to each of
the other components as identified in the title row. Each column, therefore,
identifies the information passed from each of the components identified in the
title column to the component in bold type.
2. INFORMATION EXCHANGES BETWEEN EACH OF 51E, 51C, 51M AND THE REST OF THE
INFOSEC UNIVERSE
Each component of PD 51 collects information from and provides information to
other organizations in the INFOSEC universe for use in performing its functions
and preparing responses to its customers' requests. These exchanges are
summarized in Table A 2, in which the first column identifies the external
organization, the second column the direction in which information is being
passed, the third column identifies the PD 51 component involved, and the last
column defines the data being passed.
TABLE A -1. SPAWAR PD 51: INTERNAL INFORMATION EXCHANGE
TO FROM E C M
E SYSTEM ENGINEERING ACTIVITIES Specific System Architectures Architecture Criteria For Product
Architecture Tech Base System Specific Security Standards Staff Or System Design Feasible, Mature
Engineering - Standards - Guide, SE. Document Templates Security Standards Acquisition
Process/Methods - Tools Design Guidance For Optimized Templates Security Engineering
Certification Process Engineering Processes and Methods Security
Methods (E.G., Risk Assessments, Engineering Tools Evidence Required
Requirements Analysis) Security For Certification Technology For
Engineering Tools Awareness Insertion Into Products Or Systems
Materials Guidance for Improved Guidance for Improved Product
System Engineering Processes Development Processes Guidance for
Improved Products For Development or
Acquisition
C System Security CONOPS and Issues LIAISON WITH CUSTOMER (Operational Customer-Specific System
System Engineering Constraints, User, Information System PM, Sponsor) Architectures And Constraints (e.g.,
Analysis of Interdependencies INFOSEC Engineering Support Cost, Schedule) INFOSEC Engineering
Customer-Specific INFOSEC Product Or Requirements Analysis And Guidance and Support Fleet Training
System Requirements C Feedback on Validation Certification And Materials for use by M Training for
System Engineering Methods, Tools, Recertification INFOSEC Awareness M (to Train Fleet)
Processes Customer Feedback on - Templates - Training -
Security Engineering Processes and Conferences - Publications
Solutions Fleet and Customer
Requirements via C - OPNAV
- User Conferences -
Customer-Defined/Derived Training
for E
M M Feedback on Process, Methods, INFOSEC Products, Systems PM FOR INFOSEC SYSTEMS/PRODUCTS
Tools Customer Feedback on Specific Awareness Materials Life Cycle System/Product Development
INFOSEC Products, Systems Support Materials, Documents System/Product Acquisition Life
(Architecture, Standards, Technology Cycle Support Materials And Documents
Base, COTS, GOTS)
Academia E R and D Results
Naval INFOSEC Requirements; Funding
Allies and Other C INFOSEC Products and Applications
Services
Coordination of Communications; Scheduling of Keying Material
DAA C System Accreditation; Lessons Learned
Accreditation Documentation; Certification Support
M (DAA Role when Assigned to PD51M)
DIA C Vulnerability Assessment of Naval Information Systems
Documentation of System Characteristics and Operations
E Vulnerability Assessment of Naval Information Systems
Naval Information Systems Descriptions
DISA C DOD Standards; Security Architectures; INFOSEC Awareness/Concepts Training; Approved
Products
Naval-unique Requirements
E Joint INFOSEC Architectures and Standards for Interoperability; Approved Products
Operational Users' Navy-unique INFOSEC Requirements
INDUSTRY C Systems Engineering; COTS Products and Applications for Systems Integration
INFOSEC Requirements; System Engineering Concepts; Funding
E R and D Results
Naval INFOSEC Requirements; R and D Funding for Technology and Concepts
M COTS Standalone Products and Systems; Development Plans and Budgets
Naval INFOSEC Requirements; Funding for Development
INFOSEC Products and C Operational Feedback
Systems
Developed, Tested, Verified, and Installed
E Operational Feedback
Developed, Tested, Verified, and Installed
M Operational Feedback
Developed, Tested, Verified, and Installed
Inspector General C Verification of Secure Operations of INFOSEC Systems and Products (when Integrated into
Information Systems)
M Verification of Secure Operations of Installed INFOSEC Products
NAVMIC C Threat Assessments (for INFOSEC System/Product Evaluation, and Technology Planning to
Counter Deficiencies)
Anticipated Naval Environment (Natural, Induced, and Manmade) in which Threat can exist
E Threat Assessments (for INFOSEC System/Product Evaluation, and Technology Planning to
Counter Deficiencies)
Anticipated Naval Environment (Natural, Induced, and Manmade) in which Threat can exist
M Threat Assessments as Guides for Specific Products
Naval Environment for Threat, Security CONOPS; Feedback on Operations
NAVSECGRU C Naval INFOSEC Vulnerability
Documentation of System Characteristics and Options
E Naval INFOSEC Vulnerability
NCCOSC M Fleet User Support; In-service S/EA and SSA PD51 Product Support; Installation Guides and
Drawings; TEMPEST and Operational System Security Testing, Certification and Accreditation,
NAVCIRT, all at NESSEC
ISSEA and SSA Requests; Trouble Reports; Feedback on INFOSEC Effectiveness
NCTC C Keying Material; Training
M Keying Material; Training
NIS C Security Policy for Operators
M Security Policy for Operators
NIST C INFOSEC Standards, GOTS Products, Applications
E INFOSEC Standards and Applications (for Product Technical Evaluation)
Naval INFOSEC Requirements
M INFOSEC Products and Applications
INFOSEC Product Requirements
NRL E INFOSEC Studies and Analyses, R and D, Prototypes
INFOSEC Research Goals and Plans; Tasking and Funding
NSA C INFOSEC Technology, Products, Standards, Policy, Doctrine; MOAs
MOAs with Program Managers and PD51
E INFOSEC Technology, Products, Profiles, Applications, C and A Strategies; MOAs
Operational Users' General INFOSEC Requirements; MOAs
NTC C Provides INFOSEC Product/Application Operation and Maintenance Training Curricula
Provides INFOSEC Product/Application Materials to Support Development of Curricula
Operational Users C "1-800" PD51C Contact for INFOSEC Engineering Support, INFOSEC Requirements and
Deficiencies; System Implementation; C and A
Responses to "1-800" Requests; Reports, Bulletins, etc.
E "1-800" PD51E Contact for INFOSEC Support,Technology and Systems Engineering Guidance,
Conference Participation; Operational Comments
Responses to "1-800" Requests; Reports, Bulletins, etc.
M "1-800" PD51M Contact for INFOSEC Product and Systems, Life-cycle Support, Implementation;
Feedback on INFOSEC Products and Systems
Responses to "1-800" Requests; Reports, Bulletins, etc.; INFOSEC Standalone Products and
Systems, Operational Documentation; In-Service Engineering Support; Security Policies for
Operators; DAA Activities; Keying Materials
OPNAV C Naval INFOSEC Requirements
Users' Requirements
E Naval INFOSEC Missions; Funding
POM Requests for Funding; Operational Mission Feedback
M
Users' Requirements
OPTEVFOR C OT&E Results
Documentation of System and its Operation, Installation and Operator Training
M OT and E Results
Documentation of Product/Application and its Operation, Installation and Operator Training
Program Managers C Review INFOSEC Needs for Acquired and Supported Information Systems with Defined System
CONOPS; Request INFOSEC Support, Participation in System Design Process and Reviews
Risk Assessments, Security CONOPS, T&E Requirements; INFOSEC Engineering Support, Product
and Technology Insertion, Architectural Considerations, Standards, C&A Support; Embedded
Product Guidance; Users' Security Requirements and Feedback
M Identify Needs for Products and Systems
Acquired and Supported Products, Systems, Associated Documentation; DAA Functions;
Feedback on Information System INFOSEC Performance; Users' Security Requirements
SECNAV &/or NISMC C INFOSEC Policy
Operational Feedback and Lessons Learned





