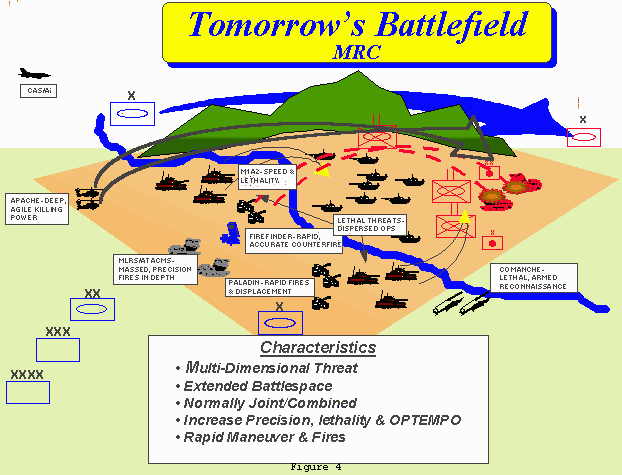

organizations the world has ever known. To mass the effects of these potent capabilities, future commanders must be able to:
b. Intel XXI is being developed to provide commanders a knowledge based, prediction oriented capability which can meet these demanding requirements. At the center of this concept are quality soldiers, leaders, and civilians. It represents a force that will produce for commanders a precise "in time" presentation of their battlespace that conveys an accurate understanding of the adversary, terrain, weather and operational environment. It will provide intelligence operators the resources necessary to coordinate and synchronize intelligence operations in concert with supported military operations. It will equip the force with tailorable, multi-spectral collection capabilities to deal with emerging capabilities and technologies. It will support operations on the move using broadcast and smart "push", and smart "pull" technologies. Finally Intel XXI will support lethal and non-lethal attack targeting and execution through the synchronization of deep information operations (IO) including command and control warfare (C2W), includes C2 Attack and C2 Protect.
c. In summary, the intelligence force of the 21st century - Intel XXI - is being designed, equipped, and trained to meet the demands of future operations and the needs of Force XXI commanders. It will be a flexible, tailorable, rapidly deployable, joint and coalition capable force. It will be a force that can access, leverage and integrate the complementary and unique specialized capabilities of the total intelligence force to include: national agencies, INSCOM strategic, operational and tactical units, active and reserve components, tactical organizations, and joint/multi-national forces. It will be an integral operational part of Force XXI.
2-2. Force XXI Decisive Operations
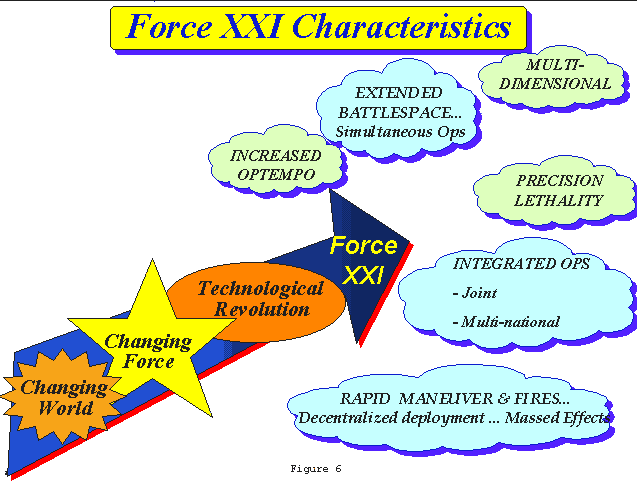
a. Force XXI Decisive Operations are characterized by simultaneous, multi-dimensional, non-linear operations over an extended battlespace conducted by integrated joint, multi-national forces operating dispersed in order to execute distributed operations through rapid maneuver and fires to achieve decisive effects. They are also characterized by significantly increased OPTEMPO, precision fires, lethality, and the need for force protection throughout all phases of the operation. (Figure 6)
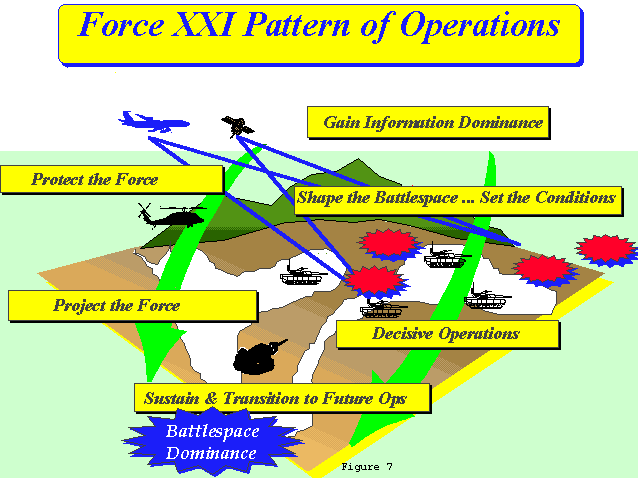
b. Within the context of this multi-dimensional high OPTEMPO environment, Force XXI Operations will be conducted through the following Pattern of Operations. They are not phased nor sequential, but apply throughout the continuum of operations from planning, to execution, to redeployment. (Figure 7)
a. Project The Force: (Figure 8)
(1) Force projection involves capabilities to tactically tailor METT-T driven force packages and the conduct of split based operations from CONUS to anywhere in the world. A major consideration for Force XXI operations is the participation of national, joint, operational, interagency, and multi-national intelligence capabilities. Intel XXI commanders, and their supported commanders, must be prepared to fully integrate and employ these critical assets. Intelligence XXI organizations and systems will have to be modular, scaleable, and flexible to meet the highly complex and often dynamically changing demands of future force projection operations. Strategic, operational, and tactical agility will be an essential characteristic of the Army's Intel XXI force.
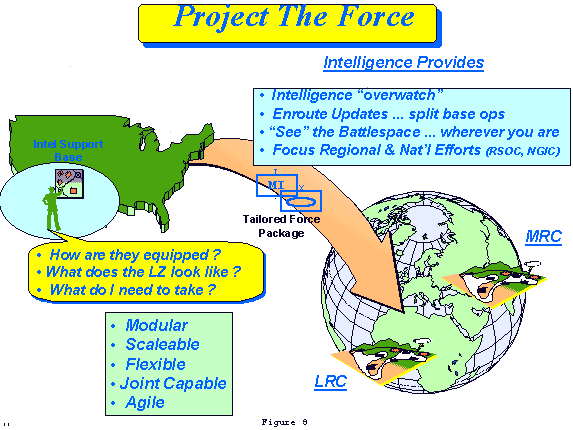
(2) Commanders, in future force projection operations, will have the capability to establish intelligence support bases (ISB) while flowing tailored intelligence force packages into the theater of operations. The ISB located in sanctuary, will provide intelligence to digitally linked deployed forces during all phases of the operation, including tailored intelligence products enroute, intel "overwatch" during initial deployment, and the ability to develop situational awareness and significant contributions to information dominance before arriving in theater. The ISB leverages and focuses national, joint and multi-national intelligence capabilities while the forward deploying intelligence units focus on staging, getting established, and building up in the theater.
(3) INSCOM forces in the 21st Century will play a vital role in force projection. Capabilities such as the Regional SIGINT Operations Centers (RSOC) and National Ground Intelligence Center (NGIC) will allow commanders to ramp up early by taking advantage of their regionally focused intelligence databases, products, and planning and training resources. INSCOM's Force Projection Brigades will provide re-enforcing complementary and frequently unique capabilities to deploying operational and tactical forces either forwarded deployed or from sanctuary. The INSCOM provided Corps Military Intelligence Support Elements (CMISE) will ensure a seamless bridge between the Corps, INSCOM and all echelons above INSCOM, including national and theater capabilities. In future operations it is clear that no one echelon can do it all, it will take a "total force" team effort, operating as a system of systems in a seamless architecture .
(4) The early entry Intel XXI force package may be as small as one person with a single channel tactical satellite communications terminal and a lap-top All Source Analysis System (ASAS) Remote Workstation (RWS) - a "mini-DISE". It may also be as large as a Intelligence Direct Support Company Team or Task Force with specialized augmentation teams from INSCOM or national agencies. It will be equipped with the capability to receive en-route updates on board aircraft or ship. Since commanders may be required to "fight" or operate immediately upon arrival, the deploying intelligence team may be equipped with capabilities to access in-theater joint and multi-national capabilities, support situational development and targeting, conduct counter-intelligence force protection operations, and perform limited C2W. Again, tailorability is the key to Intel XXI support to Force Projection operations.
b. Protect the Force: (Figure 9)
(1) The Army of the future will be vulnerable at every echelon throughout all phases of the operation to a wide range of threats from conventional fires and maneuver, to terrorists, to computer virus invasions...a mixture of lethal and non-lethal means. Threats will be multi-dimensional with potentially very precise and highly lethal capabilities. Force Protection must therefore involve the development of embedded technologies to protect against non-lethal attack of our C4I assets, as well as the operational employment of physical protective measures and C2W. Commanders of the future must be made cognizant of the full range of potential threats; prioritize their protect requirements in terms of key assets, critical nodes, and EEFI, and then be prepared to allocate resources accordingly.
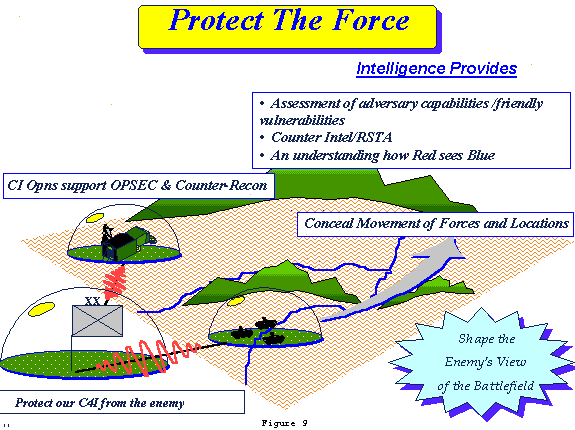
(2) In Force Protection, Intel XXI will focus on assessing friendly capabilities and vulnerabilities in relation to a thorough assessment of the adversary's attack, intelligence and RSTA capabilities. To provide commanders the information they need, the intelligence system will be able to dynamically portray how quot;red" sees "blue" so that cause and effect assessments can be made in wargaming. Using such reverse IPB "technologies", the commander can determine active and passive protect courses of action. Intelligence force protection activities will also focus on preventing surprise and conducting counter-reconnaissance and C2W to ensure that information dominance is achieved at the right time and place. Multi-discipline counterintelligence operations in support of force protection and operations security (OPSEC) must be thoroughly integrated into all phases of the operation.
c. Gain Information Dominance:(FIGURE 10)
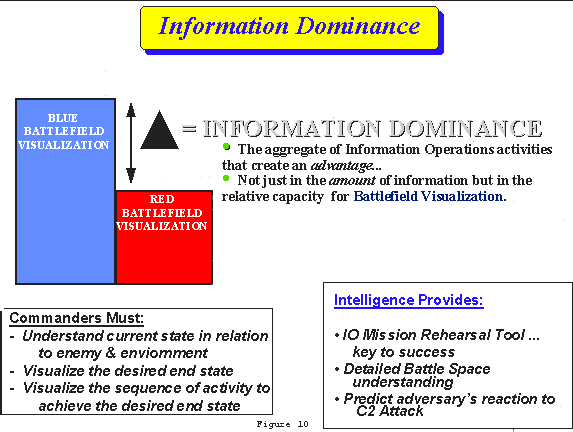
(1) Information Dominance is the delta between the understanding of information available to each of two opposing commanders. It is the aim of and achieved through the execution of information operations which include: the conduct of C2W, the establishment of a robust, secure information system (C4I) or "Infosphere" and the production of Battle Command information (intelligence, friendly force and other relevant information)n to enhance battlespace visualization and satisfy Commanders Critical Information Requirements (CCIR). To achieve information dominance commanders must protect their information systems, while destroying, degrading or de-coupling the adversary C4I/RSTA system, using a combination of lethal fires and increasingly sophisticated C2W non-lethal attack systems. Like a piston, information dominance can be up or down for a specific place and subject over time. It must be achieved at the right time and place for each specific operation.
(2) Intel XXI will play a critical role in achieving information dominance. Intelligence forces will collect, analyze present, and disseminate information on the weather, enemy and terrain and thus provide commanders the ability to visualize their battlespace. Like support to targeting, analysts will assess enemy C4I/RSTA capabilities and vulnerabilities in support of C2W target planning and execution. Intelligence operators will continue to plan, coordinate and synchronize the integrated employment of electronic warfare capabilities to include joint and multi-national. Intel XXI will thus allow commanders to more effectively mass the effects of both lethal and non-lethal means to achieve decisive results.
d. Shape The Battlespace:(FIGURE 12)
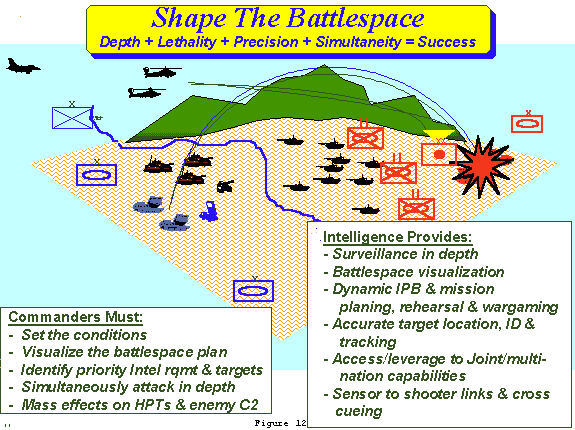
(1) Shaping the battlespace is the process whereby the commander sets the conditions for friendly success in decisive operations. To shape the battlespace, the commander must have a virtual, near-real-time continuous visualization of the battlespace in relation to the desired end state required for success. He must also be able to accurately locate, ID, track and then engage targets in depth with a variety of lethal and non-lethal means. He and his staff must wargame the various options and understand the impacts of both friendly and adversary actions, capabilities, intentions, and the environmental factors of weather and terrain. They must also coordinate the employment of joint and multi-national forces and capabilities.
(2) To shape the battlespace, the Warfighter must be supported by an intelligence force that can access deep collection assets (e.g. JSTARS, U2), precisely locate/track HPTs (e.g. UAV, GRCS), conduct C2W, and support the deep operations and targeting effort with dynamic, continuous and precise. Intel XXI must provide well trained intelligence analysts and operators supported by efficient and highly mobile precision sensors, processors, decision aids, and communications. It must be organized and equipped to integrate the intelligence and RSTA feeds from a variety of organic, joint and multi-national sensors. Finally, Intel XXI will include the capability to predict adversary actions, assess the terrain, and determine operational weather effects and their impact on friendly operations, allowing commanders and staffs to thoroughly wargame branches and sequels in varying conditions.
e. Decisive Operations: (FIGURE 13)
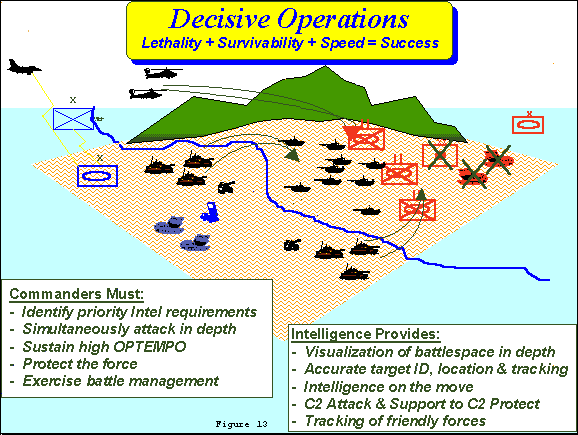
(1) Decisive operations will require an accurate view of the close-in battlespace. It demands coordinated, distributed and simultaneous operations designed to attack, disengage and re-attack. Accurate BDA will be required to ensure successful completion of each phase before moving on to the next. Rapid movement of friendly forces improves survivability and achieves mass at critical places and times for short periods.
(2) Decisive Operations demand the precise location and identification of fighting positions, combat vehicles, weapons, and obstacles. The density of such targets and the level of resolution will increase, while time to react decreases as formations close with one another. The intelligence force supporting decisive operations must be exceptionally agile and capable of providing a fine grain resolution of what surrounds the friendly commander. It must capable of not only collecting but communicating, processing and disseminating intelligence on the move. Intelligence forces will also provide commanders engaged in decisive operations with modular C2 Attack assets that support targeting and the massing of effects.
f. Sustain and Transition to Future Operations (FIGURE 14)
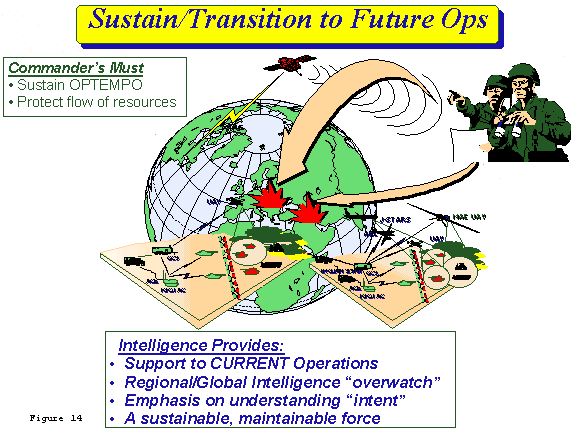
(1) Sustainment operations cross all patterns of operations and must be designed to help commanders sustain their OPTEMPO while transitioning from one phase to another. Maintaining and protecting the flow of sustaining resources will be achieved by an integrated combined arms effort.
(2) Intelligence operations will be continuous, designed to avoid surprise and protect forces. They will employ systems that can be maintained, re-supplied and re-deployed with the same speed and agility of their supported force. This will require an innovative approach to Intel XXI Combat Service Support (CSS). Intelligence operations also must keep the commander prepared for future operations. Intelligence elements must product IPB products, situation awareness, targeting data, collection request and plans for potential future operations
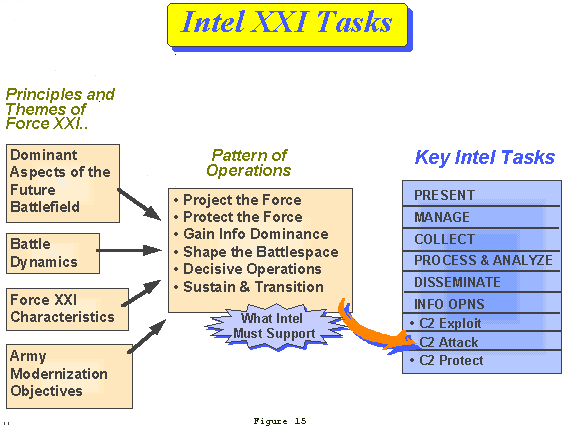
2-4. Intelligence XXI Tasks and Required Capabilities
The concept for INTEL XXI will be accomplished through the execution of the six (6) intelligence tasks shown in figure 15. The methodology for the development of INTEL XXI began with an analysis of Force XXI warfighter requirements. These requirements were derived form an analysis of TRADOC PAM 525-5, The Chief of Staff or the Army "Vision for the 21st Century", how to fight seminars, our current Army Modernization Objectives, and what it takes to provide Commander's the ability to conduct Force XXI Decisive Operations. Following is an overview of these tasks and a description of the kinds of required operational capabilities associated with each.
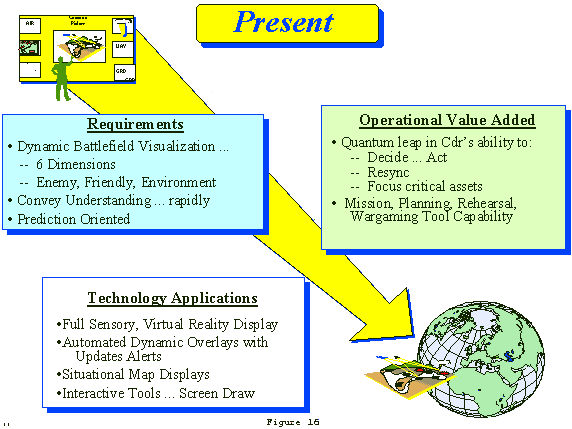
a. Present (FIGURE 16)
(1) "Present" encompasses the visionary aspects of the warfighter's knowledge-based, full sense perception of the battlespace, and the cognitive understanding of what the "presented" information means. The commander's knowledge based understanding of the battlespace and the enemy situation is fundamentally derived from a coherent and timely "picture" of the battlespace presented by the MI system. Additionally the commander's ability to anticipate difficult decisions, analyze options and reduce uncertainty when making those decisions is directly related to his intelligence staff's prediction of enemy actions and intentions in time and space; and the portrayal of those actions both during wargaming process, as well as during the rapid unfolding of combat operations, will provide virtual images to produce a dynamic yet coherent picture off the battlefield. In addition to displaying the current location, size, and type unit, the virtual display will graphically depict the current capabilities of an entity in terms of affects and ranges. The commander must understand the impact of what is being present and use that understanding to make knowledge-based decisions. By providing commanders a common understanding of their battlespace through the use of automated visualization tools, battlespace dominance can be achieved by Force XXI.
(2) The intelligence system must be able to create an accurate and relevant high fidelity virtual intelligence picture of the battlespace, integrate it with the overall situation, weather and high resolution terrain data and engineer the delivery of that picture to commanders wherever they are on the battlefield. This common picture must convey to the commander an immediate understanding of the operational impact of the current and projected situation so he can "see" his battlespace and make knowledge-based decisions. It is the beginning and the end of the intelligence cycle, and drives the requirements and capabilities associated with the other tasks. The production of this "presentation" is made by an organization of highly skilled, well trained intelligence soldiers who analyze the threat, weather and terrain within the context of the operational situation and the commander's requirements.
(3) Such a "presentation" of tomorrow's battlespace will evolve from today's map based overlays, graphic INTSUMs and textual reports to a full-sensory, digital virtual reality display that brings the battlespace to life. These "overlays" will be updated dynamically to add, change, and/or delete information and weather effects based on high resolutiondigital terrain and elevation data (DTED) in real time. They will include the use of scaleable flat panel, visual, graphic displays and full motion video of live, constructive, or virtual images with multiple overlay capabilities. Aural and visual cues, audio information and collaborative tools (John Madden white boards) will be used to dynamically convey, and coordinate the "presentation" of information and understanding. Automatic updates will alert the viewer as to what is being updated/changed based on pre-selected "alert criteria". "Presentation" technologies will support mission planning, wargaming, rehearsal, and operational execution.
(4) Future Intel XXI "Presentation" capabilities represent a quantum leap in a commander's ability to decide, act, resync operations and focus his resources. The true value added will be realized in sustained OPTEMPO, enhanced lethality and improved survivability.
b. Manage (FIGURE 17)
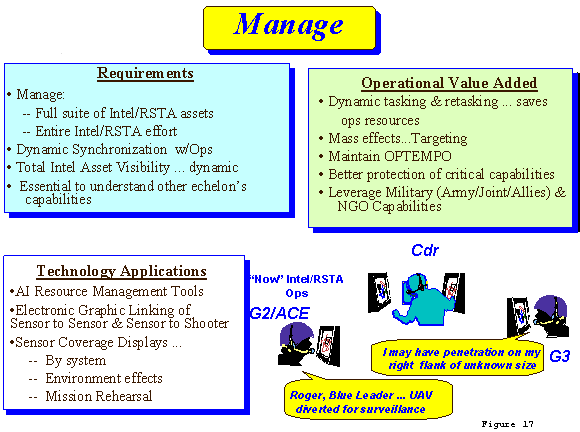
(1) In Force XXI, intelligence operators will be required to quot;manage" a full suite of intelligence and RSTA assets to include organic, joint, national and multi-national. Input from all battlefield sensors, manned and unmanned, must be managed and fused to provide a timely, accurate common picture of the battlespace. Consequently, Intelligence operations must go beyond traditional intelligence collection management activities and take into account the entire intelligence, reconnaissance, surveillance, and target acquisition domain. It is therefore imperative that the commander's senior intelligence officer be directly involved in the planning, coordination synchronization and direction of the entire intelligence and RSTA effort. Intel XXI operators must have visibility of the status and location of these assets horizontally and vertically so that efficient coordination and synchronization can be achieved.
(2) To effectively "manage" the intelligence and RSTA systems of the future, intelligence operators must be able to dynamically plan, coordinate, and synchronize the intelligence/RSTA mission using visual displays, artifical intelligence (AI) tools, and automated sync matrices. They must be able to see in real time the execution of intelligence/RSTA operations, i.e., an ability to watch what is or is not being "seen" by the sensors. They must also be able to see and execute sensor to sensor and sensor to shooter linkages. They must know how to hand off area and target coverage horizontally and vertically. With such capabilities, intelligence operators will be able to dynamically retask and shift the focus of intelligence/RSTA sensor coverage and thus more effectively locate and track critical targets.
(3) To dynamically "resync" operations, commanders must also have a real time view of the intelligence and RSTA operation as it is being executed. Such "now battle" displays for the commander must graphically present the intelligence and RSTA objectives as they are being "seen" and portray them in the context of the overall situation. With such capabilities, commanders in the future must be able to more effectively direct and influence intelligence/RSTA operations. They will be able to maintain OPTEMPO and mass effects on critical targets.
c. Collect (FIGURE 18)
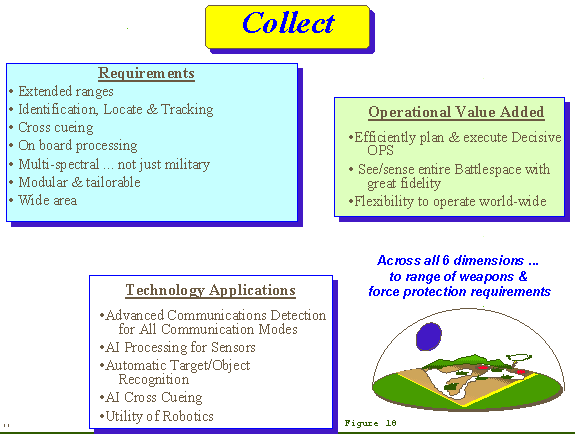
(1) Intel XXI collection systems will enable commanders to see and sense their extended battlespace with great fidelity. They will provide commanders the intelligence needed to understand the battlespace and locate, identify and track critical targets. The sensor inventory will include systems that can "see" and "sense", multi-spectral sensor equipped combat vehicles, aircraft (manned and unmanned), and soldiers - land, air, sea, and space.
(2) The trend in our future collection systems will be to fewer, more modular and tailorable systems. They will be automated, full spectrum, wide area and precision focus collectors. An open architecture design to include the Army Common Operating Environment will allow such systems to evolve with technology. Future systems must also provide multi-spectral sensing, cross-cueing, and on-board processing. Unmanned aerial and ground sensors, to include robotics and micro-electronic machines, will operate together to provide coverage in areas inaccessible to conventional collection means. Single platforms must be able to carry multiple types of sensor packages and support rapid reprogramming of smart and brilliant weapon systems.
(3) Future systems will be required to automatically detect, identify and locate all observables within the acoustic, visible and electromagnetic frequency spectrums. Advanced preprocessing technologies, to include techniques such as automated target (object) recognition (ATR), scene change detection, and target fingerprinting must be applied to sensors and processors to rapidly locate, identify and track critical targets. New sensor technologies for detection of advanced camouflage and concealment devices will also be required. Advanced, low density collection systems will be required to support specialized tailored collection operations. AI tools will be employed in support of HUMINT and open source collection operations.
(4) The ability to thoroughly see and sense the battlespace will allow warfighters to more efficiently plan and execute decisive operations. However, it will take the wide variety of sensors, described above to collect the data needed to help commanders to adequately visualize and understand their battlespace.
d. Process and Analyze (FIGURE 19)
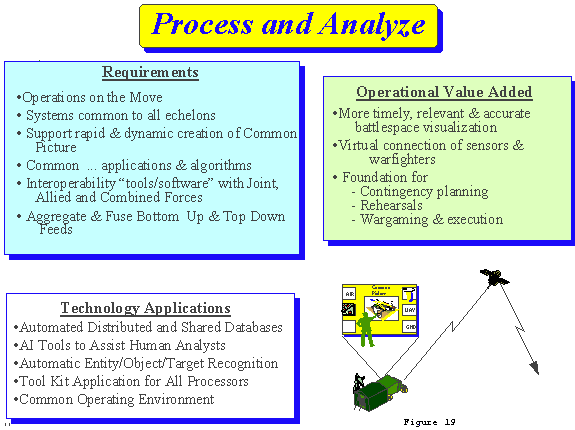
(1) Processing and analysis converts battlespace data and information into understanding and ultimately into effective decision making. As the extended battlespace grows and the speed of operations increases, Intel XXI must develop systems, common to all echelons, for the rapid processing, analysis, and throughput of intelligence and RSTA information, to include the aggregation and fusion of bottom-up with top down feeds at Brigade level. It must also support processing and analysis of intelligence while on the move.
(2) The ability to rapidly process and analyze data will demand a system that provides a virtual connection between collectors and warfighters, with efficient filtering to prevent information overload. It must facilitate distributed processing, analysis, and shared database access. Applications and algorithms must be standardized across systems and employ multi-level security at all echelons. Systems must optimize the use of a Common Operating Environment and common applications to support horizontal and vertical integration. Specific interoperability tools will be required to ensure rapid database and graphics translation/transfer with joint and multi-national forces.
(3) Future processing and analysis capabilities must support the rapid and dynamic creation of the commander's common picture. Analysts must be able to set automated alarms and use automatic routines for accessing distant databases. Artificial Intelligence tools are required to assist the analysts in adding meaning to the data being analyzed, provide automatic recognition of objects, entities, or targets and allow analysts to dynamically change the specific parameters or rule sets. In the end, the analysts must be able to make the enemy situation "come alive" so that commanders can quickly understand and act on what he sees.
(4) The Operational Value Added of such capabilities is more timely relevant and accurate battlefield visualization. It provides the commander the ability to understand threat force capabilities, vulnerabilities, and intentions in relation to the terrain, weather and operational situation. It turns information into understanding so that commanders can more effectively conduct decisive operations. It is the foundation for contingency planning, rehearsal, wargaming and execution, and therefore must support all phases of operations, peace and conflict.
e. Disseminate (FIGURE 20)
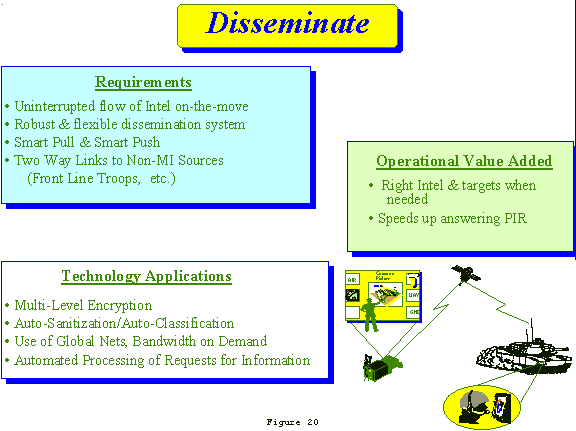
(1) Force dispersal and OPTEMPO requires that warfighters be provided an uninterrupted flow of intelligence on the move. As operational forces disperse and conduct distributed operations, a robust and flexible dissemination means becomes a critical requirement. Without it Intel XXI will not be able to provide the commander the necessary visualization of his battlespace. Technology will be required to support the automatic dissemination of intelligence at various levels of classification and handling instructions.
(2) Variations of the "Smart Push" - "Smart Pull" technologies will provide information required by warfighters and allow automatic updates based on established criteria. Automatic processing of "requests for information" will speed-up the process of answering commander PIR. If information is not immediately available, sub-tools will provide the requester the status of actions being taken in response to the request. Technologies will allow dispersed processors to be aware of available data without overburdening communications.
(3) Communications capabilities will expand to accommodate the dissemination of data to the MI System from non-MI sources such as tanks, fighting vehicles, remote unmanned sensors, scouts, attack/scout helicopters, and artillery acquisition systems. Dissemination requirements include bandwidth on demand, assured access, multilevel security access, wireless local area nets, and the ability to connect into global networks.
(4) Dissemination is a key element of the intelligence process and critical to understanding. No matter how much information is collected, processed, analyzed, and stored, intelligence is of no value unless it is available to combat commanders when they need it in a form they understand. The Operational Value Added of dissemination is the right intelligence and targets provided to warfighters when they need thereby increasing OPTEMPO and lethality and improving survivability.
f. Intelligence Support to Information Operations (FIGURE 21)
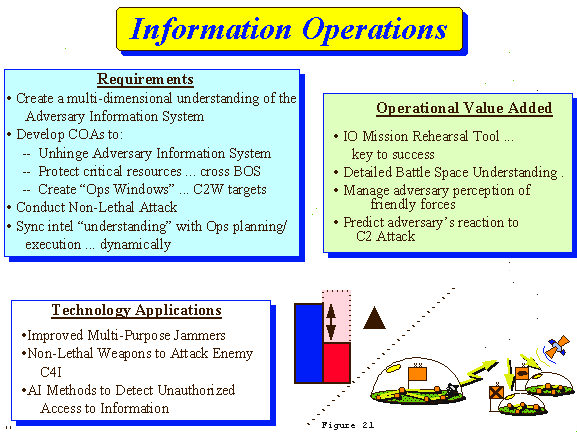
(1) Information dominance is gained when the commander's understanding of the Battlespace significantly exceeds that of the threat commander for a critical time and space. The commander will conduct information operations to achieve this information advantage. Intelligence support to Information Operations includes: enabling the understanding of how the adversary information system operates by identifying and locating his key nodes and points of failure (C2 Exploit); supporting lethal or non-lethal attack (C2 Attack) including BDA; and identifying and locating how the adversary information system operates to identify, locate and target friendly key nodes and failure points (C2 Protect).
(2) C2 Exploit
(a) Commanders require a thorough understanding of the adversary C2 structure and his decision making process to effectively attack it. Detailed analyses conducted in peacetime, and updated during the full spectrum of conflict will be the foundation of this understanding. Intelligence supports C2W through C2 exploit, focusing on the collection and maintenance of the database required to conduct C2 protect and C2 attack. A thorough understanding of the Military Information Environment (MIE) is the basis for developing and executing effective C2 attack actions to destroy, disrupt, deny, or degrade adversary information networks, C2 systems, information and intelligence sources, and decision processes. This understanding enables effective C2 protect actions to preclude the adversary from effectively conducting C2 attack against us. Understanding the adversary's decision process allows an accurate assessment of potential targets and supports effective information operations against critical nodes in synchronized, full dimensional attack. The requirement is to identify how the adversary commander will be affected by specific C2W actions, specific C2 high value target (HVT) and HPT, and predict his response when his decision process, information networks, or C2 systems are attacked.
(b) The same technologies required for other MI tasks must be used for C2 Exploit, though some new analytic and synthesis techniques that describe the adversary C2 and decision system will be required. IPB must provide the analytic tools needed for intelligence support to information operations. IPB must support wargaming, mission planning and mission rehearsal tools used to develop alternative C2W Courses of Action (COAs). These rehearsal tools will enable the commander to "think" beyond the traditional dimensions of width, height, depth, and time, and to determine the specific impacts information operations will have on the adversary decision making process. The dynamic wargaming capability must simulate adversary reactions to friendly C2W and depict threat C2 capabilities, decision process, and information collection capabilities.
(c) C2 Exploitation allows the warfighter to fully understand the adversary's intent and ability to command and control. Its Operational Value Added is providing a commander an accurate picture and visualization so that he can set condition, making full use of increased OPTEMPO and increased lethality to achieve his operational goal. The commander will now know when, where, and how to attack the adversary C2 system.
(3) C2 Attack
(a) C2 Attack includes both lethal and non-lethal means of influencing an adversary's decision process to prevent effective command and control by denying him information, degrading or destroying his C2 system, or providing him false or distorted information. The capability to thoroughly understand and graphically depict the information battlespace (C2 Exploit) is the fundamental basis for successful C2 attack operations. Sophisticated non-lethal attack options to deny, disrupt, distort or destroy information will be planned and executed by MI units as part of the commander's C2 attack strategy. Attack options may vary from surgical jamming of the frequency spectrum to intrusion into C2 systems to manipulate data. C2W BDA is essential in assessing the effects of C2 attack and maintaining information dominance. However, devising a means to conduct BDA on targets which have been non-lethally engaged poses significant challenges to future technical support required for intelligence staffs. Effective BDA is critical to the Intelligence Preparation of the Information Battlespace, and in updating current effectiveness ratings. The understanding of the threat information system, and the ability to predict his reactions, will be linked to AI assisted collection management and BDA tools. The C2 attack BDA process will require a probability and confidence matrix, based on AI algorithms using collection, attack executions, feedback reports, and analysis of how the adversary is reacting.
(b) The Operational Value Added of C2W Attack allows the friendly commander to render the opposition "headless". The threat will be unable to react in time to friendly increased OPTEMPO and lethality. Information dominance will allow friendly forces to manage adversary perceptions and execute deception operations simply by inserting data into the adversary C2I system, without moving a single asset. C2 Attack BDA provides the commander the measure of success so he can commit to decisive operations once the conditions he set are achieved.
(4) C2 Protect
(a) C2 Protect can be offensive or defensive in nature. Offensive C2 Protect uses the basic elements of C2 attack to reduce the adversary's ability to attack friendly Command and Control. Defensive C2 protect reduces friendly C2 vulnerabilities to adversary C2 attack by employment of adequate physical, and electronic protection. C2 Protect measures must be incorporated into Army systems as they are planned, designed and developed. Failure to do so will put our C2 system at risk. The capability to thoroughly understand and graphically depict the information battlespace is the fundamental basis for successful C2 protect operations. MI units will use the same analytical tools supporting C2 Exploit and Attack to conduct vulnerability assessments of friendly information system and provide recommendations for improving OPSEC and protecting friendly C2 systems. Tools are needed to aid in detecting unauthorized attempts to access information and to electronically track the intruder. Wargaming must show the effect adversary attacks on C2 could have on friendly courses of actions.
(b) Just as Theater Missile Defense provides the ability to reduce the effectiveness of threat theater missiles, the Operational Value Added of C2 Protect provides the defense against threat C2 attack. Maintaining the warfighter's ability to command and control his forces improves survivability and increases OPTEMPO.